CISCO ENCOR 350-401 Exam Questions 2025
Our ENCOR 350-401 Exam Questions feature the latest, real exam questions for the Cisco Enterprise Network Core Technologies certification, all verified by Cisco experts. You’ll get accurate answers with in-depth explanations, clarifications on incorrect choices, and references for better understanding. With free demo questions and our online exam simulator, Cert Empire helps you prepare thoroughly and pass your ENCOR 350-401 exam on the first try.
All the questions are reviewed by Aidan Cortes who is a ENCOR 350-401 certified professional working with Cert Empire.
About 350-401 Exam
What is the Cisco 350-401 ENCOR Exam, and what will you learn from it?
The Cisco 350-401 ENCOR (Implementing Cisco Enterprise Network Core Technologies) exam is a crucial step toward earning the Cisco Certified Network Professional (CCNP) Enterprise certification. It also serves as the core exam for the Cisco Certified Internetwork Expert (CCIE) Enterprise Infrastructure and CCIE Enterprise Wireless tracks.
This exam is offered by Cisco, and it validates your ability to implement core enterprise network technologies, including dual-stack (IPv4 and IPv6) architecture, virtualization, infrastructure, network assurance, security, and automation.
By passing ENCOR 350-401, you will learn how to:
- Configure, manage, and troubleshoot enterprise-level networks.
- Implement virtualization and programmability within networks.
- Secure and automate large-scale networks for better efficiency and reliability.
- Prepare yourself for advanced Cisco specializations and higher-level roles in networking.
Exam Snapshot
| Exam Code | 350-401 |
|---|---|
| Exam Name | Implementing Cisco Enterprise Network Core Technologies (ENCOR) |
| Vendor | Cisco |
| Version / Year | 2025 |
| Average Salary | Not officially published. (Based on job market, CCNP / Enterprise Network Engineer roles often command salaries in the range of USD 90,000–130,000+ depending on location, experience, role) |
| Cost | USD $400 (may vary by region) |
| Exam Format | Mixed: multiple-choice, multiple response, drag-and-drop, simulation / lab (simlets) |
| Duration (minutes) | 12000 |
| Delivery Method | In-person at Pearson VUE test center or online proctored (where available) (standard Cisco delivery via Pearson VUE) |
| Languages | English (and select regional languages as supported by Pearson VUE in your geography) |
| Scoring Method | Scored on a scaled score (0–1000) based on weighted question values. Simulation/labs also contribute. |
| Passing Score | Community sources suggest 825 / 1000 (≈ 82.5 %) for version 1.1 |
| Prerequisites | None formally required. Cisco recommends 3–5 years of enterprise network experience. |
| Retake Policy | If you do not pass, you must wait 5 calendar days before retaking the exam. Standard Cisco retake rules apply. |
| Target Audience | Network engineers, infrastructure engineers, enterprise network architects, those seeking CCNP Enterprise or CCIE Enterprise core |
| Certification Validity | 3 years (you must recertify via exam or continuing education) |
| Release Date | 2023-09-20 |
Prerequisites before taking the 350-401 Exam
There are no formal prerequisites to attempt the Cisco 350-401 exam. However, Cisco strongly recommends:
- 3–5 years of experience in implementing enterprise networking solutions.
- A strong grasp of network fundamentals, routing and switching, and Cisco device configuration.
- Prior exposure to Cisco IOS XE and enterprise-level LAN/WAN technologies.
While not mandatory, earning the Cisco CCNA certification first provides a helpful foundation for success.
