Arcitura S90.20
Q: 1
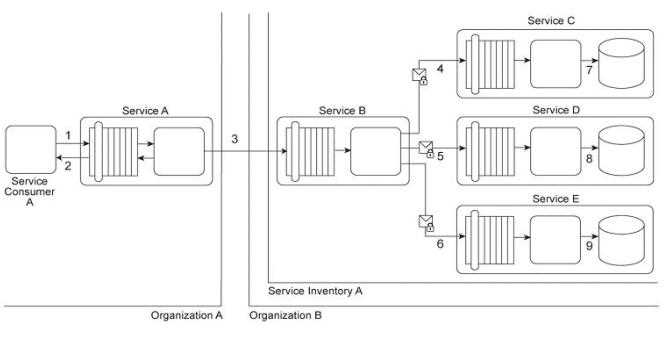
Service Consumer A sends a request to Service A (1). Service A replies with an acknowledgement
message (2) and then processes the request and sends a request message to Service B (3). This
message contains confidential financial data. Service B sends three different request messages
together with its security credentials to Services C .D .and E (4, 5, 6). Upon successful authentication,
Services C .D .and E store the data from the message in separate databases (7.8, 9). Services B .C .D,
and E belong to Service Inventory A, which further belongs to Organization B .Service Consumer A
and Service A belong to Organization A .Organization B decides to create a new service inventory
(Service Inventory B) for services that handle confidential data. Access to these services is restricted
by allocating Service Inventory B its own private network. Access to this private network is further
restricted by a dedicated firewall. Services C, D and E are moved into Service Inventory B, and as a
result. Service B can no longer directly access these services. How can this architecture be changed to
allow Service B to access Services C, D and E in a manner that does not jeopardize the security of
Service Inventory B while also having a minimal impact on the service composition's performance?

Options
Q: 2
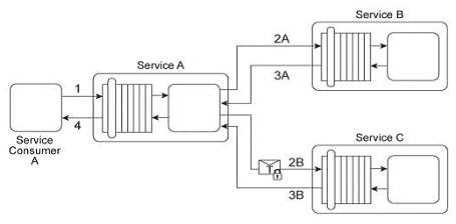
Service A is a publically accessible service that provides free multimedia retrieval capabilities to a
range of service consumers. To carry out this functionality, Service A is first invoked by Service
Consumer A (1). Based on the nature of the request message received from Service Consumer A,
Service A either invokes Service B or Service C .When Service B is invoked by Service A (2A) it
retrieves data from publicly available sources (not shown) and responds with the requested data
(3A). When Service C is invoked by Service A (2B) it retrieves data from proprietary sources within
the IT enterprise (not shown) and responds with the requested data (3B). After receiving a response
from Service B or Service C, Service A sends the retrieved data to Service Consumer A (4). Service B
does not require service consumers to be authenticated, but Service C does require authentication of
service consumers. The service contract for Service A therefore uses WS-Policy alternative policies in
order to express the two different authentication requirements to Service Consumer A .When Service
Consumer A sends a request message (1), Service A determines whether the request requires the
involvement of Service C and then checks to ensure that the necessary security credentials were
received as part of the message. If the credentials provided by Service Consumer A are verified.
Service A creates a signed SAML assertion and sends it with the request message to Service C (2B)
This authentication information is protected by public key encryption However, responses to Service
Consumer A's request message (3B, 4) are not encrypted for performance reasons. The owner of
Service C is planning two changes to the service architecture:
1. A fee will be charged to Service Consumer A (or any service consumer) using Service C .2. The
response messages issued by Service C need to be secured in order to prevent unauthorized access.
An analysis of Service C's usage statistics reveals that a group of service consumers specifically
request the retrieval of multimedia data on a frequent basis. To promote the usage of Service C to
these types of service consumers, the owner of Service C plans to offer a special discount by allowing
unlimited multimedia retrievals for a fixed monthly price. Service consumers that do not subscribe to
this promotion will need to pay for each request individually. It is anticipated that the new promotion
will significantly increase the usage of Service C .The owner of Service C therefore wants to ensure
that the security added to the response messages has a minimal impact on Service C's runtime
performance. What steps can be taken to fulfill these requirements?

