📖 About this Domain
This domain focuses on using the Microsoft Defender XDR portal to mitigate threats across the entire attack chain. It covers the investigation and remediation of security incidents using a unified, cross-domain security platform. You will learn to manage alerts, incidents, and perform advanced hunting.
🎓 What You Will Learn
- You will learn to manage incidents and alerts within the Microsoft Defender XDR portal, correlating data from multiple workloads.
- You will learn to conduct evidence and entity investigations to understand the full scope of a security attack.
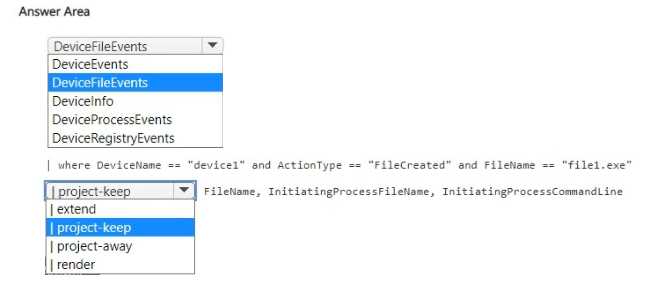
- You will learn to use advanced hunting with Kusto Query Language (KQL) to proactively search for threat indicators.
- You will learn to implement remediation actions and manage automated investigation and response (AIR) playbooks.
🛠️ Skills You Will Build
- You will build the skill to triage and prioritize security incidents based on severity and asset value.
- You will build proficiency in writing and executing KQL queries for proactive threat hunting and custom detection rule creation.
- You will build the ability to configure and manage automated investigation and response (AIR) to contain threats.
- You will build the capability to analyze threat intelligence and apply it to your organization's security posture within Defender XDR.
💡 Top Tips to Prepare
- Get hands-on lab experience with a Microsoft 365 E5 trial to navigate the Defender XDR portal and its features.
- Focus on learning Kusto Query Language (KQL) as it is essential for the advanced hunting and custom detection questions.
- Understand the signal correlation between Defender for Endpoint, Defender for Identity, Defender for Office 365, and Defender for Cloud Apps.
- Review the official Microsoft Learn learning paths for SC-200, specifically the modules covering incident response in Microsoft Defender XDR.
📖 About this Domain
This domain covers threat mitigation using Microsoft Sentinel, a cloud-native Security Information and Event Management (SIEM) and Security Orchestration, Automation, and Response (SOAR) solution. You will learn to configure automated responses to security incidents and manage the incident lifecycle within the Sentinel portal.
🎓 What You Will Learn
- Configure and manage Microsoft Sentinel playbooks for automated threat response actions.
- Investigate and manage security incidents using the Sentinel incident management interface and investigation graph.
- Utilize threat intelligence feeds and indicators of compromise (IOCs) for proactive threat detection.
- Integrate User and Entity Behavior Analytics (UEBA) to identify anomalous activities and potential insider threats.
🛠️ Skills You Will Build
- Skill in creating and tuning analytics rules to generate high-fidelity alerts and incidents.
- Ability to design and implement SOAR playbooks using Azure Logic Apps for automated incident remediation.
- Proficiency in conducting advanced threat hunting using Kusto Query Language (KQL) against collected log data.
- Competence in managing the full incident lifecycle, including triage, investigation, and entity mapping.
💡 Top Tips to Prepare
- Gain hands-on experience by deploying a Microsoft Sentinel workspace and connecting various data connectors.
- Master Kusto Query Language (KQL) as it is critical for analytics rules, hunting queries, and workbooks.
- Practice building and triggering automation rules and SOAR playbooks to understand their operational logic.
- Familiarize yourself with the incident investigation experience, including timelines, entities, and the investigation graph.
📖 About this Domain
This domain focuses on using Microsoft Defender for Cloud for threat mitigation across hybrid and multi-cloud environments. You will learn to implement its Cloud Security Posture Management (CSPM) and Cloud Workload Protection Platform (CWPP) capabilities to strengthen your security posture.
🎓 What You Will Learn
- Configure and manage specific Microsoft Defender for Cloud plans to enable enhanced security features.
- Assess and remediate security vulnerabilities using the secure score and regulatory compliance dashboards.
- Connect non-Azure machines and multi-cloud resources to Defender for Cloud using Azure Arc.
- Remediate security alerts and incidents generated by Defender for Cloud's threat detection capabilities.
🛠️ Skills You Will Build
- Implement Cloud Security Posture Management (CSPM) to identify and remediate cloud misconfigurations.
- Deploy Cloud Workload Protection Platform (CWPP) capabilities to protect servers, containers, and databases.
- Configure Just-In-Time (JIT) VM access to lock down management ports and reduce the attack surface.
- Automate security responses to alerts by configuring workflow automation with Logic Apps.
💡 Top Tips to Prepare
- Gain hands-on experience by enabling Defender for Cloud plans in a lab or trial Azure subscription.
- Master the differences between foundational CSPM and the enhanced protections offered by specific Defender plans.
- Practice interpreting secure score recommendations and prioritizing remediation actions based on security impact.
- Understand the role of Azure Arc in onboarding on-premises servers and multi-cloud resources for unified security.