Why Practice Exam Questions Are Essential for Passing Cisco 300-410 Exam in 2025
Passing the 300-410 certification isn’t about memorizing terms or rot learning, it’s about developing the aptitude required of a network implementation and troubleshooting professional. Loaded with detailed explanations and extensive references, Cert Empire’s 300-410 Exam Questions are designed to help you think like an actual enterprise routing and services specialist. These practice questions mirror the Cisco exam pattern, guiding you through what’s required to pass the exam on your first attempt and you can discover more on Cert Empire to continue strengthening your preparation.
Prepare Smarter with Exam Familiar Quiz
The 300-410 exam is challenging and broad, but consistent practice transforms that difficulty into strength. By regularly solving real exam-style questions, you’ll improve your pacing, reduce anxiety, and recognize recurring question logic. Over time, the format will feel second nature, allowing you to focus on accuracy instead of uncertainty on exam day.
Master Every Domain with Real Exam Logic
The 300-410 practice questions cover all official domains in the correct proportion. This means you’re not just preparing one domain, but all of them, making your exam preparation comprehensive.
What’s Included in Our 300-410 Exam Prep Material
It’s not just a question blob that we offer, but a whole experience that transforms your exam preparation. Here is exactly what you get:
PDF Exam Questions
- Instant Access: Start preparing right after purchase with immediate delivery.
- Study Anywhere: Access the soft form questions from your phone, laptop, or tablet.
- Printable Format: Ideal for offline review and personal note-taking, and especially if you prefer to study from hard-form documents.
Interactive Practice Simulator
- Question Simulation: Our online 300-410 exam practice simulator is designed to help you interactively review and prepare for the exam with tailored features such as show/hide answers, see correct answers etc.
- Flashcard-like Practice: Save your toughest questions and revisit them until you’ve mastered each domain.
- Progress Tracking: The progress tracking feature of our quiz simulator lets you resume your study journey right from where you left.
3 Months of Unlimited Access
Enjoy full, unrestricted access for three months, long enough to practice, revise, and retake simulations until you are satisfied with your results.
Regular Updates
Networking and enterprise routing are ever-evolving fields, so being current is the cornerstone of 300-410 exam prep. Being mindful of that, CertEmpire’s certified exam coaches keep the content of the practice questions up to date with the latest exam requirements so that you always have the latest exam questions and resources available to you.
Free Practice Tests
To make the decision easy for you, we offer free practice tests for the 300-410 exam. Look at the right side-bar and you will find the free practice test button that will take you to a sample free 300-410 practice test. Go through the free 300-410 exam questions section and discover the richness of our practice questions.
Free Exam Guides
Cert Empire offers free exam preparation guides for 300-410. You can find a trove of 300-410 related exam prep resources at our website in our blog section. From tailored study plans for success in 300-410 to exam day guidelines, we have covered it all. Cherry on the top, you do not have to be our customer to access this material, and it is free for all.
Important Note
Our 300-410 Exam Questions are updated regularly to match the latest Cisco exam version.
The Cert Empire content team, led by certified 300-410 professionals, has taken the newest release and added updated concepts, frameworks, and routing technologies, VPN configurations, and infrastructure security models to ensure relevance.
✔ Each question includes detailed reasoning for both correct and incorrect options, helping you understand the full context behind every answer.
✔ Every solution links to official Cisco references, allowing you to expand your knowledge through verified documentation.
✔ Mobile-Compatible – Both the PDF and simulator versions are easy to use across smartphones, tablets, laptops, and even in printed form.
The 300-410 remains one of the most respected and highest-paying certifications in enterprise networking, proving mastery of advanced routing, network infrastructure, and security implementation skills.
Is this Exam Dump for Cisco 300-410?
No, CertEmpire offers exam questions for practice purposes only. We do not endorse using Cisco Exam Dumps. Our product includes expert crafted and verified practice exam questions and quizzes that emulates the real exam. This is why you may find many of the similar questions in your exam, which can help you succeed easily. Nonetheless, unlike exam dumps websites, we do not give any sort of guarantees on how many questions will appear in your exam. Our mission is to help students prepare better for exams, not endorse cheating.
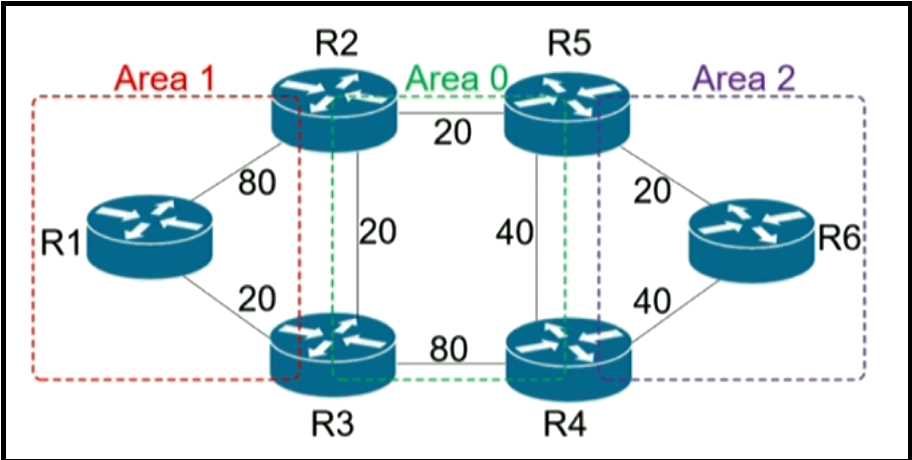 R6 should reach R1 via R5>R2>R1. Which action resolves the issue?