Main Objectives and Domains You Will Study for 350-401
The Cisco 350-401 exam covers six major domains of enterprise networking:
- Architecture – 15%
- Virtualization – 10%
- Infrastructure – 30%
- Network Assurance – 10%
- Security – 20%
- Automation – 15%
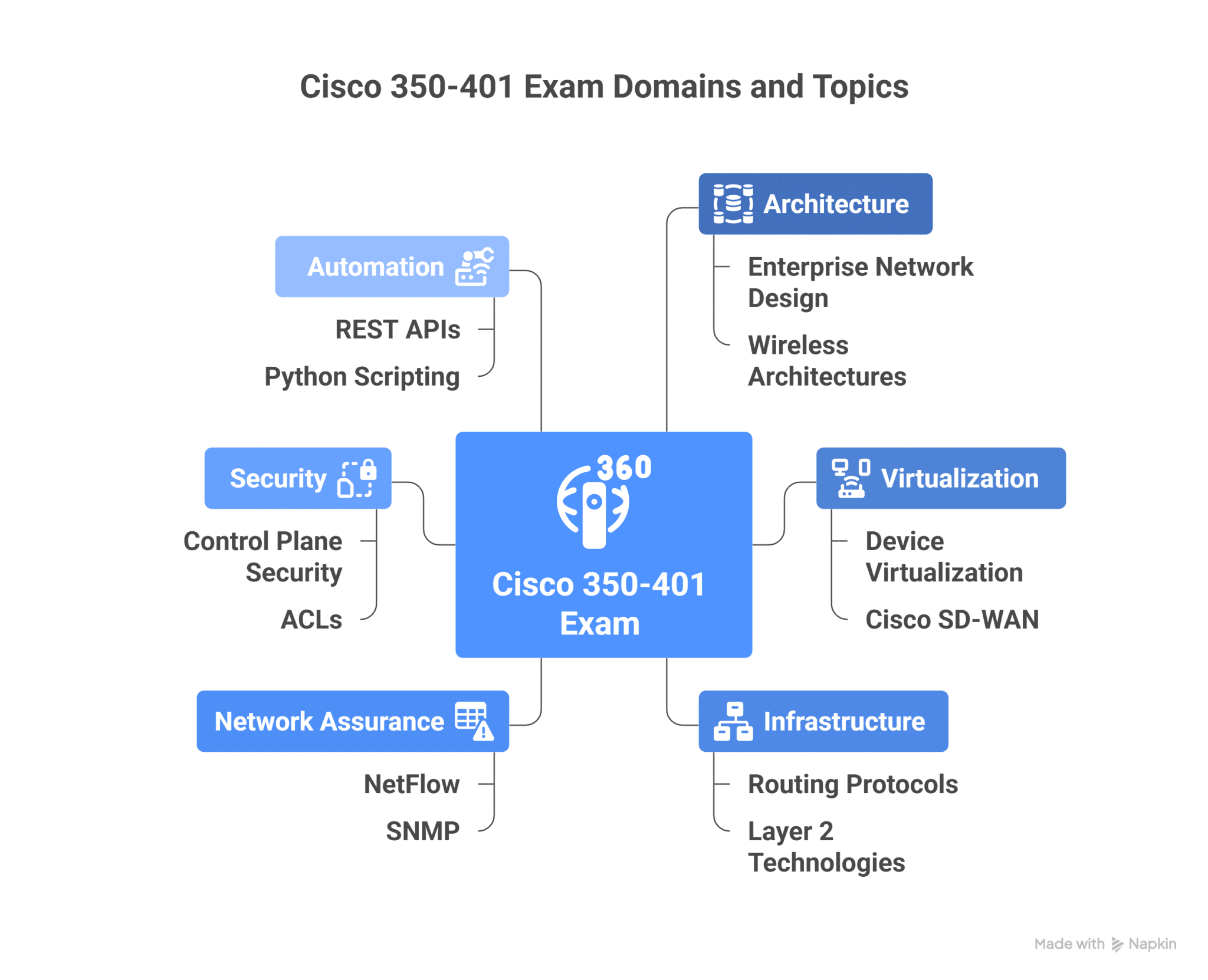
Topics to Cover in Each 350-401 Exam Domain
1. Architecture
- Understand enterprise network design principles (Campus LAN, WAN, SD-Access, etc.).
- Compare on-premises vs. cloud networking.
- Learn about wireless architectures and high availability protocols (HSRP, VRRP, GLBP).
2. Virtualization
- Master device and network virtualization concepts such as VRF, GRE, and VPNs.
- Implement Cisco SD-WAN and understand Cisco DNA Center basics.
3. Infrastructure
- Routing protocols: OSPF, EIGRP, BGP, and static routing.
