Juniper JN0-335 Dumps.pdf
Q: 1
You are troubleshooting unexpected issues on your JIMS server due to out of order event log
timestamps.
Which action should you take to solve this issue?
Options
Q: 2
You administer a JSA host and want to include a rule that sets a threshold for excessive firewall
denies and sends an SNMP trap after receiving related syslog messages from an SRX Series firewall.
Which JSA rule type satisfies this requirement?
Options
Q: 3
Which two statements are correct about a policy scheduler? (Choose two.)
Options
Q: 4
You want to permit access to an application but block application sub-Which two security policy
features provide this capability? (Choose two.)
Options
Q: 5
Which two statements are correct when considering IPS rule base evaluation? (Choose two.)
Options
Q: 6
You are asked to block malicious applications regardless of the port number being used.
In this scenario, which two application security features should be used? (Choose two.)
Options
Q: 7
Click the Exhibit button.
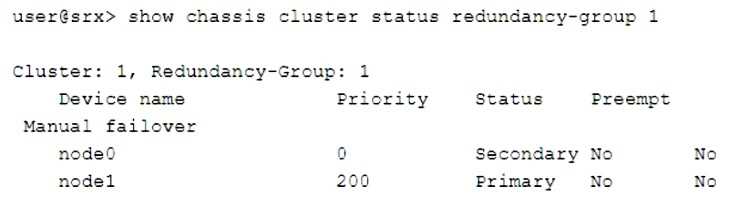 Which two statements describe the output shown in the exhibit? (Choose two.)
Which two statements describe the output shown in the exhibit? (Choose two.)
 Which two statements describe the output shown in the exhibit? (Choose two.)
Which two statements describe the output shown in the exhibit? (Choose two.)Options
Q: 8
Your company is using the Juniper ATP Cloud free model. The current inspection profile is set at 10
MB You are asked to configure ATP Cloud so that executable files up to 30 MB can be scanned while
at the same time minimizing the change in scan time for other file types.
Which configuration should you use in this scenario?
Options
Q: 9
Which two statements about unified security policies are correct? (Choose two.)
Options
Q: 10
Which sequence does an SRX Series device use when implementing stateful session security policies
using Layer 3 routes?
Options
Question 1 of 10

