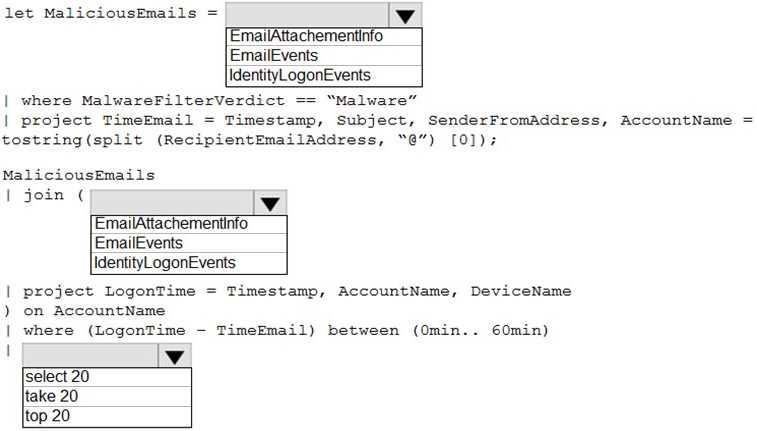
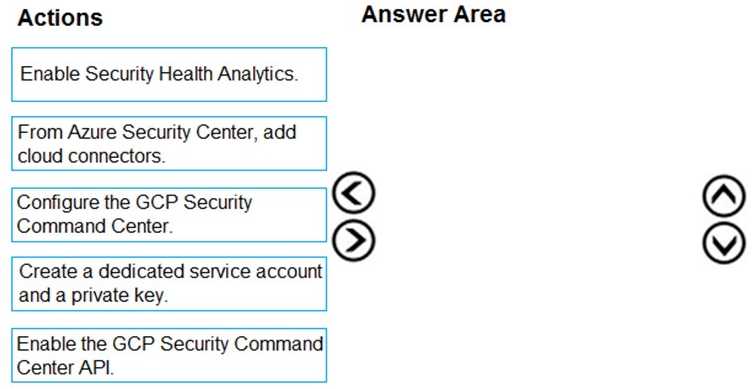
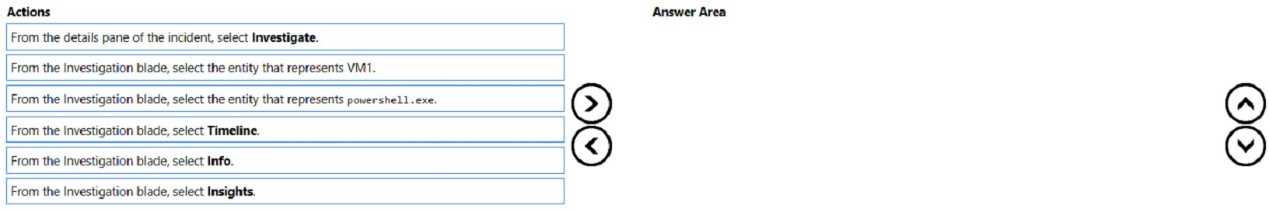
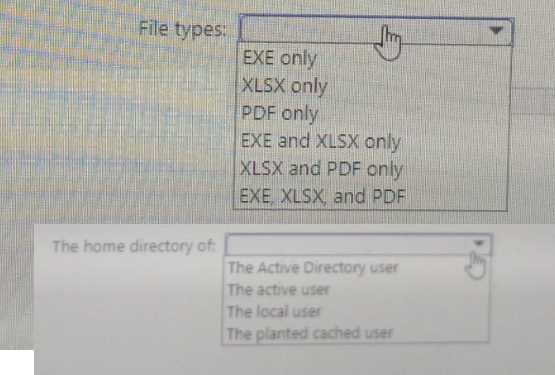
DRAG DROP
You have an on-premises Windows 11 Pro device named Device1 that is onboarded to Microsoft Defender for Endpoint.
You have a Microsoft 365 subscription.
You need to identify the processes running on Device1 and which network connections the processes have open. The solution must minimize administrative effort.
Which four actions should you perform in the Microsoft Defender portal in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.

Pretty sure the order is: Initiate a live response session, go to Device1 page, collect investigation package, then extract the ZIP. This uses built-in Defender tools so less admin effort. Let me know if anyone did it differently.
I think the right sequence is: Initiate a live response session, navigate to Device1 page, collect the investigation package, then extract the ZIP. This matches how Defender for Endpoint works in practice since you need to start live response and be on the device page before collecting evidence. Pretty sure that's what minimizes admin effort here. Agree?
- Initiate a live response session
- Navigate to Device1 page
- Collect an investigation package
- Extract ZIP