Options
Q: 3
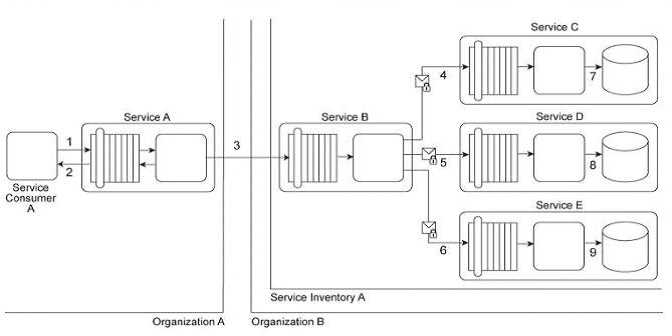
Service Consumer A sends a request to Service A (1). Service A replies with an acknowledgement
message (2) and then processes the request and sends a request message to Service B (3). This
message contains confidential financial data. Service B sends three different request messages
together with its security credentials to Services C, D, and E (4, 5, 6). Upon successful authentication,
Services C, D, and E store the data from the message in separate databases (7, 8, 9) Services B, C, D,
and E belong to Service Inventory A, which further belongs to Organization B .Service Consumer A
and Service A belong to Organization A .The service contracts of Services A and B both comply with
the same XML schema. However, each organization employs different security technologies for their
service architectures. To protect the confidential financial data sent by Service A to Service B, each
organization decides to independently apply the Data Confidentiality and the Data Origin
Authentication patterns to establish message-layer security for external message exchanges.
However, when an encrypted and digitally signed test message is sent by Service A to Service B,
Service B was unable to decrypt the message. Which of the following statements describes a solution
that solves this problem?

Options
Q: 4
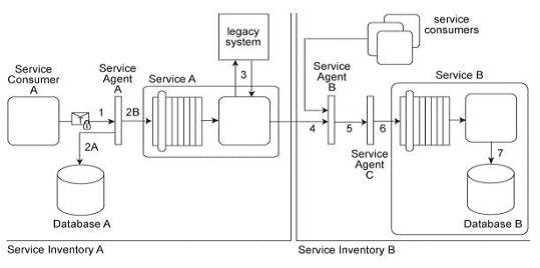
Service Consumer A sends a request message with an authentication token to Service A, but before
the message reaches Service A, it is intercepted by Service Agent A (1). Service Agent A validates the
security credentials and also validates whether the message is compliant with Security Policy A .If
either validation fails, Service Agent A rejects the request message and writes an error log to
Database A (2A). If both validations succeed, the request message is sent to Service A (2B). Service A
retrieves additional data from a legacy system (3) and then submits a request message to Service B
Before arriving at Service B, the request message is intercepted by Service Agent B (4) which
validates its compliance with Security Policy SIB then Service Agent C (5) which validates its
compliance with Security Policy B .If either of these validations fails, an error message is sent back to
Service A .that then forwards it to Service Agent A so that it the error can be logged in Database A
(2A). If both validations succeed, the request message is sent to Service B (6). Service B subsequently
stores the data from the message in Database B (7). Service A and Service Agent A reside in Service
Inventory A .Service B and Service Agents B and C reside in Service Inventory B .Security Policy SIB is
used by all services that reside in Service Inventory B .Service B can also be invoked by other service
consumers from Service Inventory B .Request messages sent by these service consumers must also
be compliant with Security Policies SIB and B .Access to the legacy system in Service Inventory A is
currently only possible via Service A, which means messages must be validated for compliance with
Security Policy A .A new requirement has emerged to allow services from Service Inventory B to
access the legacy system via a new perimeter service that will be dedicated to processing request
messages from services residing in Service Inventory B .Because the legacy system has no security
features, all security processing will need to be carried out by the perimeter service. However, there
are parts of Security Policy A that are specific to Service A and do not apply to the legacy system or
the perimeter service. Furthermore, response messages sent by the perimeter service to services
from Service Inventory B will still need to be validated for compliance to Security Policy B and
Security Policy SIB .How can the Policy Centralization pattern be correctly applied without
compromising the policy compliance requirements of services in both service inventories?

Options
Q: 5
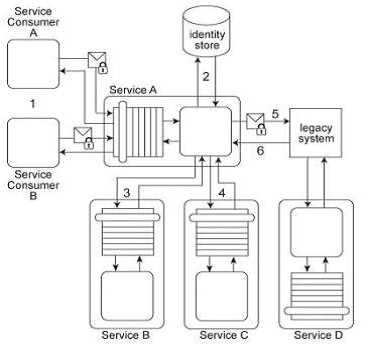
Service A has two specific service consumers, Service Consumer A and Service Consumer B (1). Both
service consumers are required to provide security credentials in order for Service A to perform
authentication using an identity store (2). If a service consumer's request message is successfully
authenticated, Service A processes the request by exchanging messages with Service B (3) and then
Service C (4). With each of these message exchanges, Service A collects data necessary to perform a
query against historical data stored in a proprietary legacy system. Service A's request to the legacy
system must be authenticated (5). The legacy system only provides access control using a single
account. If the request from Service A is permitted, it will be able to access all of the data stored in
the legacy system. If the request is not permitted, none of the data stored in the legacy system can
be accessed. Upon successfully retrieving the requested data (6), Service A generates a response
message that is sent back to either Service Consumer A or B .The legacy system is also used
independently by Service D without requiring any authentication. Furthermore, the legacy system
has no auditing feature and therefore cannot record when data access from Service A or Service D
occurs. If the legacy system encounters an error when processing a request, it generates descriptive
error codes. This service composition architecture needs to be upgraded in order to fulfill the
following new security requirements:
1. Service Consumers A and B have different permission levels, and therefore, response messages
sent to a service consumer must only contain data for which the service consumer is authorized.
2. All data access requests made to the legacy system must be logged.
3. Services B and C must be provided with the identity of Service A's service consumer in order to
provide Service A with the requested data.
4. Response messages generated by Service A cannot contain confidential error information about
the legacy system. Which of the following statements provides solutions that satisfy these
requirements?

