Q: 20
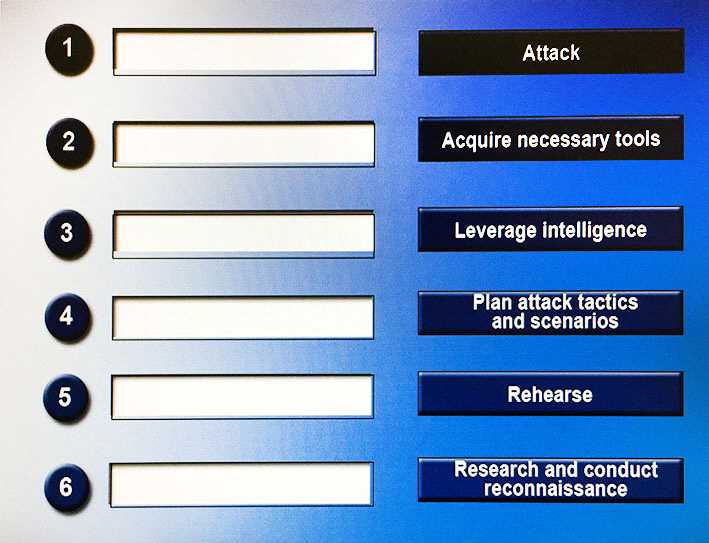
DRAG DROP Drag and drop the following steps to perform a successful social engineering attack in the correct order, from first (1) to last (6).
Drag & Drop
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.