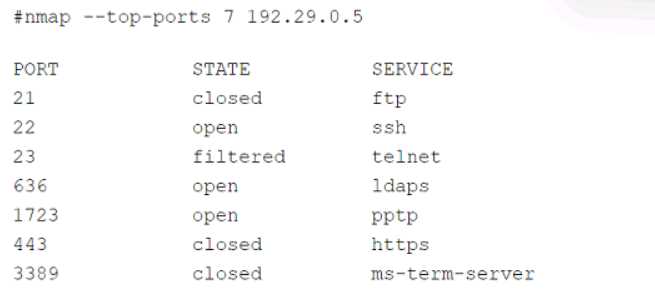
 Which of the following services should the security team investigate further? (Select two).
Which of the following services should the security team investigate further? (Select two).Not sure why people keep picking D and F, those are encrypted protocols by default (LDAPS and RDP). It's A and C you want since FTP (21) and Telnet (23) run cleartext, super common audit findings. SSH on 22 is secure out of the box. Open to correction but that's what all the similar practice questions flag.
Don’t think it’s B, since exfiltration tends to show larger or sporadic data bursts. Regular outbound HTTPS at odd hours is textbook C2 beaconing activity (A). Trap is C, but here the port isn’t unusual.
Option B is right, it directly addresses risk reduction and compliance. C might look tempting if you miss that agile/testing isn’t the main point here. Quick check: does the question mean "best for regulatory compliance" or just general software quality? That could change things.
