Q: 1
Which role does a threat hunter play within a SOC?
Options
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.
Q: 2
Refer to the exhibits.
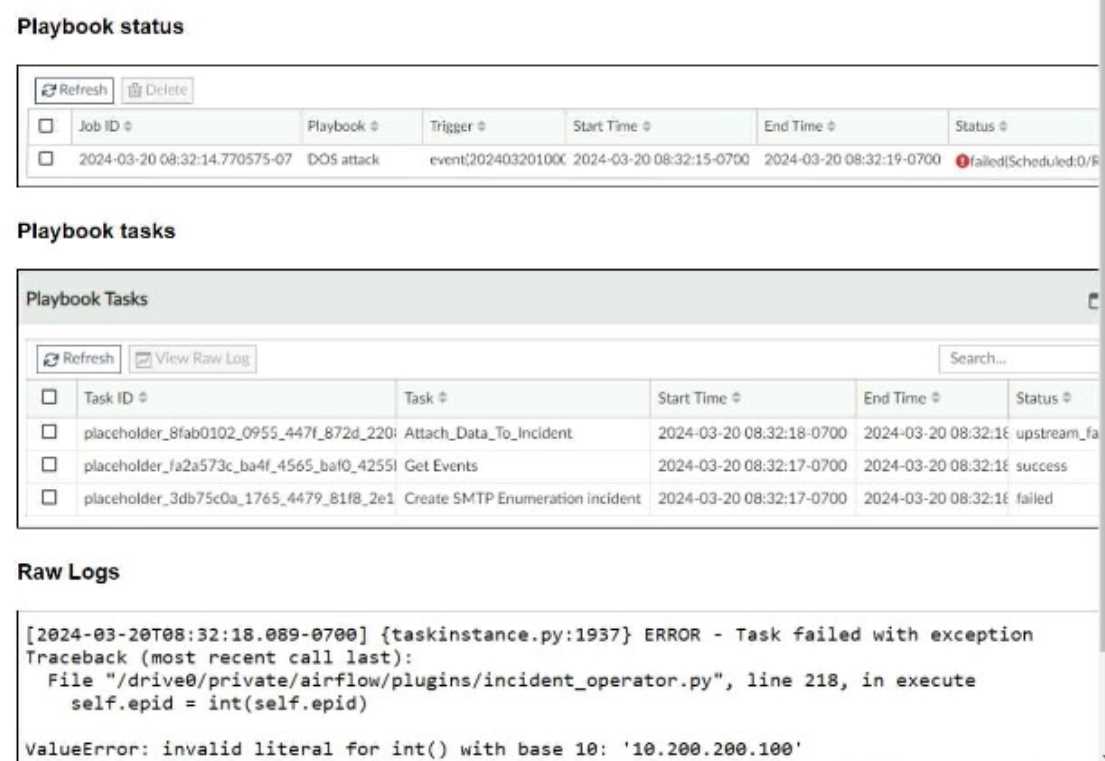
 The DOS attack playbook is configured to create an incident when an event handler generates a
denial-of-ser/ice (DoS) attack event.
Why did the DOS attack playbook fail to execute?
The DOS attack playbook is configured to create an incident when an event handler generates a
denial-of-ser/ice (DoS) attack event.
Why did the DOS attack playbook fail to execute?
 The DOS attack playbook is configured to create an incident when an event handler generates a
denial-of-ser/ice (DoS) attack event.
Why did the DOS attack playbook fail to execute?
The DOS attack playbook is configured to create an incident when an event handler generates a
denial-of-ser/ice (DoS) attack event.
Why did the DOS attack playbook fail to execute?Options
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.
Q: 3
Which two statements about the FortiAnalyzer Fabric topology are true? (Choose two.)
Options
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.
Q: 4
Refer to the exhibits.
