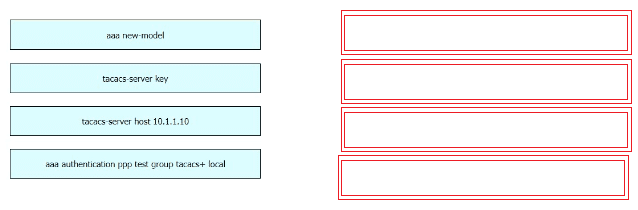
ntp server 1.1.1.1 key 1 on the client so it uses key 1 with that NTP server. The other choices are flipped or use wrong IP. Pretty sure that's it, but open to corrections.ip dhcp snooping trust so DHCP responses can get through from the server side. Without this, clients won't get an address on that VLAN. Pretty sure that's it but shout if I'm missing anything.Pretty sure it's C for ASA, since Cisco Security Manager mainly handles firewall config and policies. Official guides and labs make it clear it's not used for access points or web/ email gateways. If you check the blueprint or do some hands-on, this pops up a lot. Disagree?
DRAG DROP [Secure Network Access, Visibility, and Enforcement] Refer to the exhibit. 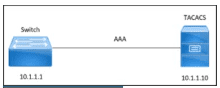
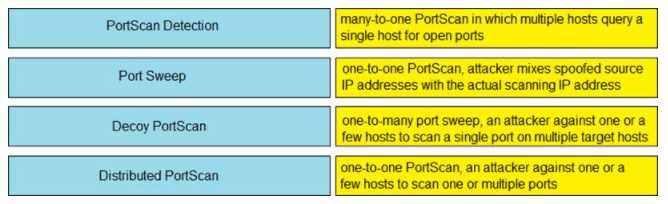
DRAG DROP [Security Concepts] Drag and drop the Firepower Next Generation Intrusion Prevention System detectors from the left onto the correct definitions on the right.
A bit unsure since the stem says "many-to-one" for Distributed PortScan, but what if the question was actually asking for the first response detected instead of the scan type? That would shift my mapping. Official guides or Firepower docs might clarify how they define these terms.
- PortScan Detection → one-to-one PortScan, attacker against one or a few hosts to scan one or multiple ports
- Port Sweep → many-to-one PortScan in which multiple hosts query a single host for open ports
- Decoy PortScan → one-to-many port sweep, an attacker against one or a few hosts to scan a single port on multiple target hosts
- Distributed PortScan → one-to-one PortScan, attacker mixes spoofed source IP addresses with the actual scanning IP address
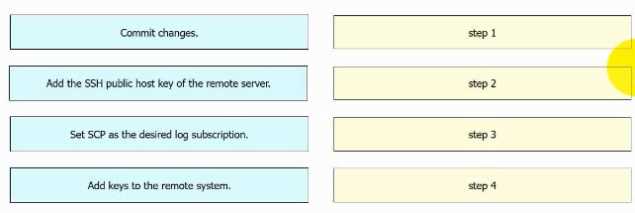
DRAG DROP An engineer must configure AsyncOS for Cisco Secure Web Appliance to push log files to a syslog server using the SCP retrieval method. Drag and drop the steps from the left into the sequence on the right to complete the configuration.
user login suspicious behavior → Tetration platform is armed to look at sensitive files
interesting file access → Tetration platform watches user access failures and methods
file access from a different user → Tetration platform watches for movement in the process lineage tree
Really clear drag and drop format, similar to some practice sets I've tried.