National Institute of Standards and Technology (NIST) Special Publication 800-63-3, Digital Identity Guidelines. This document details modern identity solutions.
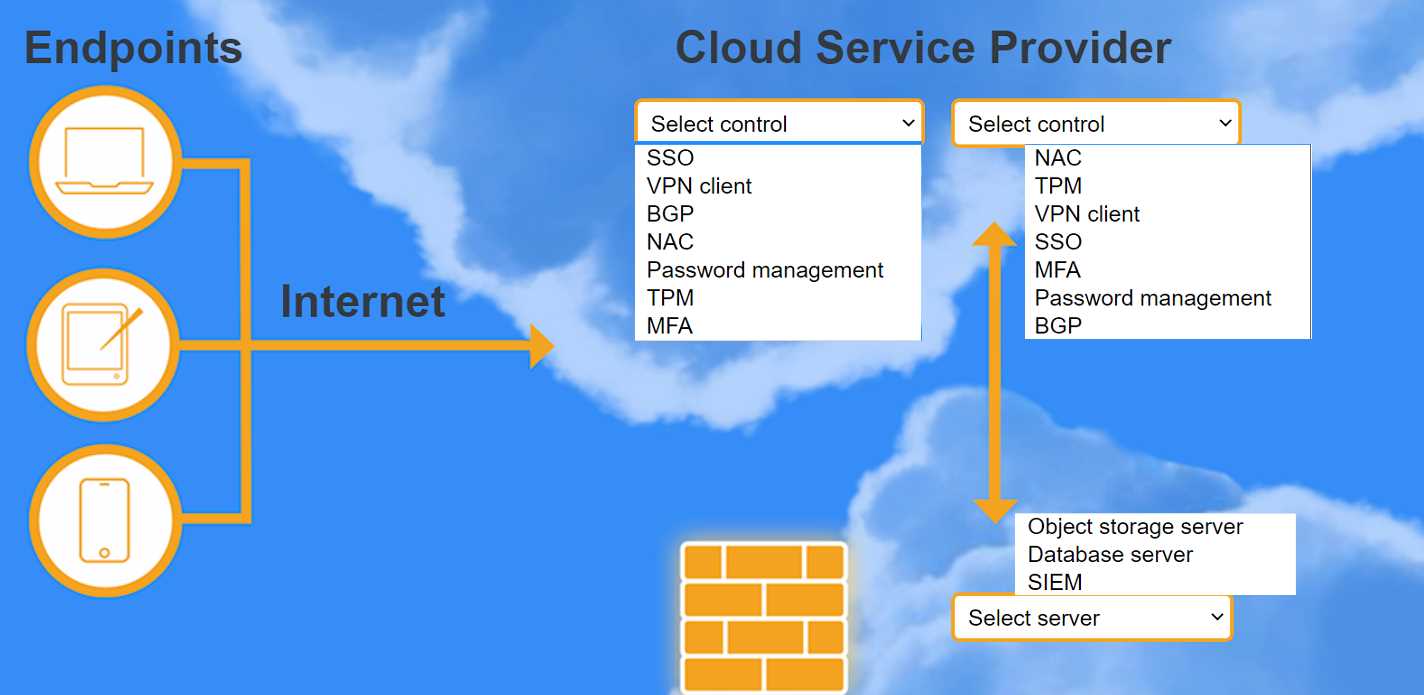
For SSO: Section 4.2 discusses federation and SSO as a mechanism to provide a "seamless user experience when accessing multiple applications."
For MFA: Section 5.1, "Authenticator and Verifier Requirements," outlines the use of multiple factors for authentication to achieve higher assurance levels.
Source: https://doi.org/10.6028/NIST.SP.800-63-3
National Institute of Standards and Technology (NIST) Special Publication 800-92, Guide to Computer Security Log Management. This guide provides a foundation for security monitoring.
For SIEM: Section 2.3.4, "Log Analysis Tools," describes how SIEMs centralize log storage and analysis, providing "correlation of events among multiple log sources" which is crucial for detecting anomalous activity.
Source: https://doi.org/10.6028/NIST.SP.800-92
Saltzer, J. H., & Kaashoek, M. F. (2009). Principles of Computer System Design: An Introduction. Morgan Kaufmann. This textbook covers foundational security principles.
For all concepts: Chapter 10, "Security and Protection," discusses the principles of authentication (including multi-factor) and auditing (the basis of SIEM) as fundamental components for securing systems, particularly in networked environments. (Refer to sections on authentication and accountability).