Staging environment (A) is the closest to production so it's safest for a final check before release. Testing or dev would be too early in the cycle for a "newly released" feature that's about to go live. Pretty sure on this, agree?
I thought C and E made sense at first look since HIDS could help with firewall and policy checks. But not sure if E really covers Zero Trust app access fully. Pretty sure about C though, could be wrong on E. Anyone see it different?
This question is super clear about mapping requirements to controls. I think C (SCAP) fits since it's meant for config validation and compliance checks like password policies and firewall status. For the Zero Trust/remote access part, D (SASE) makes sense because it covers ZTNA and broader endpoint protections. Open to other views if someone reads it differently though!
Yeah, this is textbook regression testing (A). The whole idea is to run past bug scenarios whenever you pull in older components or make changes, so you can catch stuff like this before it hits production. Code signing and SCA wouldn't actually catch the logic flaw itself. Pretty sure A's the answer here.
Isn't the main issue here that a fixed bug came back after integrating an old component? That usually means something's missing in the regression test suite, rather than needing more automation like C. If tests for that bug had run, it should've been caught even with new-old code coming in. Anyone got a scenario where code signing or SCA (B/E) would actually prevent this?
I don't think it's C. Automated test and retest sounds nice but if the test cases aren't covering previously fixed bugs, automation won't help. A (regression testing) directly targets this problem and is meant to prevent old issues from resurfacing after changes. Tempting to pick C with all the automation buzz but pretty sure A is what they'd expect here. Disagree?