- Layer 2 technologies: STP, EtherChannel, VLANs, and trunking.
- Layer 3 switching and IPv6 configurations.
4. Network Assurance
- Learn NetFlow, SPAN, and Syslog for monitoring and troubleshooting.
- Implement SNMP and model-driven telemetry for network visibility.
5. Security
- Secure control, management, and data planes.
- Implement ACLs, 802.1X, Cisco TrustSec, and device hardening.
- Integrate Cisco ISE for identity-based networking.
6. Automation
- Understand REST APIs, JSON, YANG, NETCONF, and Python scripting.
- Implement automation tools such as Ansible and Cisco DNA Center workflows.
Changes in the Latest Version of Cisco 350-401
The ENCOR exam has evolved to match the needs of modern enterprise networks. The latest version emphasizes:
- Network automation and programmability (Python, APIs, SDN concepts).
- Software-defined architectures (Cisco DNA, SD-Access).
- Cloud and virtualization integration.
- Greater focus on security frameworks and Zero Trust architectures.
Register and Schedule Your Cisco 350-401 Exam
You can register for the 350-401 exam via Pearson VUE:
- Create or log in to your Cisco Certification account.
- Choose the Implementing Cisco Enterprise Network Core Technologies (ENCOR 350-401) exam.
- Select your preferred language (English or Japanese).
- Schedule the exam online or at a testing center.
You’ll receive your exam results immediately after completion.
Cisco 350-401 Exam Cost and Available Discounts
- Exam Fee: USD $400 (price may vary by region).
- Discount Options:
- Cisco sometimes offers discount vouchers through training partners.
- Students and military personnel may qualify for special pricing.
- Group training packages via Cisco Learning Partners often include exam discounts.
Exam Policies You Should Know Before Taking Cisco 350-401
- You must bring valid government-issued photo ID.
- No personal items (phones, watches, notes) are allowed.
- You can retake the exam after 5 calendar days if you fail.
- Certification is valid for 3 years; recertification requires either retaking the exam or earning Continuing Education (CE) credits.
What Can You Expect on Your Cisco 350-401 Exam Day?
Expect a proctored environment either at a Pearson VUE center or online.
You’ll encounter:
- Scenario-based questions simulating real network issues.
- A blend of theory and hands-on configuration tasks.
- Tight time management requirements, so practice pacing yourself.
Take a few deep breaths before you start; it’s a comprehensive but achievable exam if you’re well-prepared.
Plan Your 350-401 Study Schedule Effectively with 5 Study Tips
Tip 1: Create a 12-week plan, dedicating at least 2–3 hours daily to one domain at a time.
Tip 2: Use Cisco’s official study materials (Cisco Press, ENCOR Official Cert Guide).
Tip 3: Join online forums or Discord groups where candidates share exam experiences.
Tip 4: Practice real exam scenarios through labs (Cisco Packet Tracer, GNS3, or EVE-NG).
Tip 5: Take mock exams and practice tests to measure your readiness.
Pro Tip: Use CertEmpire’s premium question files for real exam-like practice, one of the best resources available: Get your Cisco 350-401 exam questions at CertEmpire.
Best Study Resources You Can Use to Prepare for Cisco 350-401
- Cisco Press Books: “Implementing Cisco Enterprise Network Core Technologies (ENCOR) Official Cert Guide.”
- Cisco Learning Network: Access free videos, practice labs, and community discussions.
- CertEmpire Practice Exam: Reliable, updated question banks for real-world practice.
- Boson ExSim or CBT Nuggets: Great for simulated practice exams and video lessons.
- Hands-on Labs: Use EVE-NG, GNS3, or Packet Tracer for real practice.
Career Opportunities You Can Explore After Earning Cisco 350-401
Passing the Cisco 350-401 exam opens doors to various high-demand roles, such as:
- Network Engineer
- Enterprise Infrastructure Specialist
- Network Security Engineer
- Wireless Network Engineer
- Network Consultant or Architect
These roles often come with salaries ranging from $90,000 to over $ 130,000 annually, depending on experience and region.
