GIAC GSEC
Q: 1
What technique makes it difficult for attackers to predict the memory address space location for code
execution?
Options
Q: 2
When an IIS filename extension is mapped, what does this mean?
Options
Q: 3
Which of the following SIP methods is used to setup a new session and add a caller?
Options
Q: 4
An IT security manager is trying to quickly assess the risks associated with not implementing a
corporate firewall system. What sort of risk assessment is most appropriate?
Options
Q: 5
You work as a Network Administrator for Net World Inc. The company has a Linux-based network.
For testing purposes, you have configured a default IP-table with several filtering rules. You want to
reconfigure the table. For this, you decide to remove the rules from all the chains in the table. Which
of the following commands will you use?
Options
Q: 6
You have set up a local area network for your company. Your firewall separates your network into
several sections: a DMZ with semi-public servers (web, dns, email) and an intranet with private
servers. A penetration tester gains access to both sections and installs sniffers in each. He is able to
capture network traffic for all the devices in the private section but only for one device (the device
with the sniffer) in the DMZ. What can be inferred about the design of the system?
Options
Q: 7
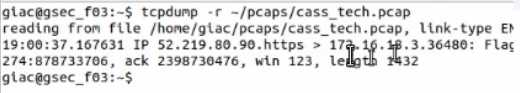
Open the MATE terminal and use the tcpdump program to read - /pcaps /cass tech.pcap. What is the source port number? 
Options
Q: 8
What is TRUE about Workgroups and Domain Controllers?
Options
Q: 9
What is a recommended defense against SQL injection, OS injection, and buffer overflows?
Options
Q: 10
Which of the following services resolves host name to IP Address?
Options
Question 1 of 10

