Stallings, W., & Brown, L. (2018). Computer Security: Principles and Practice (4th ed.). Pearson.
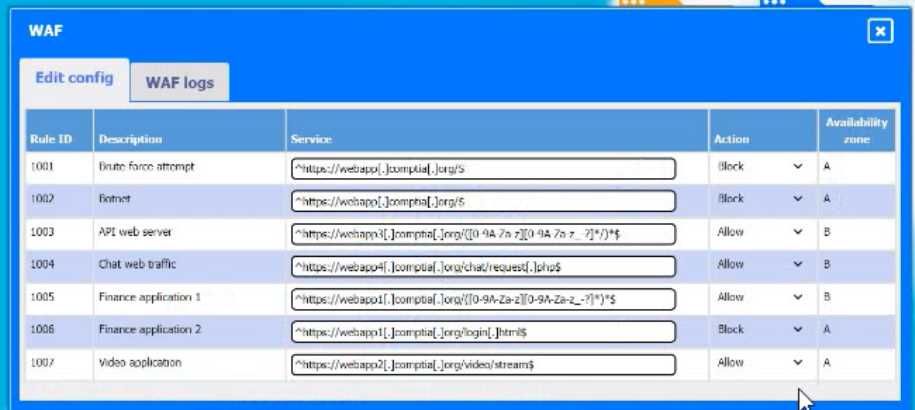
Reference: Chapter 21, "Firewalls and Intrusion Prevention Systems," Section 21.1 Firewall Characteristics. This section discusses how firewalls, including WAFs, use rule-based policies to filter traffic. A misconfigured rule that incorrectly blocks a specific URL or path is a common cause for legitimate traffic being denied access to a web application resource.
Amazon Web Services. (2025). AWS WAF Developer Guide.
Reference: Section "Rule action." The documentation explicitly defines the Block action, which instructs AWS WAF to stop the web request. This aligns with the scenario where the user's access to login.html is being stopped by the WAF. The guide also defines the Allow action as the remedy to permit such requests.
Saltzer, J. H., & Kaashoek, M. F. (2009). Principles of Computer System Design: An Introduction. Morgan Kaufmann.
Reference: Chapter 8, "The Network," Section 8.4.3 Firewalls. The text explains that a firewall's effectiveness is entirely dependent on its configured policy. An incorrect "deny" (or "block") rule within the policy is a primary cause of access problems, where the system incorrectly identifies legitimate traffic as hostile and prevents it from reaching its destination.