Certifications to Go for After Completing Cisco 350-401
Once you’ve cleared 350-401, consider pursuing:
- CCNP Enterprise (specialization exam required)
- CCIE Enterprise Infrastructure or Wireless
- Cisco DevNet Professional for automation-focused careers
- Cisco Security Core (SCOR 350-701) for network security specialization
How Does Cisco 350-401 Compare to Other Beginner-Level Cloud Certifications?
|
Certification |
Focus Area |
Difficulty Level |
Career Path |
|
Cisco 350-401 (ENCOR) |
Enterprise networking, automation, security |
Intermediate |
Network & Infrastructure Engineering |
|
Microsoft AZ-900 |
Cloud fundamentals |
Beginner |
Cloud computing, Azure basics |
|
AWS Cloud Practitioner |
Cloud services overview |
Beginner |
Cloud solutions, DevOps |
|
CompTIA Network+ |
Networking fundamentals |
Beginner |
IT and Network Support |
Ready to pass your Cisco 350-401 ENCOR exam?
Practice smarter with real, updated questions and verified answers.
Visit Cert Empire for the best Cisco 350-401 exam question files and boost your preparation today!
FAQS
Frequently Asked Questions (FAQs)
Q1. What is the Cisco 350-401 ENCOR exam?
The Cisco 350-401 ENCOR is the core exam for Cisco’s CCNP Enterprise certification path. It evaluates your ability to implement and troubleshoot advanced enterprise networking solutions, including automation, security, and dual-stack technologies.
Q2. Who should take the Cisco 350-401 exam?
Network professionals, system engineers, and administrators who want to advance toward Cisco’s professional or expert-level certifications should take this exam. It’s ideal for anyone managing or designing enterprise-level networks.
Q3. How difficult is the Cisco 350-401 ENCOR exam?
The ENCOR exam is moderately difficult and technical. It requires a strong understanding of routing, switching, wireless, and automation. Regular practice with simulated questions helps reduce difficulty and builds confidence.
Q4. What topics are covered in the 350-401 ENCOR exam?
The exam includes architecture, virtualization, infrastructure, network assurance, security, and automation. Each domain carries a different weight, making it essential to prepare comprehensively across all topics.
Q5. How do Cert Empire’s Cisco 350-401 questions help in preparation?
Our practice questions bank reflect Cisco’s real exam style, including scenario-based and logic-driven items. Each question has explanations and references that reinforce understanding and strengthen exam-level reasoning.
Q6. Are these 350-401 questions real Cisco dumps?
No. Cert Empire provides legal and verified practice content. Our files are created by Cisco-certified experts to simulate real-exam logic and structure without violating Cisco’s exam policies.
Q7. How often is the Cisco 350-401 material updated?
We review and update every ENCOR file frequently to align with the latest Cisco blueprint and technical changes. You’ll always have access to the most accurate and up-to-date question set available.
Q8. Can I study the 350-401 PDF on my phone?
Yes. Cert Empire’s PDF and simulator are optimized for mobile and tablet use. You can study anywhere, whether you’re traveling or reviewing short sessions on your lunch break.
Q9. How long will I have access to the material?
You get unlimited access to your simulator and files for three months. This allows you to study at your own pace, revisit difficult areas, and build the consistency needed to pass.
Q10. Does Cert Empire offer a free Cisco 350-401 practice test?
Yes. We provide a free Cisco 350-401 sample test on the right sidebar. It includes a few representative questions so you can experience our quality and interface before purchasing the full version.
6 reviews for CISCO ENCOR 350-401 Exam Questions 2025
32 thoughts on "CISCO ENCOR 350-401 Exam Questions 2025"
-
How well did the CISCO 350-401 exam dumps prepare you for the exam topics outlined in the official blueprint?
-
Seems to be a Quite Helpful resource
-
-
Connor: Quick question, everyone, In a Cisco SDN setup, which protocol is mainly used for communication between the controller and switches?
a) OSPF
b) BGP
c) OpenFlow
d) NETCONF-
It’s definitely c) OpenFlow. That’s the protocol that allows the controller to directly modify flow tables on switches. I remember Cisco stressing that in their official docs.