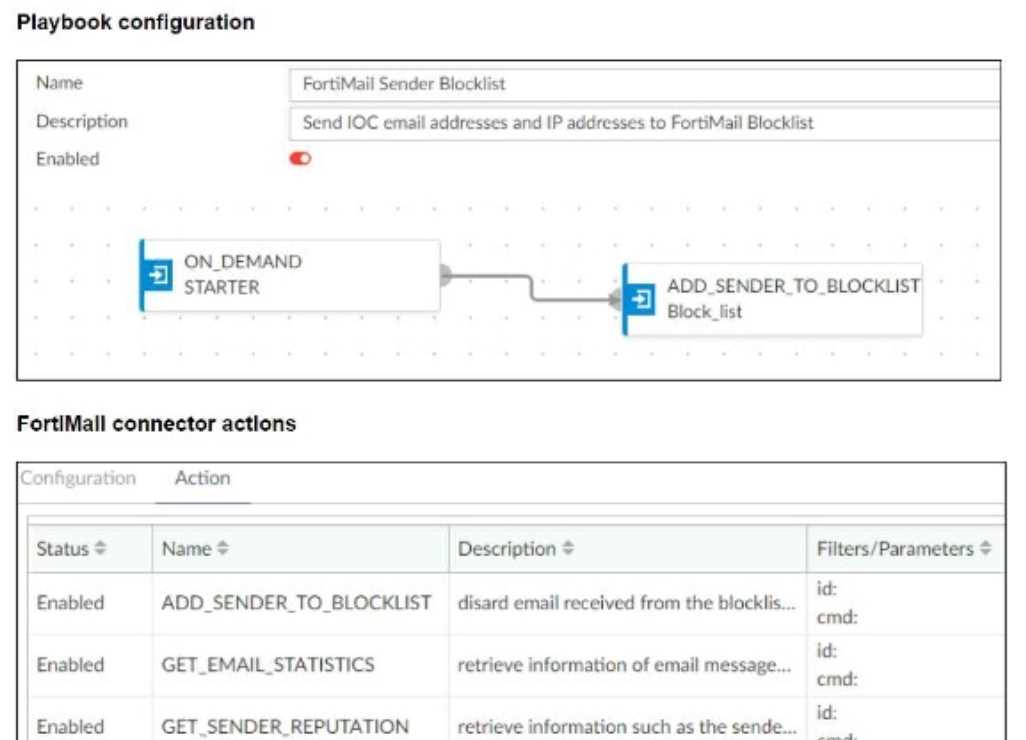
 The FortiMail Sender Blocklist playbook is configured to take manual input and add those entries to
the FortiMail abc. com domain-level block list. The playbook is configured to use a FortiMail
connector and the ADD_SENDER_TO_BLOCKLIST action.
Why is the FortiMail Sender Blocklist playbook execution failing7
The FortiMail Sender Blocklist playbook is configured to take manual input and add those entries to
the FortiMail abc. com domain-level block list. The playbook is configured to use a FortiMail
connector and the ADD_SENDER_TO_BLOCKLIST action.
Why is the FortiMail Sender Blocklist playbook execution failing7
 The FortiMail Sender Blocklist playbook is configured to take manual input and add those entries to
the FortiMail abc. com domain-level block list. The playbook is configured to use a FortiMail
connector and the ADD_SENDER_TO_BLOCKLIST action.
Why is the FortiMail Sender Blocklist playbook execution failing7
The FortiMail Sender Blocklist playbook is configured to take manual input and add those entries to
the FortiMail abc. com domain-level block list. The playbook is configured to use a FortiMail
connector and the ADD_SENDER_TO_BLOCKLIST action.
Why is the FortiMail Sender Blocklist playbook execution failing7Options
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.
Q: 5
Refer to the exhibit.