 Code Snippet 2
Code Snippet 2
 Vulnerability 1:
SQL injection
Cross-site request forgery
Server-side request forgery
Indirect object reference
Cross-site scripting
Fix 1:
Perform input sanitization of the userid field.
Perform output encoding of queryResponse,
Ensure usex:ia belongs to logged-in user.
Inspect URLS and disallow arbitrary requests.
Implementanti-forgery tokens.
Vulnerability 2
1) Denial of service
2) Command injection
3) SQL injection
4) Authorization bypass
5) Credentials passed via GET
Fix 2
A) Implement prepared statements and bind
variables.
B) Remove the serve_forever instruction.
C) Prevent the "authenticated" value from being overridden by a GET parameter.
D) HTTP POST should be used for sensitive parameters.
E) Perform input sanitization of the userid field.
Vulnerability 1:
SQL injection
Cross-site request forgery
Server-side request forgery
Indirect object reference
Cross-site scripting
Fix 1:
Perform input sanitization of the userid field.
Perform output encoding of queryResponse,
Ensure usex:ia belongs to logged-in user.
Inspect URLS and disallow arbitrary requests.
Implementanti-forgery tokens.
Vulnerability 2
1) Denial of service
2) Command injection
3) SQL injection
4) Authorization bypass
5) Credentials passed via GET
Fix 2
A) Implement prepared statements and bind
variables.
B) Remove the serve_forever instruction.
C) Prevent the "authenticated" value from being overridden by a GET parameter.
D) HTTP POST should be used for sensitive parameters.
E) Perform input sanitization of the userid field.

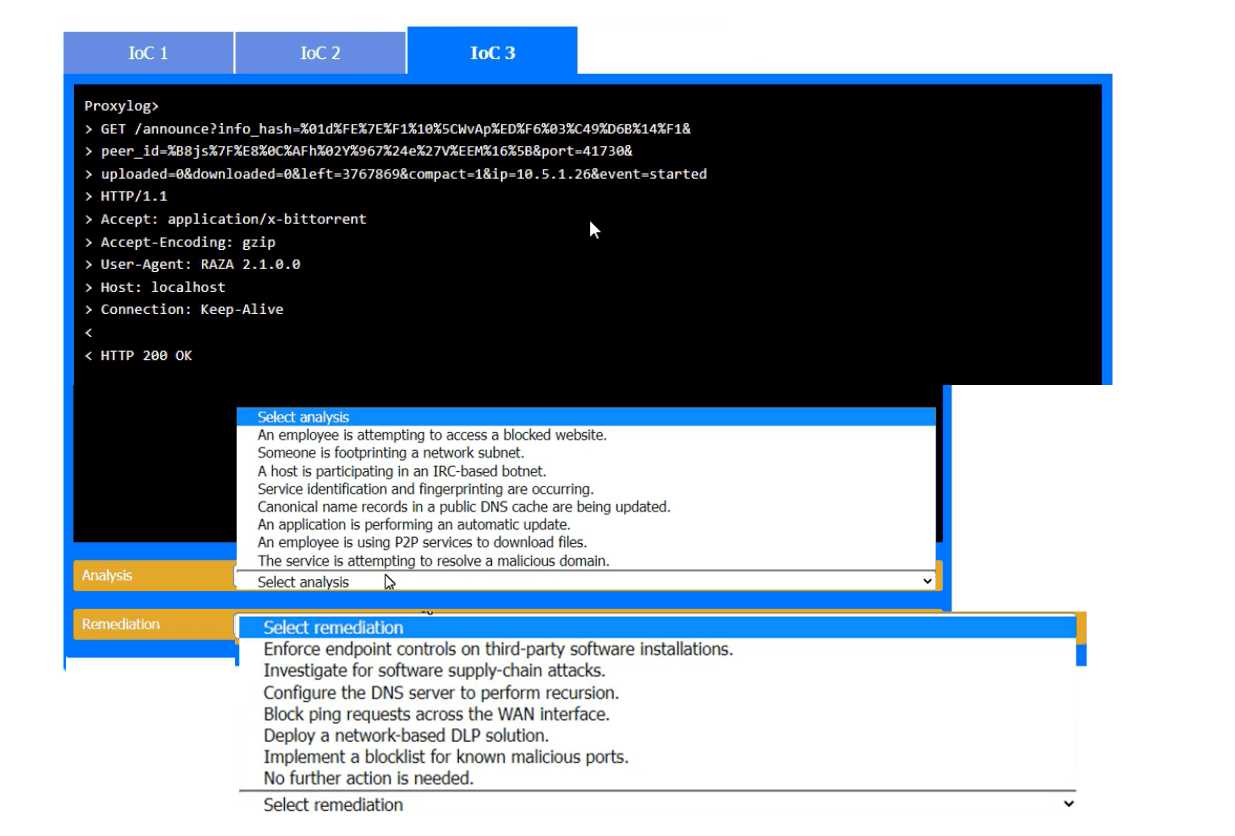