-
Hmm, I thought NETCONF was also involved in controller communications? I’m a bit confused about the exact role of NETCONF vs OpenFlow here.
-
Good question, Owen. NETCONF is mostly for configuration management, pushing configuration changes and gathering device info via XML. OpenFlow, on the other hand, is specifically for controlling packet forwarding in SDN environments.
-
Adding to Nina, OpenFlow works at the data plane level, letting the controller instruct devices how to handle traffic. NETCONF is more management plane-focused.
-
So basically, OpenFlow is about directing how packets flow, while NETCONF manages device configurations but doesn’t control packet forwarding paths.
-
Yeah, it’s an important distinction. OpenFlow installs flow entries in switches’ flow tables, which is key for SDN’s dynamic traffic control.
-
I’m curious, does Cisco exclusively use OpenFlow, or do they support other protocols for controller communication?
-
Cisco supports multiple protocols. While OpenFlow is the standard southbound protocol in many SDN implementations, Cisco also leverages NETCONF, RESTCONF, and proprietary APIs depending on the platform and use case.
-
I remember being tripped up because BGP is such a popular routing protocol. But BGP doesn’t really have anything to do with controller-device communication in SDN, right?
-
Correct. BGP is for exchanging routing information between different autonomous systems. It doesn’t handle controller instructions to devices.
-
The exam will almost always expect OpenFlow for this type of question about SDN controller communication. It’s the safest bet.
-
It’s worth noting though that in practical deployments, sometimes hybrid models combine OpenFlow with other protocols for flexibility.
-
Thanks for clarifying! I was mixing up management and control plane protocols. Now it makes more sense.
-
Same here. Initially, I thought NETCONF was the default for everything controller-related. This clears it up nicely.
-
OpenFlow’s ability to dynamically update flow tables means the controller can reroute traffic instantly without waiting for traditional routing protocol convergence.
-
Exactly. That’s why SDN is considered revolutionary, it separates control logic from the forwarding hardware.
-
For the exam, if they mention “controller-to-device communication,” OpenFlow should be your go-to answer unless they specify configuration protocols.
-
Cisco’s DevNet has excellent hands-on labs showing OpenFlow in action. That really helped me internalize these concepts beyond theory.
-
Labs are fantastic. I struggled with the theory until I got to see OpenFlow programming live.
-
Are there any known limitations or challenges with OpenFlow in real networks?
-
Yes, some say OpenFlow adds overhead and complexity, and not all devices support it fully. So in production, Cisco sometimes uses hybrid approaches combining OpenFlow with traditional routing and management protocols.
-
That makes sense. But for exam purposes, I guess we focus on the idealized concept of OpenFlow as the main controller-device protocol.
-
Exactly. Don’t overcomplicate it for the exam. Stick with Cisco’s official curriculum and you’ll be fine.
-
This discussion helped a lot! Appreciate all your inputs.
-
Happy to help! Good luck with your studies.
-
I feel much clearer on this topic now. Thanks, everyone!
-
Glad to contribute! Let’s keep sharing knowledge.
-
Looking forward to tackling the next topic with you all.
-
-
-
-




Ethan Good (verified owner) –
I’ll always be thankful for this resource. It played a crucial role in my exam success and helped me achieve my goals. 100% Recommended Resource.
Parker (verified owner) –
Cert Empire provided me with support on how to prepare for my exam. It gave me a roadmap for preparation, and using Cert Empire dumps helped me pass my exam.
1905.mohammed.ahmed (verified owner) –
The study material is excellent, and I’m really impressed with the customer support. They’re very responsive and always ready to assist with any questions or concerns. It’s great to know that I can rely on such strong support throughout my preparation!
Aadi (verified owner) –
This was my first time using dumps, and I’m glad I went with Cert Empire. The material was highly useful and made my exam preparation much smoother. I also appreciate their support team for always being available whenever I needed assistance with the dumps.
Olivia (verified owner) –
If someone asks me to describe Cert Empire’s dumps in one word, I would simply say “fantastic”.
Olivia (verified owner) –
The study material from Cert Empire was really helpful. It covered all the key topics and made me feel more confident before the exam.