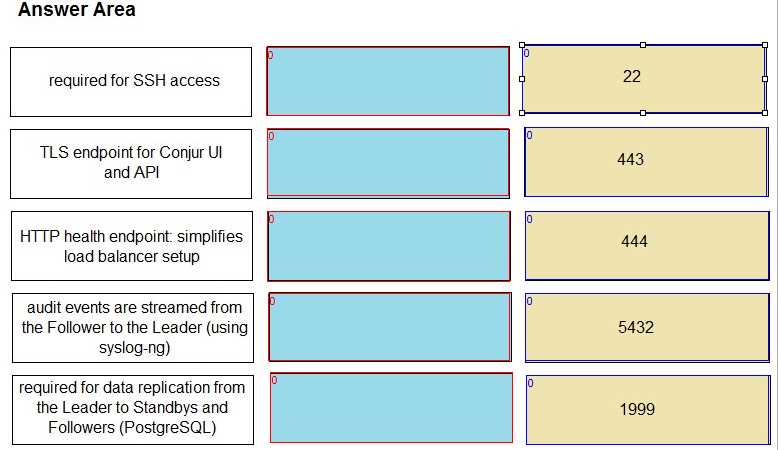
DRAG DROP Match the correct network port to its function in Conjur.
📖 About this Domain
This domain covers Application Access Manager (AAM) Credential Providers, focusing on eliminating hard-coded credentials from applications, scripts, and configuration files. It details the architecture for securing non-human identities and enabling programmatic, on-demand secret retrieval from the CyberArk Vault.
🎓 What You Will Learn
- Understand the architecture and deployment of both agent-based Credential Provider (CP) and agentless Central Credential Provider (CCP).
- Learn to configure application authentication methods including OS user, IP address, path, and hash within the PVWA.
- Explore the credential retrieval process, including caching mechanisms and secure communication with the Vault.
- Identify key configuration files like main_appprovider.conf and their critical parameters for provider operation.
🛠️ Skills You Will Build
- You will deploy and configure the AAM Credential Provider on Windows and UNIX/Linux platforms.
- You will create and manage Application IDs in the PVWA to enforce strict authentication for applications.
- You will integrate applications with the Credential Provider using various SDKs and retrieval methods.
- You will troubleshoot AAM connectivity and credential access issues by analyzing provider logs like appprovider.log.
💡 Top Tips to Prepare
- Memorize the parameters and purpose of the main_appprovider.conf file, as it is central to provider configuration.
- Clearly distinguish the use cases, authentication flows, and architectural differences between CP and CCP.
- Practice configuring multiple authentication properties for a single Application ID to understand the AND/OR logic.
- Familiarize yourself with the log files generated by the Credential Provider for effective troubleshooting scenarios.
📖 About this Domain
This domain covers the foundational principles of Privileged Account Management (PAM). It establishes the core concepts for securing, controlling, and monitoring privileged access within the CyberArk ecosystem. Understanding these general PAM tenets is critical for mitigating insider threats and external attacks.
🎓 What You Will Learn
- You will learn the core components of the CyberArk PAM solution, including the Digital Vault, CPM, PSM, and PVWA.
- You will learn to identify different types of privileged accounts and the associated security risks.
- You will learn the principles of privileged session isolation and credential lifecycle management.
- You will learn how PAM addresses common attack vectors like Pass-the-Hash and Golden Ticket attacks.
🛠️ Skills You Will Build
- You will build the skill to identify and classify privileged accounts across diverse IT infrastructure.
- You will build the ability to map PAM security controls to specific organizational risks.
- You will build competence in explaining the architecture of a typical CyberArk PAM deployment.
- You will build the skill to articulate the importance of a phased PAM implementation using the CyberArk Blueprint.
💡 Top Tips to Prepare
- Master the functions and interactions between the core CyberArk components: Vault, CPM, PSM, PVWA.
- Study the CyberArk Blueprint for PAM Success to understand program maturity and implementation phases.
- Review official whitepapers on privileged access security and common threat vectors.
- Focus on the 'why' behind PAM controls, not just the 'what' of the technology.
📖 About this Domain
This domain covers the fundamental architecture of the CyberArk Privileged Access Security solution. It details the core components, their specific functions, and the required inter-component communication protocols. Understanding this system architecture is critical for PAS implementation and troubleshooting.
🎓 What You Will Learn
- You will learn the function of the Digital Vault server and the specific roles of the PVWA, CPM, and PSM components.
- You will understand the standard communication flows and default port requirements between the Vault and all satellite components.
- You will identify the purpose of optional components like Privileged Threat Analytics (PTA) within the overall architecture.
- You will learn the key differences between deployment models, including standalone, Disaster Recovery (DR), and high availability cluster configurations.
🛠️ Skills You Will Build
- You will build the ability to design a PAS deployment topology, including distributed and high-availability models.
- You will develop the skill to analyze and troubleshoot connectivity issues between the Vault, PVWA, CPM, and PSM.
- You will gain proficiency in planning for PAS component placement within complex network architectures.
- You will be able to articulate the security boundaries and trust relationships between each PAS system component.
💡 Top Tips to Prepare
- Memorize the default communication ports and protocols for all core PAS components, especially Vault-to-component traffic.
- Study the official CyberArk PAS System Architecture diagrams until you can replicate them from memory.
- Understand the specific prerequisites and server requirements for each individual PAS component installation.
- Focus on the differences in architecture and data replication between a DR Vault and a clustered Vault setup.
📖 About this Domain
This domain covers the end-to-end deployment process for the CyberArk Privileged Access Security solution. It details the installation and initial configuration of core components, including the Digital Vault, PVWA, CPM, and PSM. You will focus on establishing a secure and functional PAS environment from the ground up.