Yeah, I see why it's just "SEE THE"-that's probably all the system wants since the actual analysis and remediation steps are based on each image. The sim wants you to pull details from the screenshots rather than type out answers. Makes sense for a test like this, but let me know if I'm off.
Looks like "SEE THE" is the answer here, probably because it's a simulation and expects you to refer to the provided evidence images for analysis and remediation. Minimal text so you focus on reviewing each IoC's evidence. Makes sense for this CASP+ sim, but correct me if I'm missing something.
Hmm, I don't think the answer is meant to be a full phrase here, it's literally "SEE THE". The sim question is just telling you to check the provided IoC evidence images for your analysis. Tricky wording, maybe some folks would overthink it?

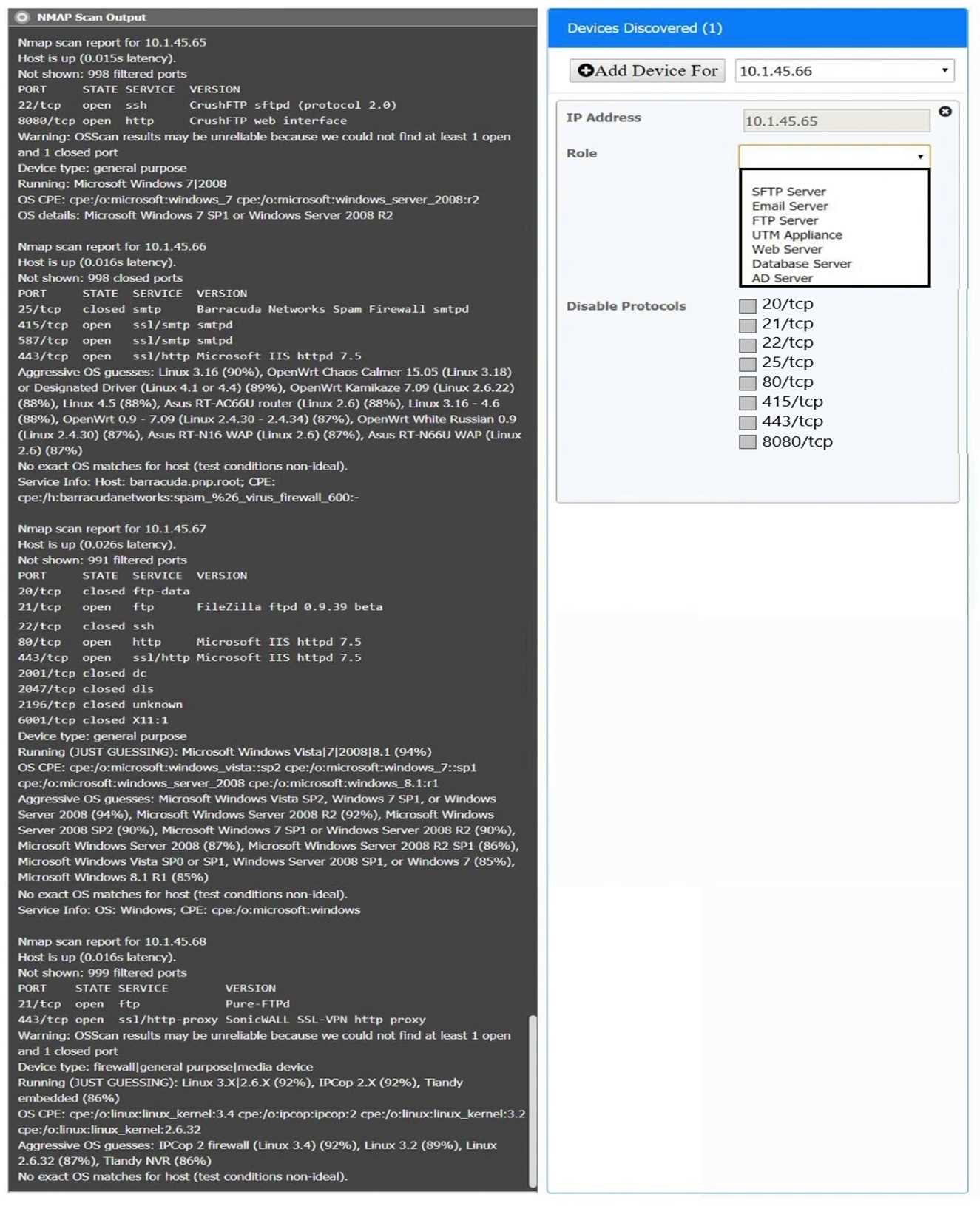
 WAP A
WAP A
 PC A
PC A
 Laptop A
Laptop A
 Switch A
Switch A
 Switch B:
Switch B:
 Laptop B
Laptop B
 PC B
PC B
 PC C
PC C
 Server A
Server A




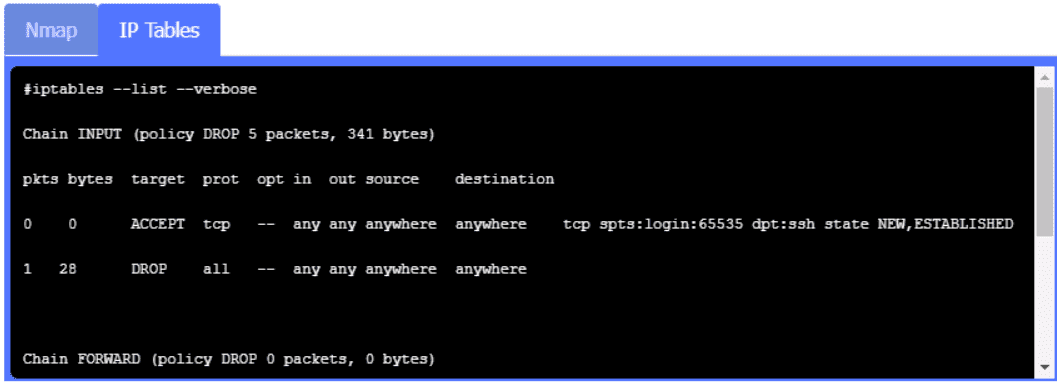
SEE THE
Had something like this in a mock before, and "SEE THE" was literally the accepted answer for these sim formats. It's odd but that's what works for the grading here. Pretty sure that's all they're looking for.
Enable host firewall on PC A, apply updates on Laptop A, disable telnet on Laptop B, enable disk encryption on PC B, and change SSH config on PC C. Each device has a clear fix based on the requirements (host firewall off for workstations, patching, disabling cleartext stuff like telnet, disk encryption for data at rest). Pretty sure these cover all the findings from the screenshots but open to corrections if I missed something in configs.
SEE THE is all that's needed here, I've seen this exact format on other practice sims. It just means reference the image/config given, nothing more to type. Pretty sure that's what counts as correct, agree?