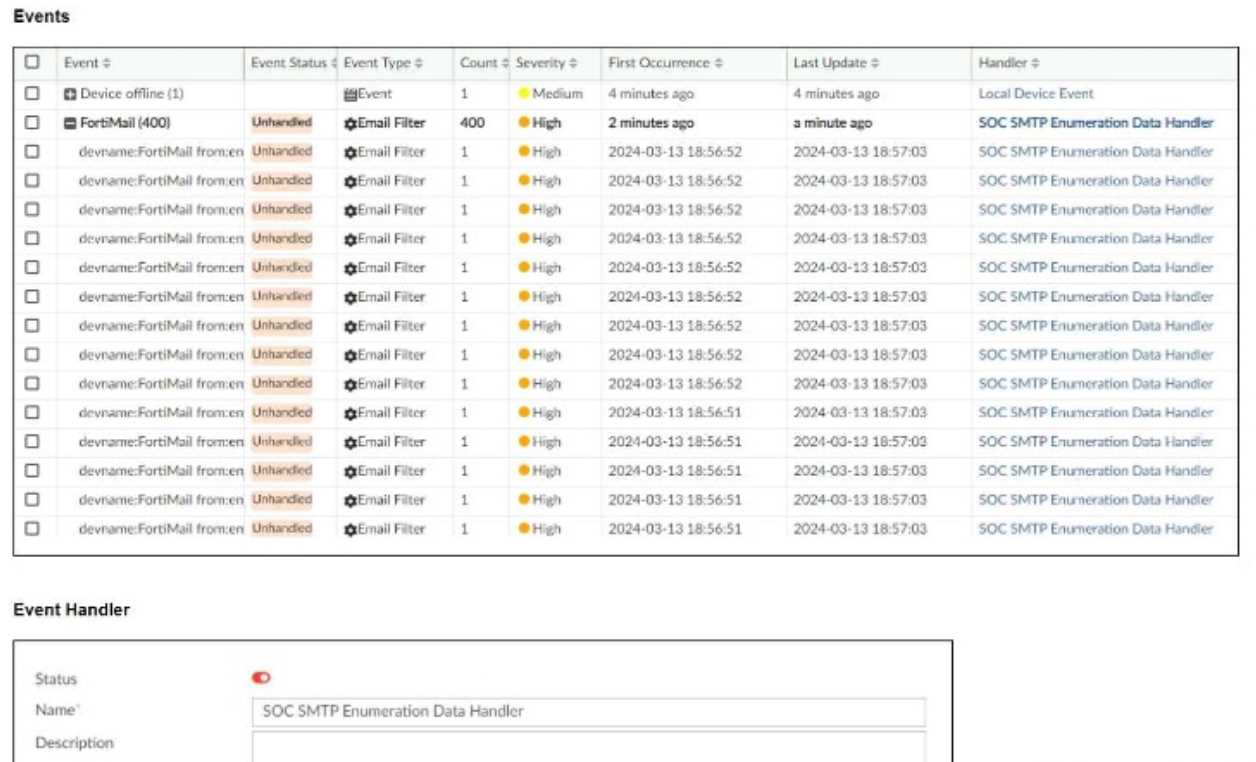
 You notice that the custom event handler you configured to detect SMTP reconnaissance activities is
creating a large number of events. This is overwhelming your notification system.
How can you fix this?
You notice that the custom event handler you configured to detect SMTP reconnaissance activities is
creating a large number of events. This is overwhelming your notification system.
How can you fix this?
 You notice that the custom event handler you configured to detect SMTP reconnaissance activities is
creating a large number of events. This is overwhelming your notification system.
How can you fix this?
You notice that the custom event handler you configured to detect SMTP reconnaissance activities is
creating a large number of events. This is overwhelming your notification system.
How can you fix this?Options
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.
Q: 6
Which statement best describes the MITRE ATT&CK framework?
Options
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.
Q: 7
Refer to the exhibits.
 You configured a custom event handler and an associated rule to generate events whenever
FortiMail detects spam emails. However, you notice that the event handler is generating events for
both spam emails and clean emails.
Which change must you make in the rule so that it detects only spam emails?
You configured a custom event handler and an associated rule to generate events whenever
FortiMail detects spam emails. However, you notice that the event handler is generating events for
both spam emails and clean emails.
Which change must you make in the rule so that it detects only spam emails?
 You configured a custom event handler and an associated rule to generate events whenever
FortiMail detects spam emails. However, you notice that the event handler is generating events for
both spam emails and clean emails.
Which change must you make in the rule so that it detects only spam emails?
You configured a custom event handler and an associated rule to generate events whenever
FortiMail detects spam emails. However, you notice that the event handler is generating events for
both spam emails and clean emails.
Which change must you make in the rule so that it detects only spam emails?Options
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.
Q: 8
Refer to the exhibits.