Pretty sure B is the way to go here-main benefit of secure SDLC is reducing risk and hitting those compliance checkboxes. The other options don't really cover that core reason. Unless I'm missing a weird context?
CompTIA loves cramming compliance into every question, so yeah: B.
Had something like this in a mock. SOAR (A) and SIEM (B) are the best picks because SIEM pulls all alert data into one view and SOAR handles the automation to cut down manual work. XDR is more about detection across sources, not really centralizing workload for analysts.
This kind of scenario pops up often in practice sets and guides. SIEM and SOAR together really help centralize alerts and automate responses. If the question said "most secure" instead of "centralize," would XDR (E) make more sense?
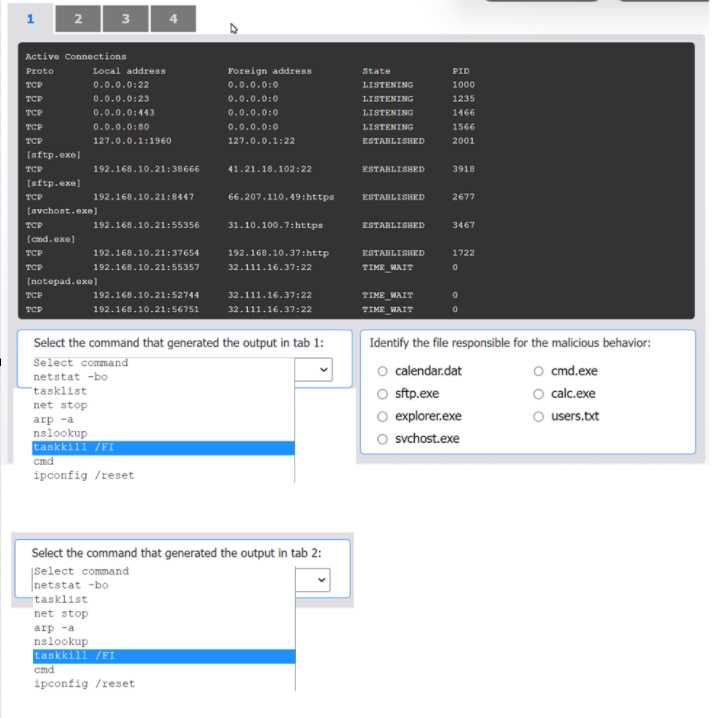
HOTSPOT An organization has noticed large amounts of data are being sent out of its network. An analyst is identifying the cause of the data exfiltration. INSTRUCTIONS Select the command that generated the output in tabs 1 and 2. Review the output text in all tabs and identify the file responsible for the malicious behavior. If at any time you would