R6 should reach R1 via R5>R2>R1. Which action resolves the issue?
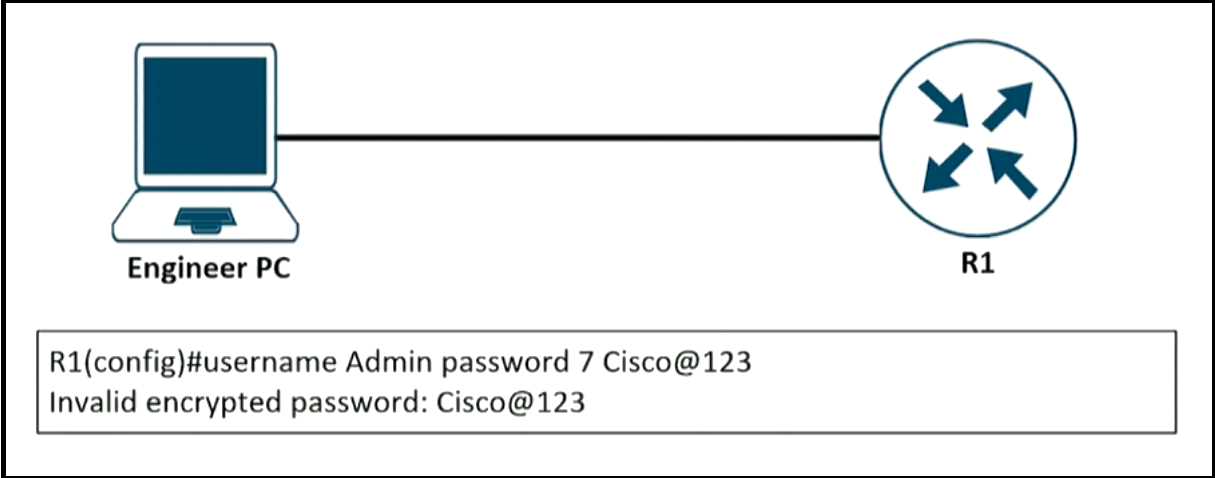 An engineer is trying to add an encrypted user password that should not be visible in the router
configuration. Which two configuration commands resolve the issue? (Choose two)
An engineer is trying to add an encrypted user password that should not be visible in the router
configuration. Which two configuration commands resolve the issue? (Choose two)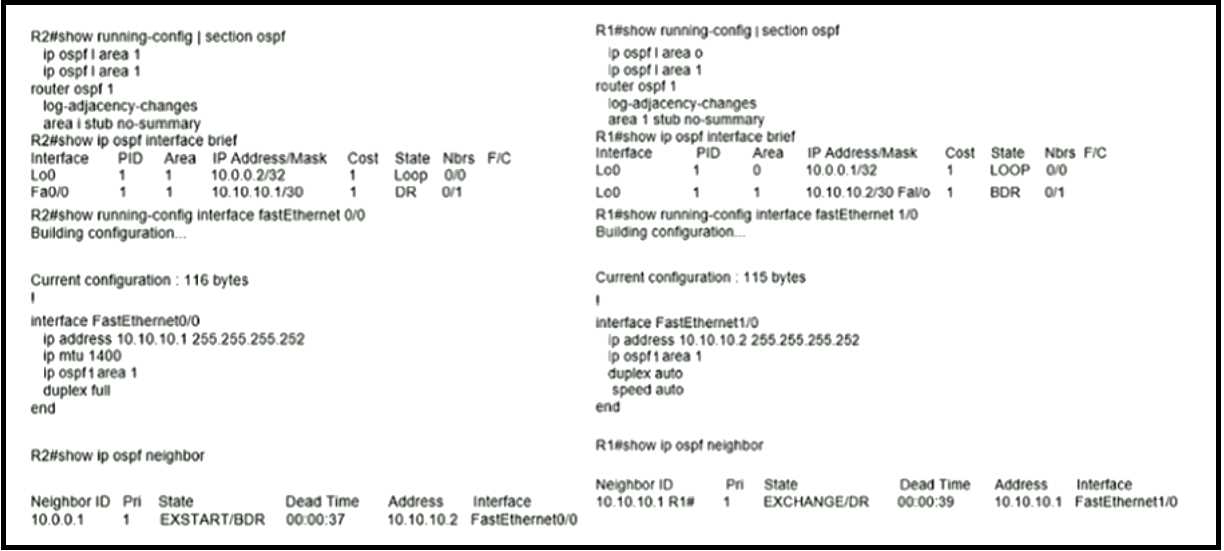 Which action restores OSPF adjacency between R1 and R2?
