Netskope NSK300
Q: 1
You deployed Netskope Cloud Security Posture Management (CSPM) using pre-defined benchmark
rules to monitor your cloud posture in AWS, Azure, and GCP. You are asked to assess if you can
extend the Netskope CSPM solution by creating custom rules for each environment.
Which statement is correct?
Options
Q: 2
You are asked to create a customized restricted administrator role in your Netskope tenant for a
newly hired employee. Which two statements are correct in this scenario? (Choose two.)
Options
Q: 3
Your customer is currently using Directory Importer with Active Directory (AD) to provision users to Nelskope. They have recently acquired three new companies ( A. B. and C) and want to onboard users from the companies onto the NetsKope platform. Information about the companies is shown below. - Company A uses Active Directory. -- Company B uses Azure AD. -- Company C uses Okta Universal Directory. Which statement is correct in this scenario?
Options
Q: 4
What is a Fast Scan component of Netskope Threat Detection?
Options
Q: 5
You are using Netskope CSPM for security and compliance audits across your multi-cloud
environments. To decrease the load on the security operations team, you are researching how to
auto-re mediate some of the security violations found in low-risk environments.
Which statement is correct in this scenario?
Options
Q: 6
You are deploying the Netskope Client to Windows devices. The following command line would be
used to install the client MSI file:
 In this scenario, what is referring to in the command line?
In this scenario, what is referring to in the command line?
 In this scenario, what is referring to in the command line?
In this scenario, what is referring to in the command line?Options
Q: 7
Review the exhibit.
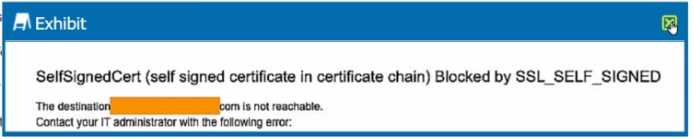 You are the proxy administrator for a medical devices company. You recently changed a pilot group of
users from cloud app steering to all Web traffic. Pilot group users have started to report that they
receive the error shown in the exhibit when attempting to access the company intranet site that is
publicly available. During troubleshooting, you realize that this site uses your company's internal
certificate authority for SSL certificates.
Which three statements describe ways to solve this issue? (Choose three.)
You are the proxy administrator for a medical devices company. You recently changed a pilot group of
users from cloud app steering to all Web traffic. Pilot group users have started to report that they
receive the error shown in the exhibit when attempting to access the company intranet site that is
publicly available. During troubleshooting, you realize that this site uses your company's internal
certificate authority for SSL certificates.
Which three statements describe ways to solve this issue? (Choose three.)
 You are the proxy administrator for a medical devices company. You recently changed a pilot group of
users from cloud app steering to all Web traffic. Pilot group users have started to report that they
receive the error shown in the exhibit when attempting to access the company intranet site that is
publicly available. During troubleshooting, you realize that this site uses your company's internal
certificate authority for SSL certificates.
Which three statements describe ways to solve this issue? (Choose three.)
You are the proxy administrator for a medical devices company. You recently changed a pilot group of
users from cloud app steering to all Web traffic. Pilot group users have started to report that they
receive the error shown in the exhibit when attempting to access the company intranet site that is
publicly available. During troubleshooting, you realize that this site uses your company's internal
certificate authority for SSL certificates.
Which three statements describe ways to solve this issue? (Choose three.)Options
Q: 8
Review the exhibit.
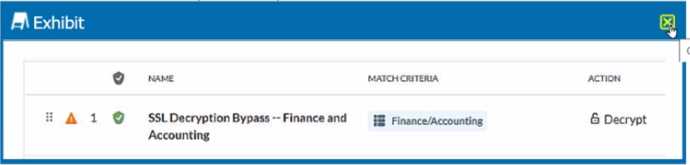 You created an SSL decryption policy to bypass the inspection of financial and accounting Web
categories. However, you still see banking websites being inspected.
Referring to the exhibit, what are two possible causes of this behavior? (Choose two.)
You created an SSL decryption policy to bypass the inspection of financial and accounting Web
categories. However, you still see banking websites being inspected.
Referring to the exhibit, what are two possible causes of this behavior? (Choose two.)
 You created an SSL decryption policy to bypass the inspection of financial and accounting Web
categories. However, you still see banking websites being inspected.
Referring to the exhibit, what are two possible causes of this behavior? (Choose two.)
You created an SSL decryption policy to bypass the inspection of financial and accounting Web
categories. However, you still see banking websites being inspected.
Referring to the exhibit, what are two possible causes of this behavior? (Choose two.)Options
Q: 9
You are troubleshooting an issue with users who are unable to reach a financial SaaS application
when their traffic passes through Netskope. You determine that this is because of IP restrictions in
place with the SaaS vendor. You are unable to add Netskope's IP ranges at this time, but need to
allow the traffic.
How would you allow this traffic?
Options
Q: 10
You are implementing a solution to deploy Netskope for machine traffic in an AWS account across
multiple VPCs. You want to deploy the least amount of tunnels while providing connectivity for all
VPCs.
How would you accomplish this task?
Options
Question 1 of 10