like to bring back the initial state of the simulation, please click the Reset All button. 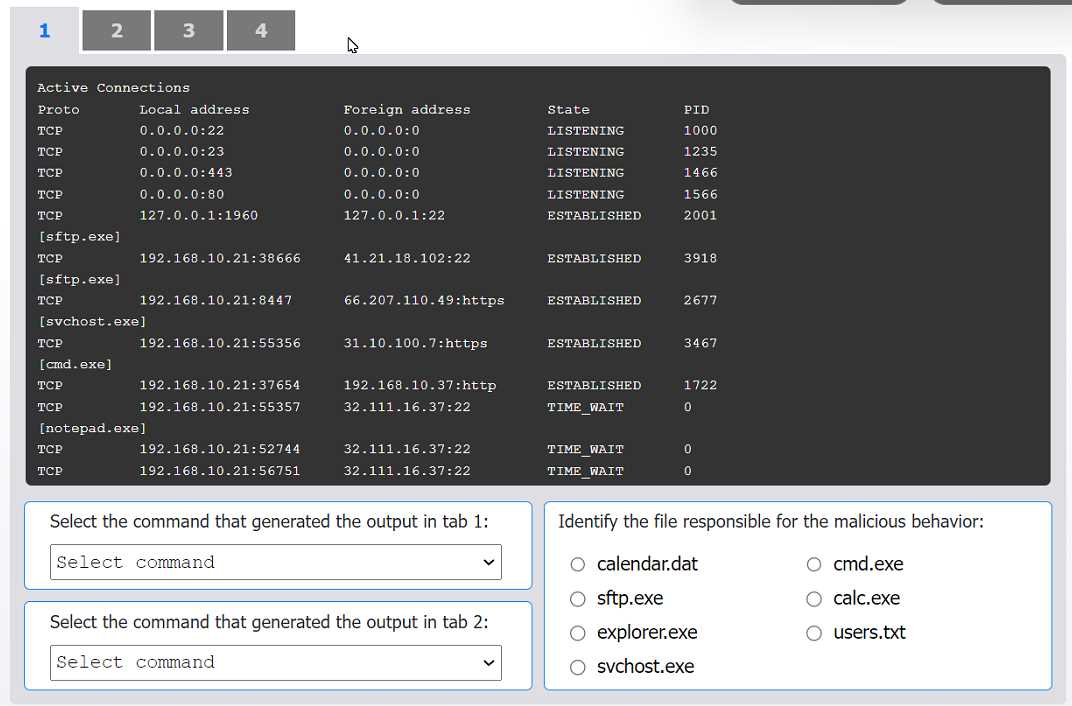
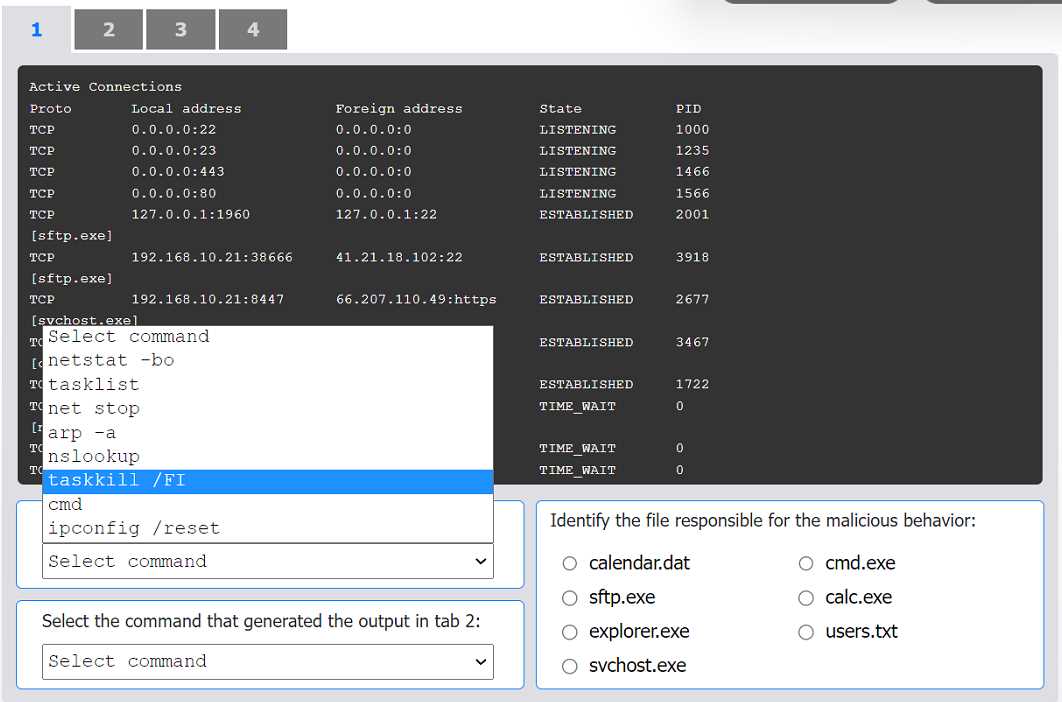
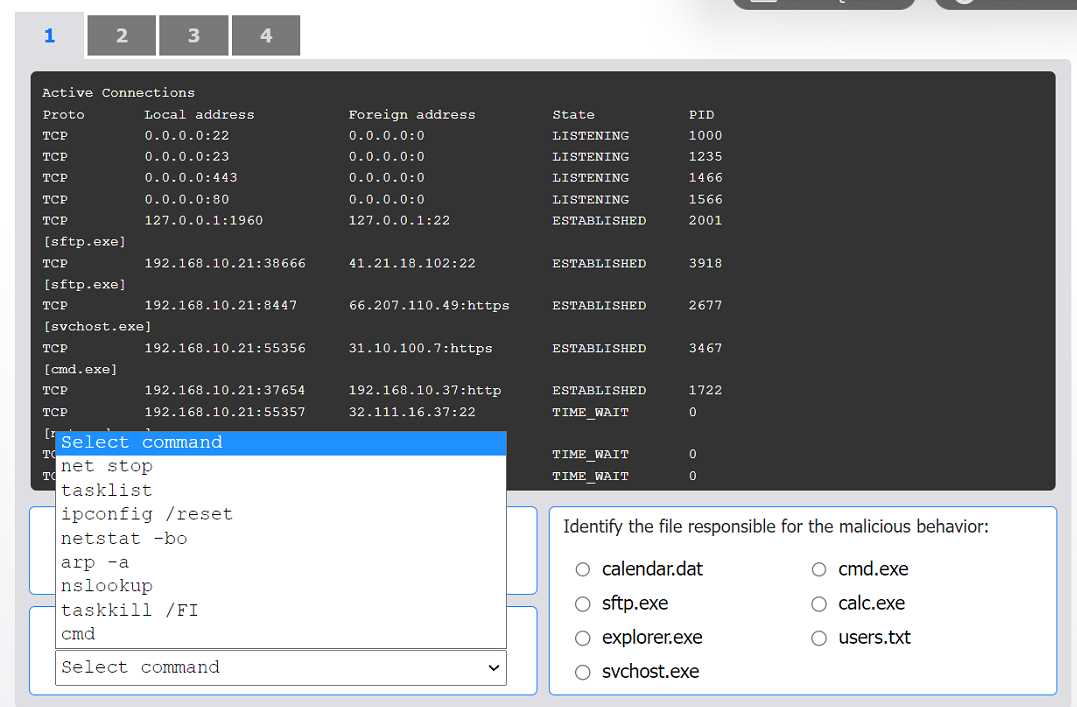
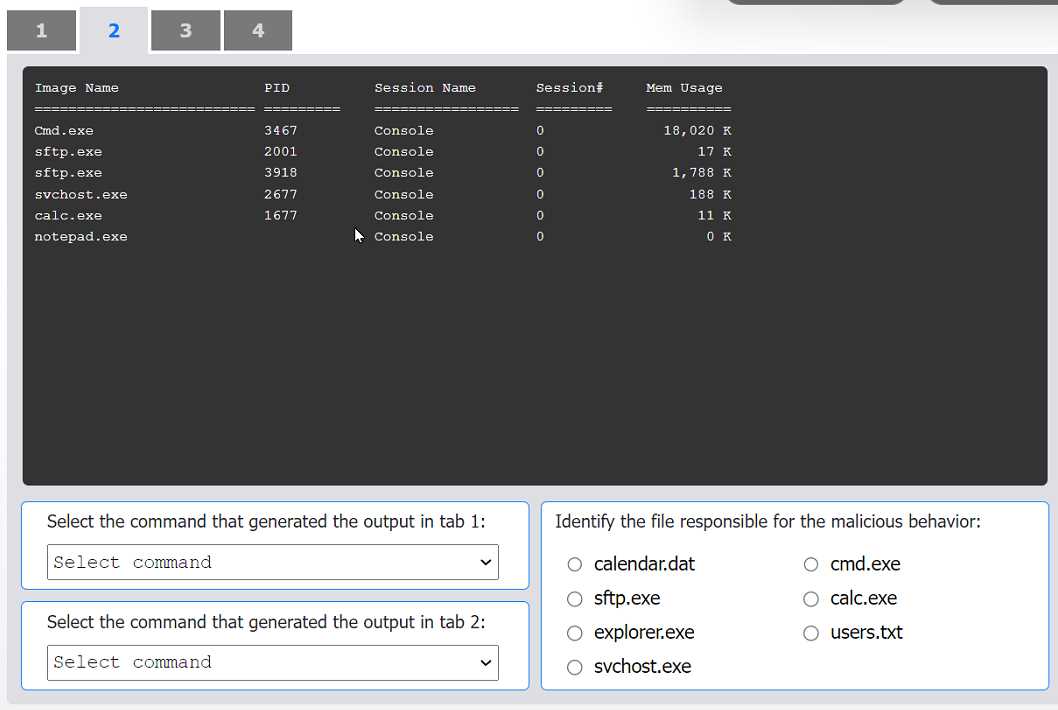
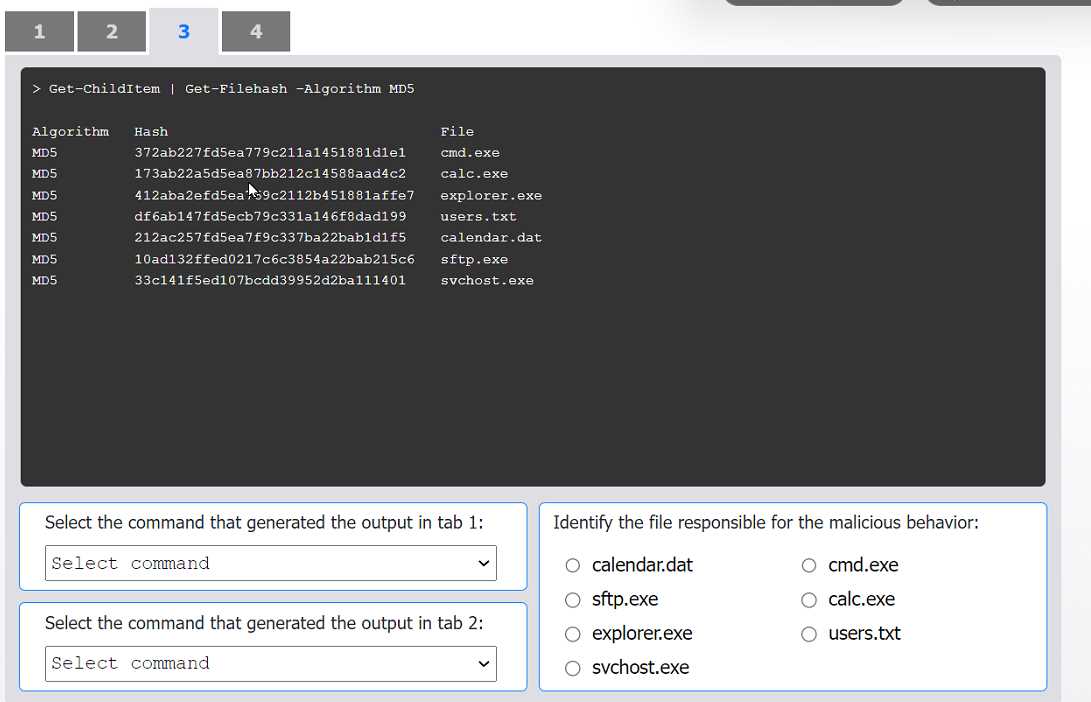
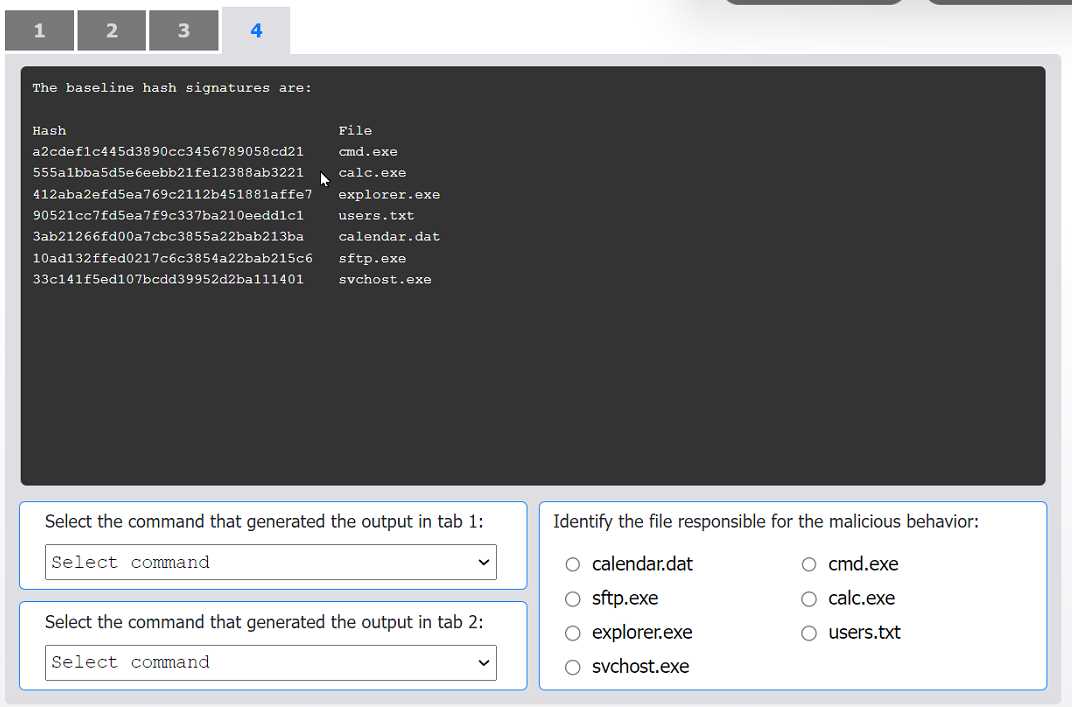
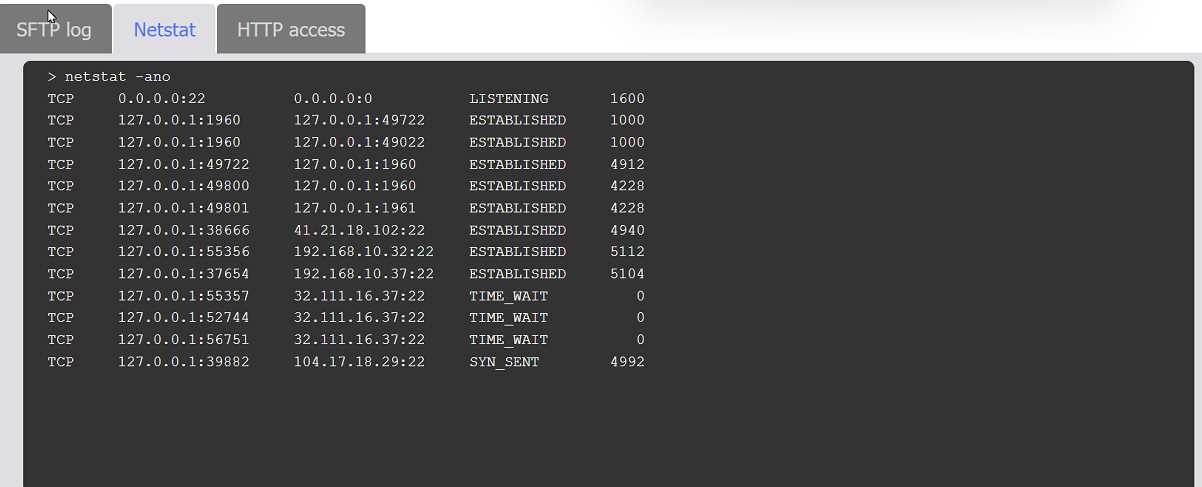
cmd.exe.I can see why folks pick sftp.exe as the file at fault, since it's the one usually handling outbound data transfers. It shows up in netstat with established