Which action restores OSPF adjacency between R1 and R2?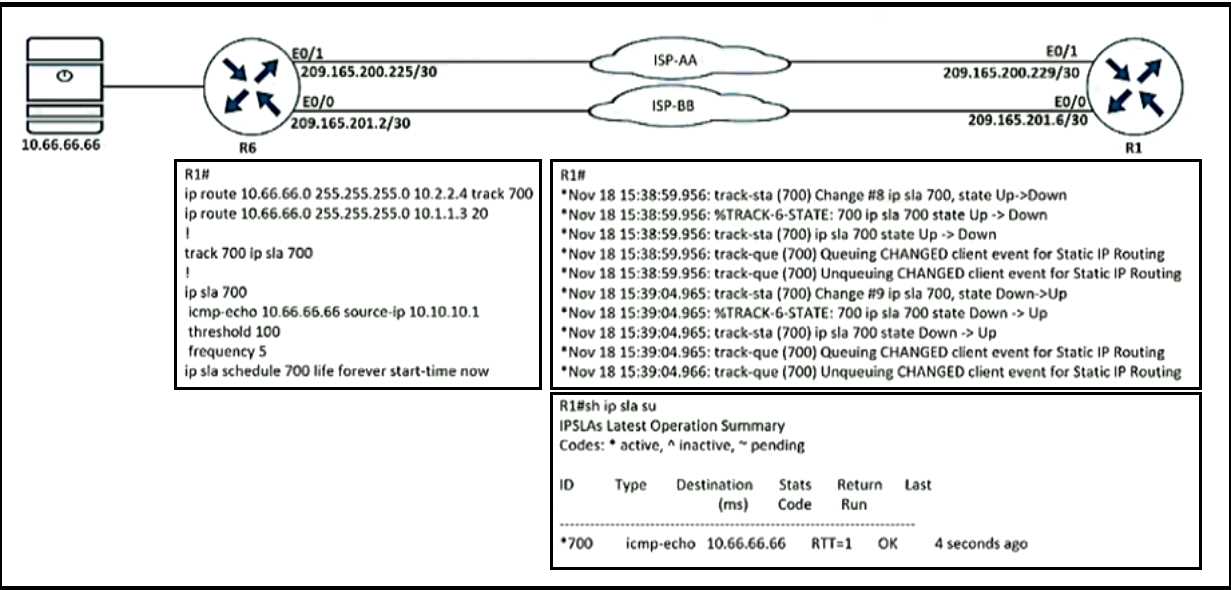 R1 is configured with IP SLA to check the availability of the server behind R6 but it kept failing. Which
configuration resolves the issue?
R1 is configured with IP SLA to check the availability of the server behind R6 but it kept failing. Which
configuration resolves the issue?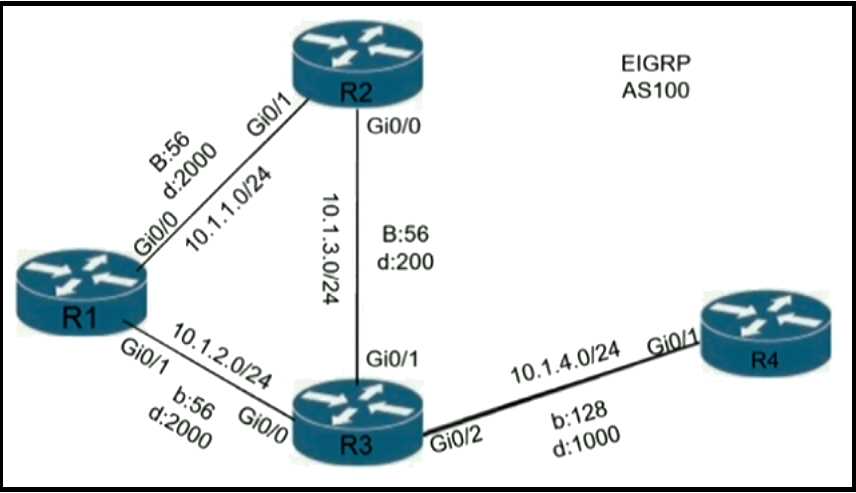 A loop occurs between R1, R2, and R3 while EIGRP is run with poison reverse enabled. Which action
prevents the loop between R1, R2, and R3?
A loop occurs between R1, R2, and R3 while EIGRP is run with poison reverse enabled. Which action
prevents the loop between R1, R2, and R3?


Amira (verified owner) –
I was unsure at first, but Cert Empire turned out to be a solid choice. The content was accurate and well-organized, definitely worth it.
Manohar Mehra (verified owner) –
I got the 300-410 materials straight away after checkout. Cert Empire had everything running smooth—no delays, no download problems. Being able to jump in and start studying within minutes really helped me stay on track with my routine.