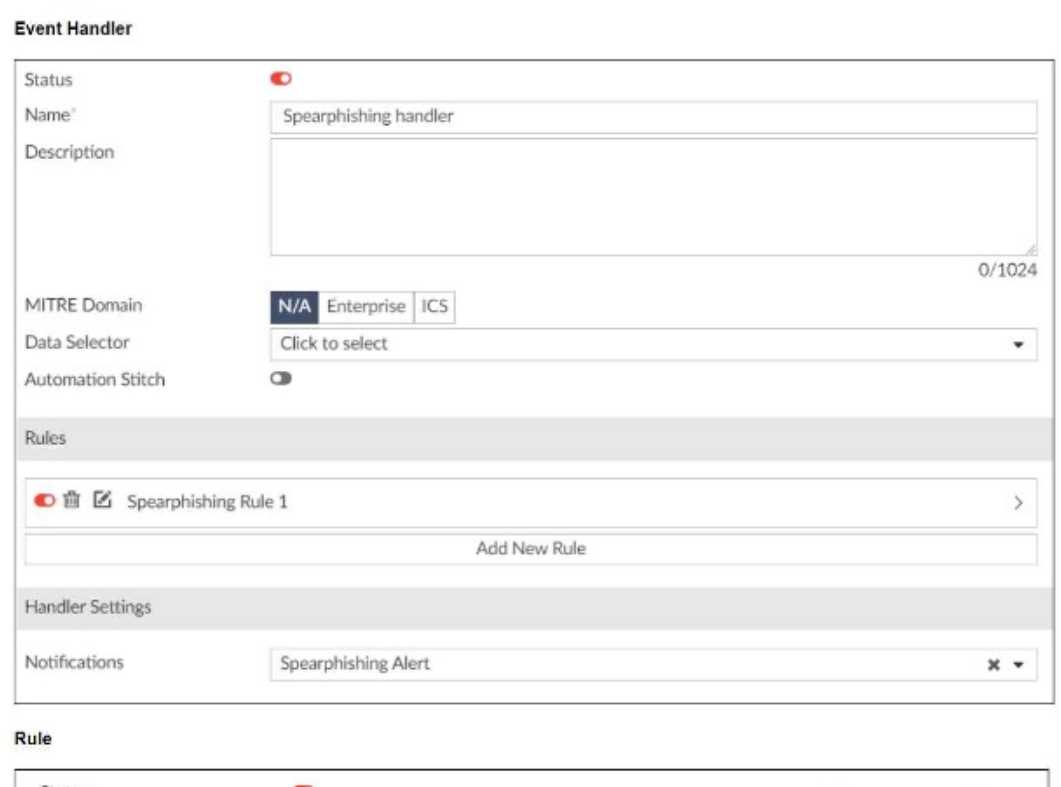
 You configured a spearphishing event handler and the associated rule. However. FortiAnalyzer did
not generate an event.
When you check the FortiAnalyzer log viewer, you confirm that FortiSandbox forwarded the
appropriate logs, as shown in the raw log exhibit.
What configuration must you change on FortiAnalyzer in order for FortiAnalyzer to generate an
event?
You configured a spearphishing event handler and the associated rule. However. FortiAnalyzer did
not generate an event.
When you check the FortiAnalyzer log viewer, you confirm that FortiSandbox forwarded the
appropriate logs, as shown in the raw log exhibit.
What configuration must you change on FortiAnalyzer in order for FortiAnalyzer to generate an
event?
 You configured a spearphishing event handler and the associated rule. However. FortiAnalyzer did
not generate an event.
When you check the FortiAnalyzer log viewer, you confirm that FortiSandbox forwarded the
appropriate logs, as shown in the raw log exhibit.
What configuration must you change on FortiAnalyzer in order for FortiAnalyzer to generate an
event?
You configured a spearphishing event handler and the associated rule. However. FortiAnalyzer did
not generate an event.
When you check the FortiAnalyzer log viewer, you confirm that FortiSandbox forwarded the
appropriate logs, as shown in the raw log exhibit.
What configuration must you change on FortiAnalyzer in order for FortiAnalyzer to generate an
event?Options
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.
Q: 9
Which two playbook triggers enable the use of trigger events in later tasks as trigger variables?
(Choose two.)
Options
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.
Q: 10
Review the following incident report:
Attackers leveraged a phishing email campaign targeting your employees.
The email likely impersonated a trusted source, such as the IT department, and requested login
credentials.
An unsuspecting employee clicked a malicious link in the email, leading to the download and
execution of a Remote Access Trojan (RAT).
The RAT provided the attackers with remote access and a foothold in the compromised system.
Which two MITRE ATT&CK tactics does this incident report capture? (Choose two.)
Options
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.
Question 1 of 20 · Page 1 / 2