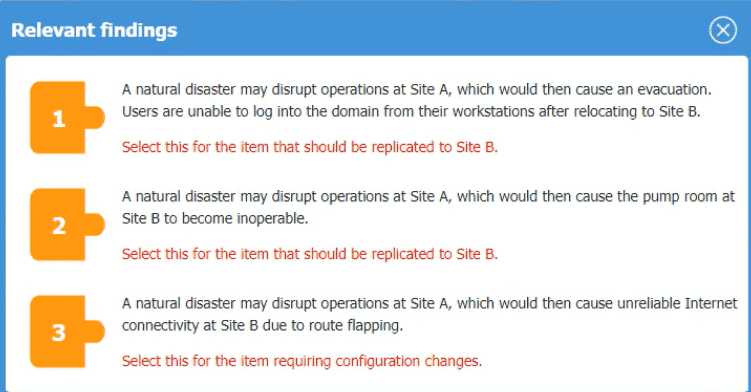
SIMULATION [Security Architecture] An organization is planning for disaster recovery and continuity ofoperations, and has noted the following relevant findings: 1. A natural disaster may disrupt operations at Site A, which would then cause an evacuation. Users are unable to log into the domain from-their workstations after relocating to Site B. 2. A natural disaster may disrupt operations at Site A, which would then cause the pump room at Site B to become inoperable. 3. A natural disaster may disrupt operations at Site A, which would then cause unreliable internet connectivity at Site B due to route flapping. INSTRUCTIONS Match each relevant finding to the affected host by clicking on the host name and selecting the appropriate number. For findings 1 and 2, select the items that should be replicated to Site B. For finding 3, select the item requiring configuration changes, then select the appropriate corrective action from the drop-down menu. 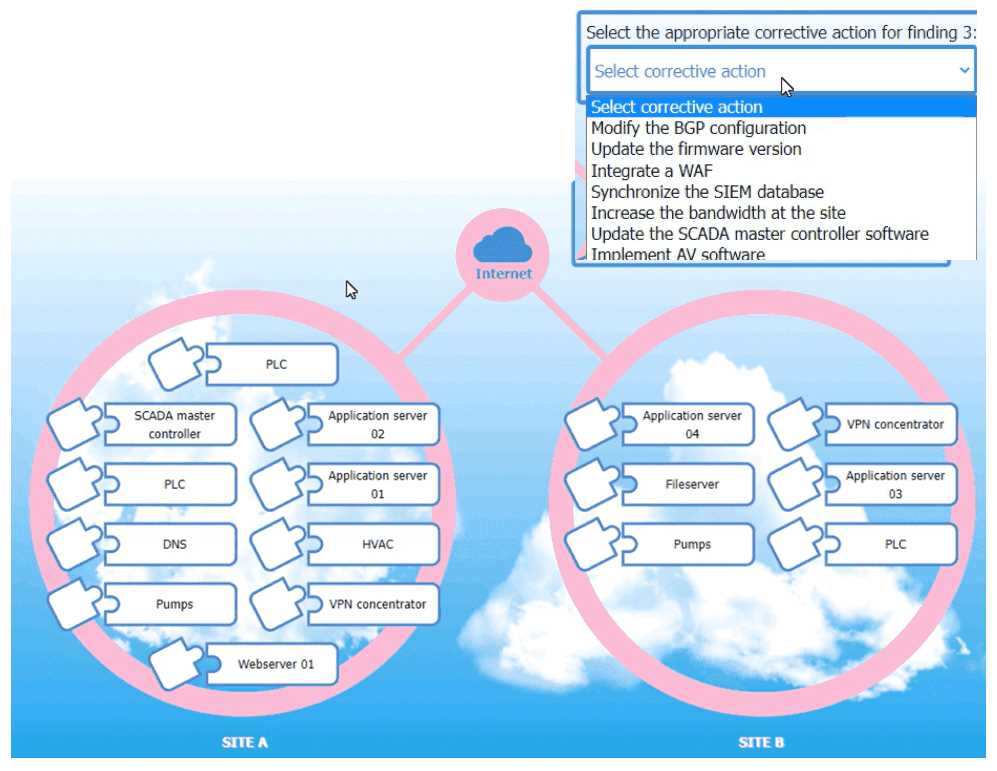
SEE THE
I agree, for finding 1 it's DNS that needs to be replicated so users can log in at Site B, and for finding 2 it's the pump controls not the physical pumps. For finding 3, fix the VPN concentrator's BGP config to stop route flapping. Makes sense unless I'm missing something?
DNS and pump controls both need to be replicated for site failover, that's key for user auth and infrastructure. For the network instability at Site B, I think modifying BGP on the VPN concentrator is the usual fix for route flapping. Makes sense from a disaster recovery perspective, but open if anyone disagrees.
I don’t think it’s DNS that should be replicated for the login issue, I’d say domain controllers at Site B. That’s usually what lets users log into the domain after a site relocation. Correct me if I’m missing something here, but that’s how we handle it in practice.