NSE7_OTS-7.2.pdf
Q: 1
[OT Network Fundamentals and Segmentation]
Refer to the exhibit.
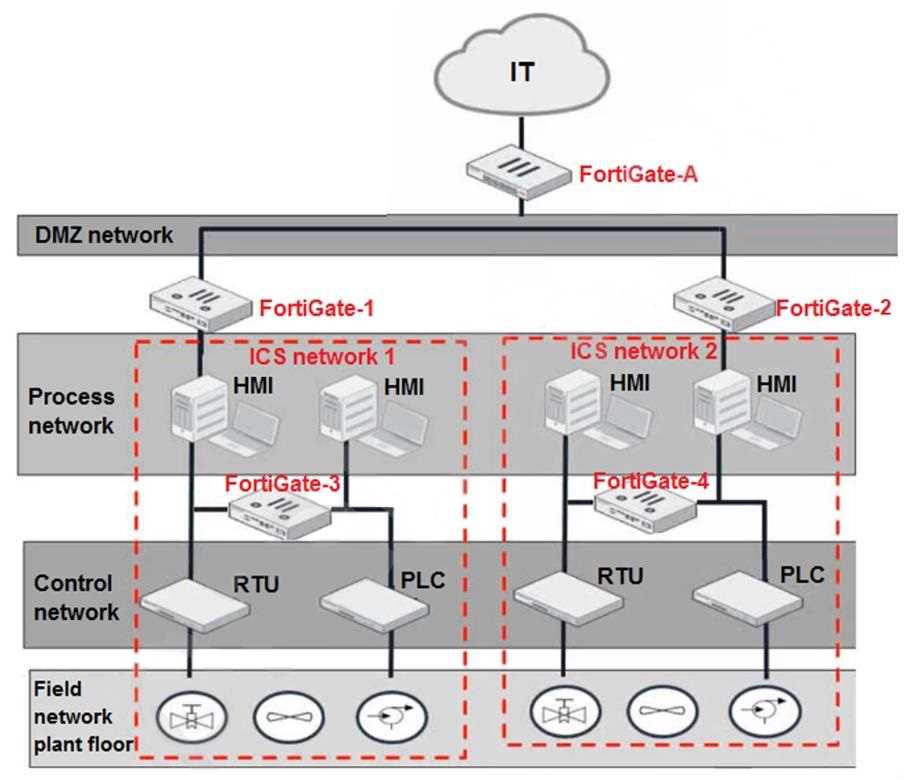 Based on the topology designed by the OT architect, which two statements about implementing OT
security are true? (Choose two.)
Based on the topology designed by the OT architect, which two statements about implementing OT
security are true? (Choose two.)
 Based on the topology designed by the OT architect, which two statements about implementing OT
security are true? (Choose two.)
Based on the topology designed by the OT architect, which two statements about implementing OT
security are true? (Choose two.)Options
Q: 2
[OT Network Fundamentals and Segmentation]
A FortiGate device is newly deployed as the edge gateway of an OT network security fabric. The
downstream FortiGate devices are also newly deployed as Security Fabric leafs to protect the control
area zone.
With no additional essential networking devices, and to implement micro-segmentation on this OT
network, what configuration must the OT network architect apply to control intra-VLAN traffic?
Options
Q: 3
[Fortinet Products for OT Security]
Which three common breach points can be found in a typical OT environment? (Choose three.)
Options
Q: 4
[Fortinet Products for OT Security]
Operational technology (OT) network analysts run different levels of reports to identify failures that
could put the network at risk Some of these reports may be related to device performance
Which FortiSIEM reporting method helps identify device failures?
Options
Q: 5
[Fortinet Products for OT Security]
An OT supervisor has configured LDAP and FSSO for the authentication. The goal is that all the users
be authenticated against passive authentication first and, if passive authentication is not successful,
then users should be challenged with active authentication.
What should the OT supervisor do to achieve this on FortiGate?
Options
Q: 6
[Fortinet Products for OT Security]
What are two benefits of a Nozomi integration with FortiNAC? (Choose two.)
Options
Q: 7
[Fortinet Products for OT Security]
How can you achieve remote access and internet availability in an OT network?
Options
Q: 8
[OT Network Fundamentals and Segmentation]
Refer to the exhibit.
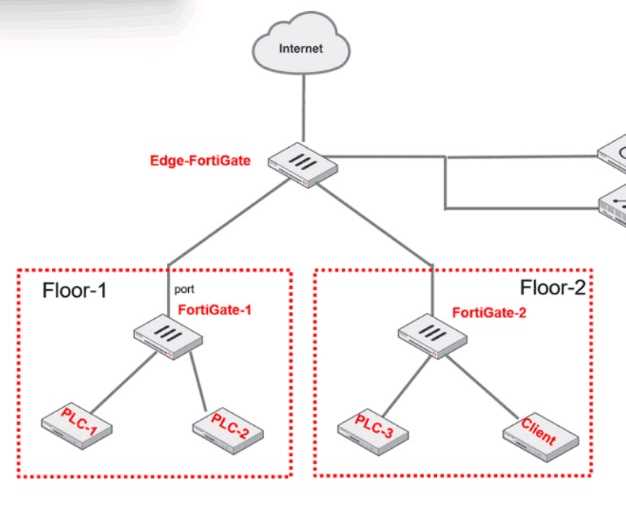 PLC-3 and CLIENT can send traffic to PLC-1 and PLC-2. FGT-2 has only one software switch (SSW-1)
connecting both PLC-3 and CLIENT. PLC-3 and CLIENT can send traffic to each other at the Layer 2
level.
What must the OT admin do to prevent Layer 2-level communication between PLC-3 and CLIENT?
PLC-3 and CLIENT can send traffic to PLC-1 and PLC-2. FGT-2 has only one software switch (SSW-1)
connecting both PLC-3 and CLIENT. PLC-3 and CLIENT can send traffic to each other at the Layer 2
level.
What must the OT admin do to prevent Layer 2-level communication between PLC-3 and CLIENT?
 PLC-3 and CLIENT can send traffic to PLC-1 and PLC-2. FGT-2 has only one software switch (SSW-1)
connecting both PLC-3 and CLIENT. PLC-3 and CLIENT can send traffic to each other at the Layer 2
level.
What must the OT admin do to prevent Layer 2-level communication between PLC-3 and CLIENT?
PLC-3 and CLIENT can send traffic to PLC-1 and PLC-2. FGT-2 has only one software switch (SSW-1)
connecting both PLC-3 and CLIENT. PLC-3 and CLIENT can send traffic to each other at the Layer 2
level.
What must the OT admin do to prevent Layer 2-level communication between PLC-3 and CLIENT?Options
Q: 9
[OT Network Fundamentals and Segmentation]
As an OT network administrator, you are managing three FortiGate devices that each protect
different levels on the Purdue model. To increase traffic visibility, you are required to implement
additional security measures to detect exploits that affect PLCs.
Which security sensor must implement to detect these types of industrial exploits?
Options
Q: 10
[Industrial Protocols and Risk Assessment]
What are two critical tasks the OT network auditors must perform during OT network risk assessment
and management? (Choose two.)
Options
Question 1 of 10