connections, which is typical for exfil cases. If we only went by network activity and didn't check hash changes, I'd pick sftp.exe here too. Maybe I'm missing something subtle, but seems logical right?
SIMULATION An organization's website was maliciously altered. INSTRUCTIONS Review information in each tab to select the source IP the analyst should be concerned about, the indicator of compromise, and the two appropriate corrective actions. 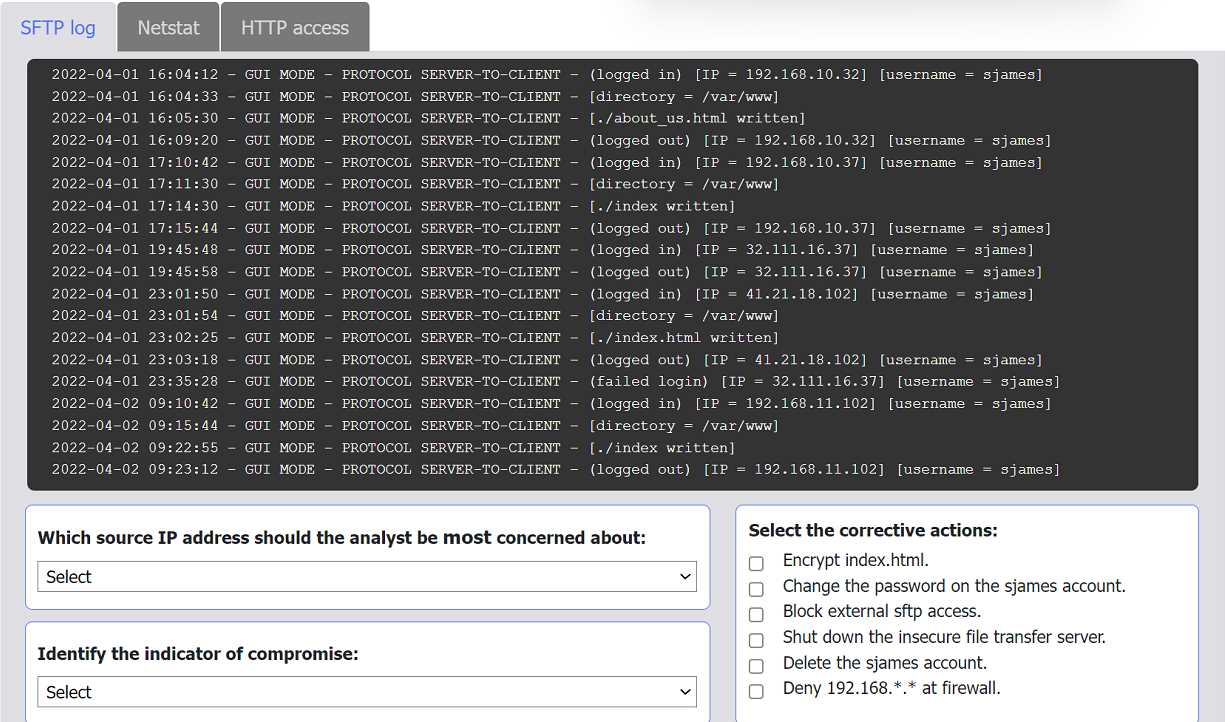
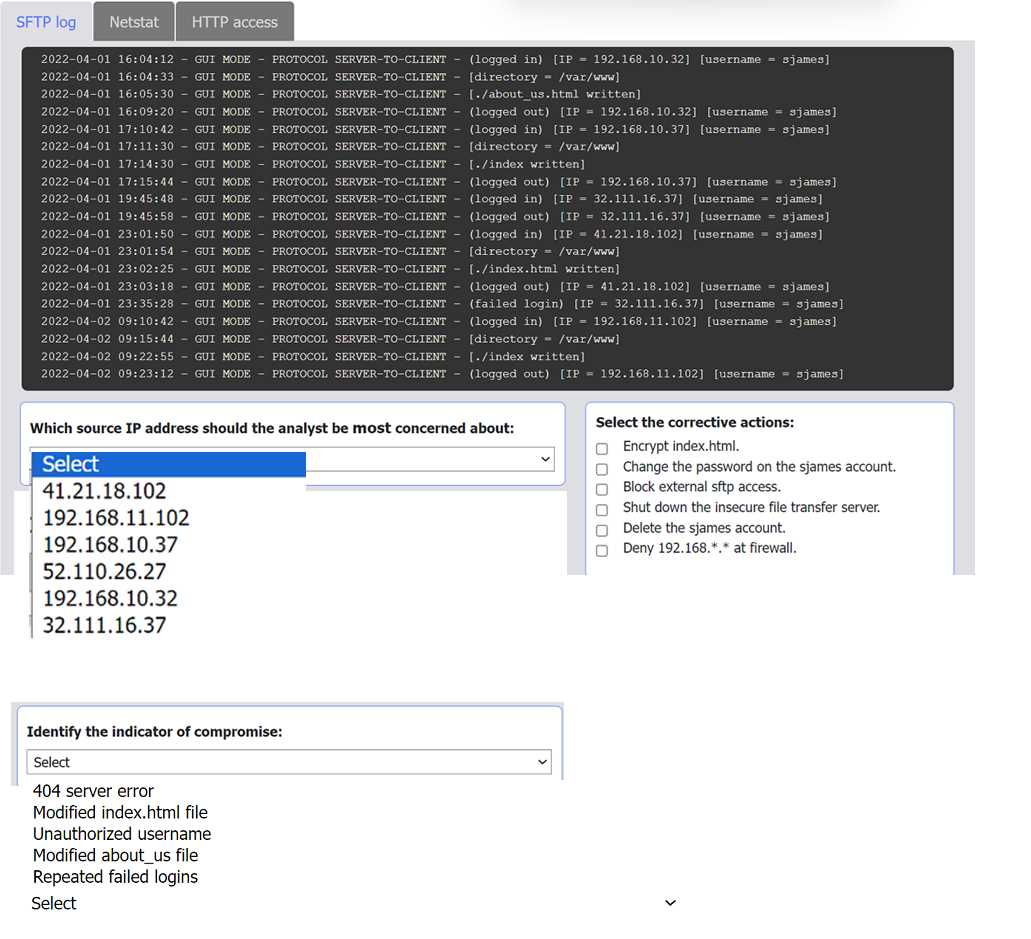
Not quite the internal address. The suspicious activity comes from 41.21.18.102, which logs in as sjames and alters index.html. The two key steps are changing that account's password and deleting it, since internal IPs just reflect normal ops. Seen this logic in other CySA+ practice sets, pretty sure that's right.
Source IP: 10.7.34.82
Indicator: suspicious login times
Actions: disable sjames account, reset web server
I saw a similar question but not totally sure if the internal IP is right here since it connects right before the change. Did anyone else pick these values?