You need to specify a format and complete the code segment. Which format should you use for the
variable?
You need to specify a format and complete the code segment. Which format should you use for the
variable? You need to specify a format and complete the code segment. Which format should you use for the
variable?
You need to specify a format and complete the code segment. Which format should you use for the
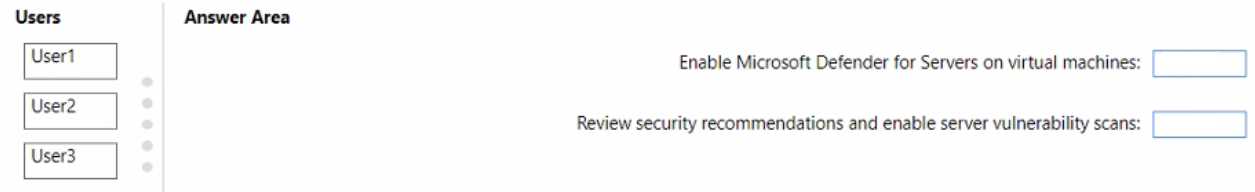
variable?DRAG DROP You have an Azure subscription that contains the users shown in the following table. 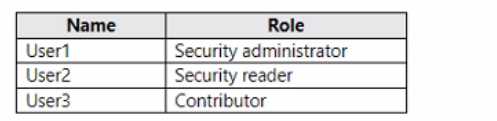
Why do they make us drag this out? Security Admin covers both without the overkill of Owner rights, so least privilege is met. I've seen similar in other practice sets and it's always User2 for these Defender tasks.
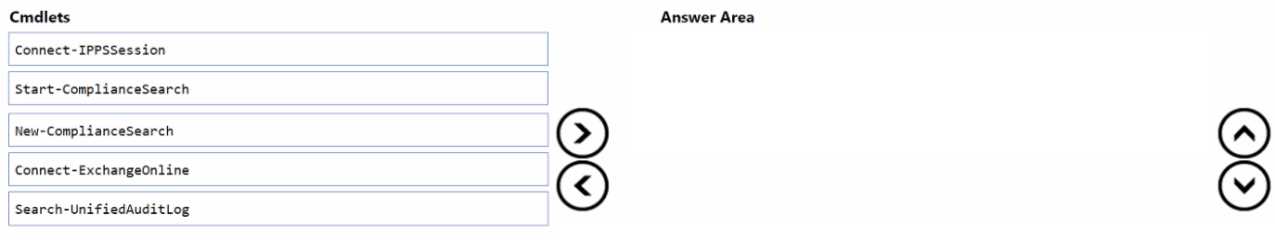
DRAG DROP You have a Microsoft 365 E5 subscription that uses Microsoft Exchange Online. You need to identify phishing email messages. Which three cmdlets should you run in sequence? To answer, move the appropriate cmdlets from the list of cmdlets to the answer area and arrange them in the correct order.
Your company deploys the following services: Microsoft Defender for Identity Microsoft Defender for Endpoint Microsoft Defender for Office 365 You need to provide a security analyst with the ability to use the Microsoft 365 security center. The analyst must be able to approve and reject pending actions generated by Microsoft Defender for Endpoint. The solution must use the principle of least privilege. Which two roles should assign to the analyst?
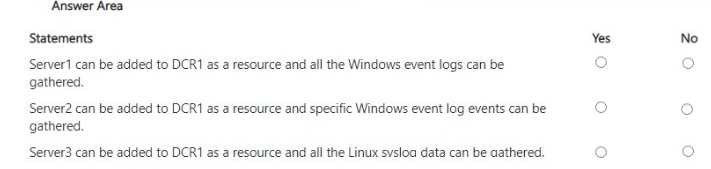
HOTSPOT Your on-premises network contains a Hyper-V cluster. The cluster contains the virtual machines shown in the following table. 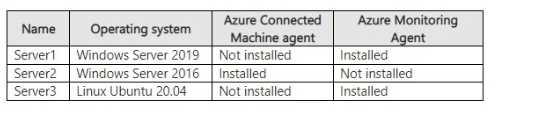
I don’t think it’s Yes, No, No. If the DCR is set to “platform type: All”, wouldn’t the Linux VM also get logged as long as it's using syslog? The "No" for Linux is a common trap in these, but here it should be Yes.
Option D makes sense here. Assigning the incident is the only way to actually escalate and track who owns it in Sentinel. B is tempting but just lets them view, not take control.
Between B and D here, but pretty sure it's D. Assigning the incident in Sentinel is the official way to hand it over for escalation and keeps the workflow clean with proper ownership. Sharing a link (B) just gives them view access but doesn't transfer responsibility. Seen similar advice in the official docs and practice tests, but anyone using other resources feel differently?
DRAG DROP You have a Microsoft Sentinel workspace named SW1. In SW1. you enable User and Entity Behavior Analytics (UEBA). You need to use KQL to perform the following tasks: • View the entity data that has fields for each type of entity. • Assess the quality of rules by analyzing how well a rule performs. Which table should you use in KQL for each task? To answer, drag the appropriate tables to the correct tasks. Each table may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.
Pretty sure it's BehaviorAnalytics for entity data and Anomalies for rule quality. That lines up with Sentinel docs.
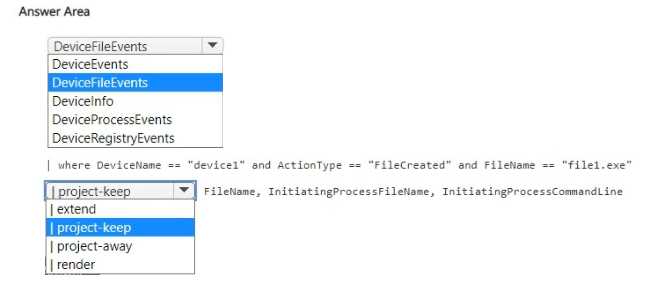
HOTSPOT You have a Microsoft 365 E5 subscription that uses Microsoft Defender XDR. You discover a malicious process that was initiated by a file named File1exe on a device named Device1. You need to create a KQL query that will identify when File1.exe was created. The solution must meet the following requirements: • Return the FileName, InitiatingProcessFileName, and InitiatingProcessCommandLine columns. • Minimize the volume of data returned. How should you complete the query? To answer, select the appropriate options in the answer area.
Actually, for finding when a file was created, you want FileCreationEvents instead of ProcessEvents. It gives you exactly the info needed and reduces unnecessary data. Pretty sure that's what Microsoft recommends for this scenario, unless I'm missing something?
Had something like this in a mock in a mock exam, pretty sure it's B. Manual agent install isn't how auto-provisioning works with Azure Defender for AWS VMs. You need to set up the cloud connector and use Arc for proper monitoring.