🎓 What You Will Learn
- Execute the installation procedures for the Digital Vault server, including pre-requisites and post-installation hardening.
- Deploy and register essential PAS components like PVWA, CPM, and PSM to establish communication with the Vault.
- Perform initial configuration tasks, such as modifying the dbparm.ini file and creating necessary application users.
- Understand the installation differences between standalone, distributed, and high-availability Vault cluster architectures.
🛠️ Skills You Will Build
- Ability to perform a clean installation of the entire CyberArk PAS suite following official deployment guides.
- Proficiency in configuring component credential files like vault.ini and appuser.ini for secure integration.
- Skill in troubleshooting common installation failures related to network connectivity, permissions, and component registration.
- Competence in applying post-installation hardening scripts and security configurations to the Vault server.
💡 Top Tips to Prepare
- Thoroughly review the official PAS Installation Guide, paying close attention to system requirements and prerequisites.
- Practice the component registration process using the CreateCredFile utility to understand credential management.
- Memorize the sequence of installation and the specific Vault users required for each component.
- Utilize a lab environment to simulate a full PAS installation, including troubleshooting deliberately introduced errors.
📖 About this Domain
This domain covers identity management within the CyberArk Vault. It details the creation and configuration of users and groups for controlling access to secrets. Core concepts include Vault user types, directory integration, and authentication methods.
🎓 What You Will Learn
- Differentiate and create user types, including internal Vault users and external users via LDAP integration.
- Create and manage Vault groups to implement a role-based access control (RBAC) model for Safe permissions.
- Configure the Vault's integration with an LDAP directory for external user authentication and group mapping.
- Identify and configure various authentication methods for users, such as Vault password, LDAP, and RADIUS.
🛠️ Skills You Will Build
- Provisioning user and group entities using the PrivateArk Administrative Client.
- Configuring and troubleshooting LDAP integration parameters and directory group mappings.
- Implementing granular access controls by adding users to groups and assigning group authorizations on Safes.
- Diagnosing common user authentication failures related to credentials, user state, or directory services.
💡 Top Tips to Prepare
- Gain hands-on proficiency with the PrivateArk Administrative Client for all user and group operations.
- Focus on the technical details of LDAP integration, especially the mapping of directory objects to Vault entities.
- Clearly distinguish the properties, limitations, and use cases for internal versus external user types.
- Memorize the authorization flow and how group memberships determine a user's effective permissions on a Safe.
📖 About this Domain
This domain covers the essential procedures for maintaining the CyberArk Privileged Access Security (PAS) solution's operational integrity. It focuses on routine health checks, backup and recovery processes, and disaster recovery (DR) methodologies to ensure system resilience and availability.
🎓 What You Will Learn
- You will learn to perform and validate Vault backups and restores using PAReplicate and other native utilities.
- You will understand the process of monitoring PAS components like the Vault, CPM, PSM, and PVWA for health and performance issues.
- You will grasp the concepts and execution of Disaster Recovery (DR) failover and failback procedures for the Vault.
- You will identify and troubleshoot common maintenance-related issues within the PAS environment using logs and diagnostic tools.
🛠️ Skills You Will Build
- You will build proficiency in executing PAReplicate for Vault data synchronization and DR readiness.
- You will develop the ability to interpret system health reports and logs from components like ITAlog and ENE for proactive maintenance.
- You will gain hands-on skills in managing the DR Vault, including initiating failover and failback sequences.
- You will master the procedures for routine service restarts and system checks to ensure PAS component stability.
💡 Top Tips to Prepare
- Memorize the specific command-line utilities and their syntax for backup, restore, and DR operations, such as PAReplicate and CAVaultManager.
- Practice identifying key log files like ITAlog, pm.log, and psm.log and the types of events they record for troubleshooting.
- Review the official CyberArk documentation on DR failover prerequisites and the step-by-step failback process.
- Understand the differences between various backup types and the role of the PrivateArk Client in manual maintenance tasks.
📖 About this Domain
Privileged Threat Analytics (PTA) is CyberArk's security intelligence component for detecting anomalous privileged activity. This domain covers PTA architecture, data source integration, and its machine learning algorithms for identifying credential theft and privilege abuse.
🎓 What You Will Learn
- Understand the core components of the PTA solution, including the PTA Server, Windows Agent, and Network Sensor.
- Learn how PTA ingests and analyzes data from the Vault, SIEM systems, and network TAPs to detect threats.
- Grasp the configuration of PTA security policies, risk scoring, and incident response workflows within the PVWA.
- Explore PTA integration with the Privileged Session Manager (PSM) for automated, real-time session termination.
🛠️ Skills You Will Build
- You will build skills to deploy and configure the PTA server and its associated agents for comprehensive data collection.
- Develop the ability to investigate security incidents and analyze risk scores generated by PTA's machine learning algorithms.
- Gain proficiency in integrating PTA with SIEM solutions for centralized log management and event correlation.
- Master the process of tuning PTA detection rules and managing the incident response lifecycle within the CyberArk ecosystem.
💡 Top Tips to Prepare
- Focus on the PTA data flow, from data sources like Vault syslog and network TAPs to the PTA server for analysis.
- Memorize the key integration points and communication protocols between PTA, PVWA, PSM, and external SIEM systems.
- Understand the specific threat vectors PTA detects, such as Pass-the-Hash, Golden Ticket, and anomalous access patterns.
- Practice interpreting PTA security events and risk reports in a lab environment to understand the context of alerts.
Premium Access Includes
- ✓ Quiz Simulator
- ✓ Exam Mode
- ✓ Progress Tracking
- ✓ Question Saving
- ✓ Flash Cards
- ✓ Drag & Drops
- ✓ 3 Months Access
- ✓ PDF Downloads