Options
Q: 6
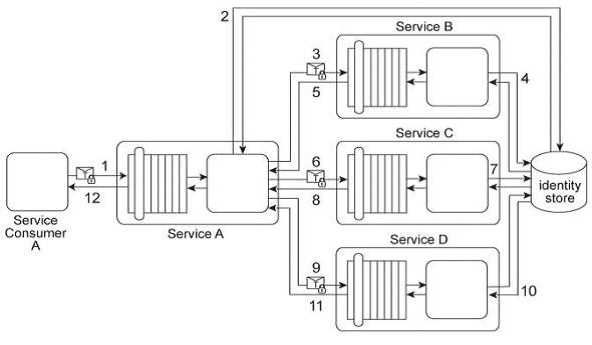
Service Consumer A sends a request message with a Username token to Service A (1). Service B
authenticates the request by verifying the security credentials from the Username token with a
shared identity store (2). To process Service Consumer A's request message, Service A must use
Services B, C, and D .Each of these three services also requires the Username token (3. 6, 9) in order
to authenticate Service Consumer A by using the same shared identity store (4, 7, 10). Upon each
successful authentication, each of the three services (B, C, and D) issues a response message back to
Service A (5, 8, 11). Upon receiving and processing the data in all three response messages, Service A
sends its own response message to Service Consumer A (12). You are asked to redesign this service
composition architecture so that it can still carry out the described message exchanges while
requiring that Service Consumer A only be authenticated once using the identity store. Which of the
following statements describes an accurate solution?

Options
Q: 7
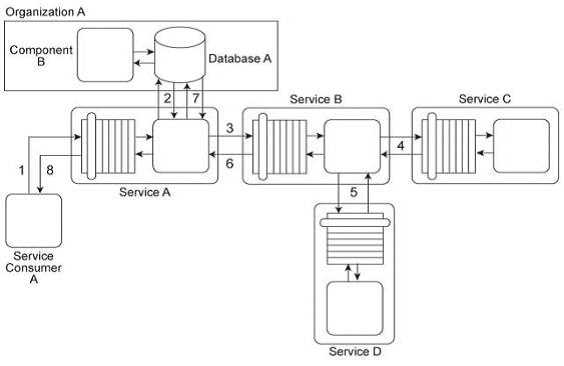
Service Consumer A sends a request message to Service A (1) after which Service A retrieves financial
data from Database A (2). Service A then sends a request message with the retrieved data to Service
B (3). Service B exchanges messages with Service C (4) and Service D (5), which perform a series of
calculations on the data and return the results to Service A .Service A uses these results to update
Database A (7) and finally sends a response message to Service Consumer A (8). Component B has
direct, independent access to Database A and is fully trusted by Database A .Both Component B and
Database A reside within Organization A .Service Consumer A and Services A, B, C, and D are external
to the organizational boundary of Organization A .Service A has recently experienced an increase in
the number of requests from Service Consumer A .However, the owner of Service Consumer A has
denied that Service Consumer A actually sent these requests. Upon further investigation it was
determined that several of these disclaimed requests resulted in a strange behavior in Database A,
including the retrieval of confidential data. The database product used for Database A has no feature
that enables authentication of consumers. Furthermore, the external service composition (Services
A, B, C, D) must continue to operate at a high level of runtime performance. How can this
architecture be improved to avoid unauthenticated access to Database A while minimizing the
performance impact on the external service composition?

