DRAG DROP Drag and drop the attack-mitigation techniques from the left onto the Types of attack that they mitigate on the right. 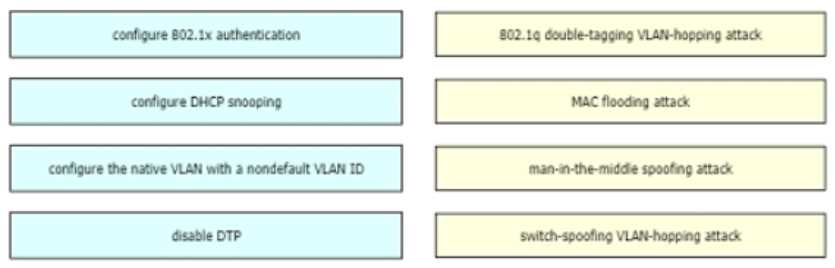
Yeah, this mapping pops up a lot in CCNA practice sets. Native VLAN to double-tagging VLAN hopping, 802.1x authentication for MAC flooding, DHCP snooping for man-in-the-middle (spoofing), and disable DTP for switch-spoofing attacks. Port-security isn't an option for MAC flooding, so 802.1x fits best here imo. Let me know if you'd pick differently.
- 802.1q double-tagging VLAN-hopping attack → Configure the native VLAN with a nondefault VLAN ID
- MAC flooding attack → configure 802.1x authentication
- man-in-the-middle spoofing attack → configure DHCP snooping
- switch-spoofing VLAN-hopping attack → disable DTP
Not quite, I think it's native VLAN with nondefault for double-tagging, 802.1x authentication for MAC flooding, DHCP snooping for MITM spoofing, and disable DTP for switch-spoofing. Easy to mix up MAC flooding since port-security is a common answer, but it's not listed here.

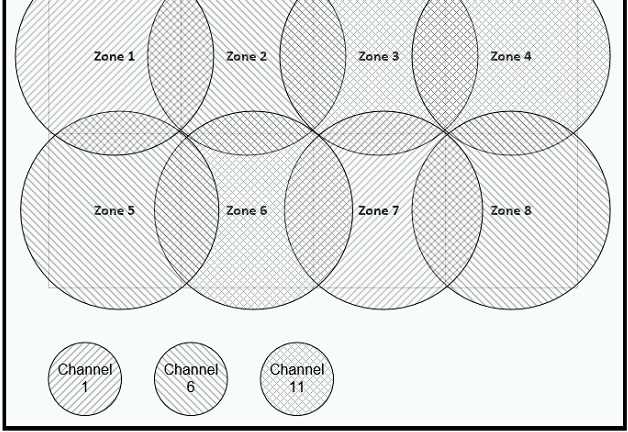 Between which zones do wireless users expect to experience intermittent connectivity?
Between which zones do wireless users expect to experience intermittent connectivity?