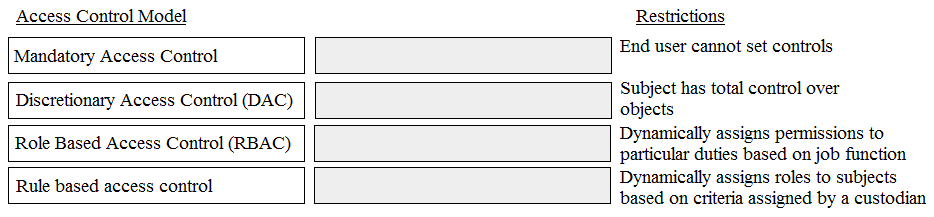
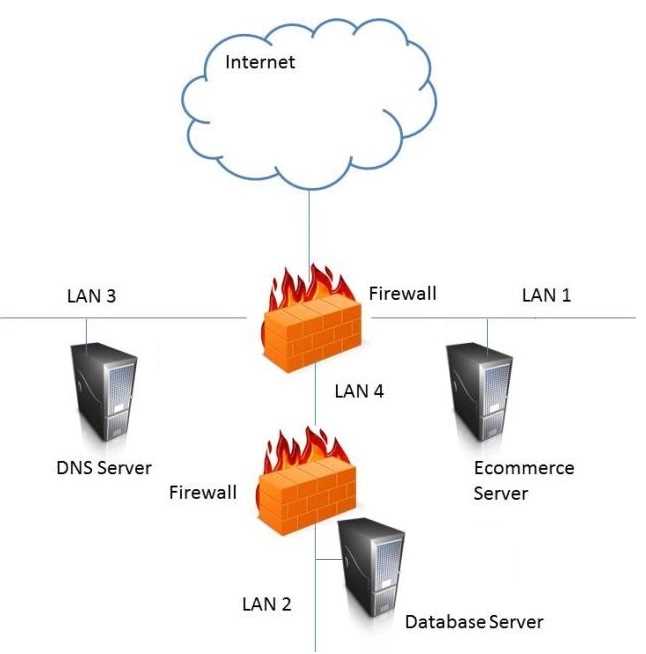
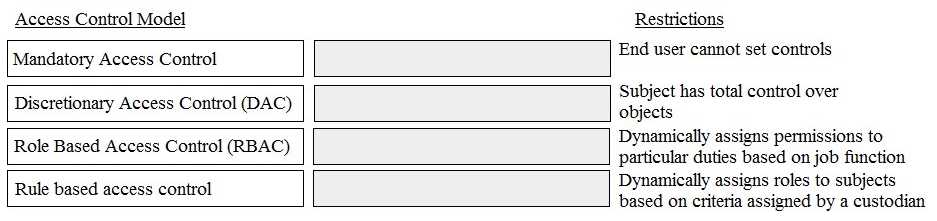
1. Carnegie Mellon University
Software Engineering Institute (CMU/SEI). In the technical note "A Framework for a Vulnerability Management Program
" the authors state
"The selection of tools is a critical step in the implementation of a vulnerability management program." The deployment phase is synonymous with the implementation phase
where the planned program is put into action.
Source: Alberts
C.
& Dorofee
A. (2005). A Framework for a Vulnerability Management Program (CMU/SEI-2005-TN-028). Carnegie Mellon University. (See Section 3.3
"Tool Selection").
2. NIST Special Publication 800-100
"Information Security Handbook: A Guide for Managers." This guide outlines the information security program life cycle
which includes initiation
development/acquisition
implementation
operation/maintenance
and disposal. The selection and procurement of technologies fall squarely within the "development/acquisition" phase
which directly precedes the "implementation" (or deployment) phase. In the context of establishing a new program
these are often grouped as deployment activities.
Source: NIST SP 800-100
Chapter 3
"Information Security Program Management
" Section 3.3
"Information Security Program Life Cycle."
3. University of California
Berkeley
Information Security Office. Courseware and guidance on establishing security programs consistently place budgeting and charter development in the initial "Strategy & Plan" phase
while tool acquisition and implementation occur in the "Build/Deploy" phase. Measuring metrics occurs in the final "Measure & Improve" phase.
Source: UC Berkeley Security
"Vulnerability Management Program
" Program Development Lifecycle documentation. (Illustrates the standard phased approach to program creation).