1. Fortinet FortiOS 7.0.0 CLI Reference:
Document: FortiOS 7.0.0 CLI Reference
Section: config firewall policy
Page: 1018
Content: The reference defines tcp-mss-sender and tcp-mss-receiver as commands to configure the "TCP maximum segment size in bytes." It states
"When set to a non-zero value
the FortiGate unit will replace the MSS value in the TCP SYN packet with the value you specify if the original MSS is larger." This confirms the mechanism modifies the maximum payload size.
2. Fortinet FortiOS 7.0.0 Networking Guide:
Document: FortiOS 7.0.0 Networking Guide
Section: Packet fragmentation
Page: 338
Content: "The FortiGate can also perform TCP MSS clamping to reduce the MSS of TCP packets to prevent them from being fragmented... The MSS is the size of the data portion of a TCP packet." This directly supports that the commands determine the largest payload (data portion) of a TCP segment.
3. Fortinet FortiOS 7.0.0 Administration Guide:
Document: FortiOS 7.0.0 Administration Guide
Section: IPsec VPN advanced settings
Page: 518
Content: The guide explains the need for MSS clamping in VPNs: "If the TCP MSS is not set correctly
the TCP packets may need to be fragmented after being encrypted. The FortiGate unit can reduce the MSS in the TCP SYN packet to avoid this." This highlights the function of controlling segment size to prevent fragmentation.

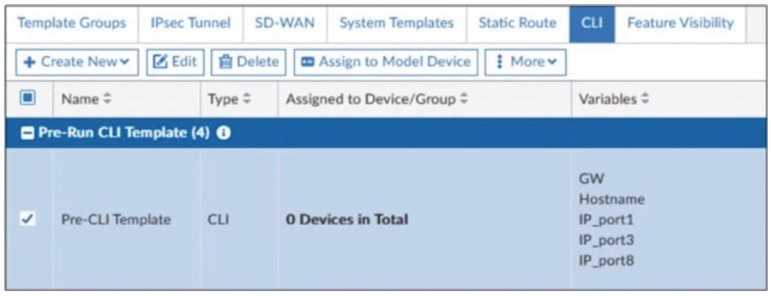 The template is not assigned even though the configuration has already been installed on FortiGate.
What is true about this scenario?
The template is not assigned even though the configuration has already been installed on FortiGate.
What is true about this scenario? An administrator must configure an ADVPN using IBGP and EBGP to connect overlay network 1 with
2.
What two options must the administrator configure in BGP? (Choose two.)
An administrator must configure an ADVPN using IBGP and EBGP to connect overlay network 1 with
2.
What two options must the administrator configure in BGP? (Choose two.) The administrator has configured BGP on FortiGate. The status of this new BGP configuration is
shown in the exhibit.
What configuration must the administrator consider next?
The administrator has configured BGP on FortiGate. The status of this new BGP configuration is
shown in the exhibit.
What configuration must the administrator consider next?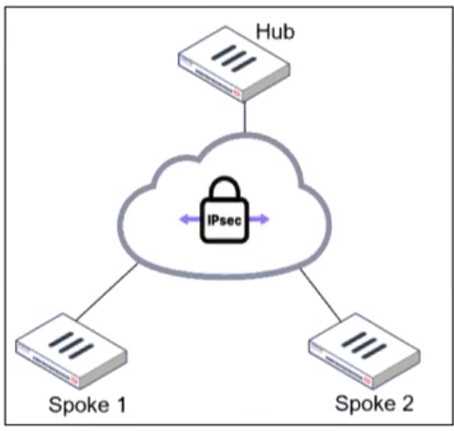 An administrator is deploying a hub and spokes network and using OSPF as dynamic protocol.
Which configuration is mandatory for neighbor adjacency?
An administrator is deploying a hub and spokes network and using OSPF as dynamic protocol.
Which configuration is mandatory for neighbor adjacency?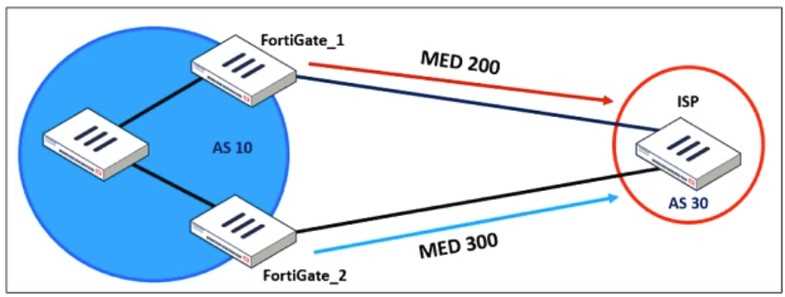 An administrator would like to modify the MED value advertised from FortiGate_1 to a BGP neighbor
in the autonomous system 30.
What must the administrator configure on FortiGate_1 to implement this?
An administrator would like to modify the MED value advertised from FortiGate_1 to a BGP neighbor
in the autonomous system 30.
What must the administrator configure on FortiGate_1 to implement this?