Options
Q: 8
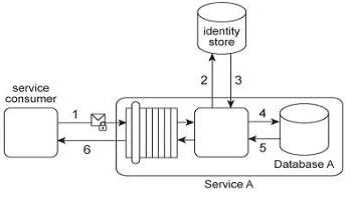
Service A provides a data access capability that can be used by a variety of service consumers. The
database records accessed by Service A are classified as either private or public. There are two types
of service consumers that use Service A:
Service consumers with public access permissions (allowed to access only public data records) and
service consumers with private access permissions (allowed to access all data records). For
performance reasons the Service A architecture uses a single database, named Database A .Each
record in Database A is classified as either private or public. After Service A is invoked by a service
consumer (1), it authenticates the request message using an identity store and retrieves the
corresponding authorization (2, 3). Once authorized, the service consumer's request is submitted to
Database A (4), which then returns the requested data (5) If the service consumer has private access
permissions, all of the returned data is included in Service A's response message (6). If the service
consumer has public access permissions, then Service A first filters the data in order to remove all
unauthorized private data records before sending to the response message to the service consumer
(6). In addition to retrieving data, Service A's data access capability can be used to update database
records. An investigation recently revealed an information leakage problem that can occur when
service consumers with public access permissions attempt to update the ID value of a database
record The ID values of all database records (private or public) must be unique. When a service
consumer with public access permissions updates a public database record with an ID value that is
already assigned to a private database record, the database returns an error message describing this
conflict. This error text reveals confidential information by stating that the ID value submitted by the
service consumer with public access permissions already exists within a private database record.
What steps can be taken to avoid this problem while preserving the requirement that all database
records (private and public) have unique ID values?

Options
Q: 9
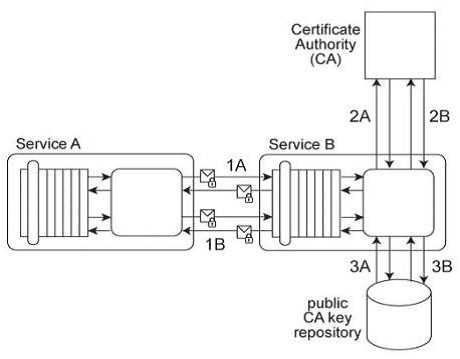
Service A exchanges messages with Service B multiple times during the same runtime service
activity. Communication between Services A and B has been secured using transport-layer security.
With each service request message sent to Service B (1A .IB), Service A includes an X.509 certificate,
signed by an external Certificate Authority (CA). Service B validates the certificate by retrieving the
public key of the CA (2A .2B) and verifying the digital signature of the X.509 certificate. Service B then
performs a certificate revocation check against a separate external CA repository (3A, 3B). No
intermediary service agents reside between Service A and Service B .Service B has recently suffered
from poor runtime performance plus it has been the victim of an access-oriented attack. As a result,
its security architecture must be changed to fulfill the following new requirements:
1. The performance of security-related processing carried out by Service B when communicating with
Service A must be improved.
2. All request messages sent from Service A to Service B must be screened to ensure that they do not
contain malicious content. Which of the following statements describes a solution that fulfills these
requirements?

Options
Q: 10
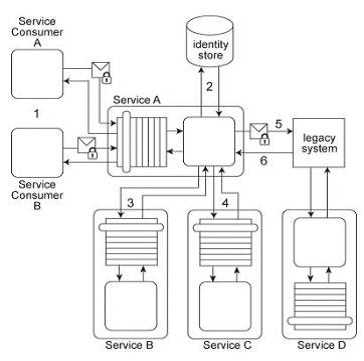
Service A has two specific service consumers, Service Consumer A and Service Consumer B (1). Both
service consumers are required to provide security credentials in order for Service A to perform
authentication using an identity store (2). If a service consumer's request message is successfully
authenticated, Service A processes the request by exchanging messages with Service B (3) and then
Service C (4). With each of these message exchanges, Service A collects data necessary to perform a
query against historical data stored in a proprietary legacy system. Service A's request to the legacy
system must be authenticated (5). The legacy system only provides access control using a single
account. If the request from Service A is permitted, it will be able to access all of the data stored in
the legacy system. If the request is not permitted, none of the data stored in the legacy system can
be accessed. Upon successfully retrieving the requested data (6), Service A generates a response
message that is sent back to either Service Consumer A or B .The legacy system is also used
independently by Service D without requiring any authentication. Furthermore, the legacy system
has no auditing feature and therefore cannot record when data access from Service A or Service D
occurs. If the legacy system encounters an error when processing a request, it generates descriptive
error codes. This service composition architecture needs to be upgraded in order to fulfill the
following new security requirements:
1. Service Consumers A and B have different access permissions and therefore, data received from
the legacy system must be filtered prior to issuing a response message to one of these two service
consumers.
2. Service Consumer A's request messages must be digitally signed, whereas request messages from
Service Consumer B do not need to be digitally signed. Which of the following statements describes a
solution that fulfills these requirements?

Options
Question 1 of 10

