Q: 12
A security audit for unsecured network services was conducted, and the following output was
generated:
 Which of the following services should the security team investigate further? (Select two).
Which of the following services should the security team investigate further? (Select two).
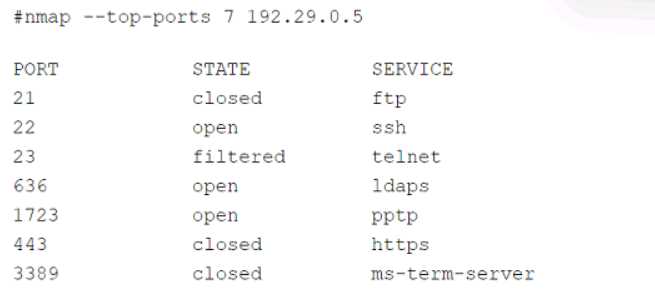 Which of the following services should the security team investigate further? (Select two).
Which of the following services should the security team investigate further? (Select two).Options
Discussion
I saw something like this in a practice test, went with D and F.
A is wrong, C and A. Saw a similar question on practice, FTP (21) and Telnet (23) always flagged as unsecured.
Not sure why people keep picking D and F, those are encrypted protocols by default (LDAPS and RDP). It's A and C you want since FTP (21) and Telnet (23) run cleartext, super common audit findings. SSH on 22 is secure out of the box. Open to correction but that's what all the similar practice questions flag.
Definitely check A and C here. FTP (21) and Telnet (23) both use cleartext so they're usually flagged in audits for being insecure protocols. Pretty sure that's what CompTIA wants you to pick, but open to debate.
A and C tbh. FTP (21) and Telnet (23) both send data in cleartext so they're classic audit targets. SSH (22) is secure, 636 is LDAPS, others less risky here.
Be respectful. No spam.

