GIAC GISP
Q: 1
Which of the following ports is used by a BOOTP server?
Options
Q: 2
Which of the following are based on malicious code?
Each correct answer represents a complete solution. Choose two.
Options
Q: 3
You are responsible for a Microsoft based network. Your servers are all clustered. Which of the
following are the likely reasons for the clustering?
Each correct answer represents a complete solution. Choose two.
Options
Q: 4
Which of the following statements about role-based access control (RBAC) model is true?
Options
Q: 5
Which of the following is a source port forwarder and redirector tool?
Options
Q: 6
Which of the following statements about DMZ are true?
Each correct answer represents a complete solution. Choose two.
Options
Q: 7
Which of the following is a formula, practice, process, design, instrument, pattern, or compilation of
information which is not generally known, but by which a business can obtain an economic
advantage over its competitors?
Options
Q: 8
Which of the following encryption methods comes under symmetric encryption algorithm?
Each correct answer represents a complete solution. Choose three.
Options
Q: 9
Which of the following terms is used for a router that filters traffic before it is passed to the firewall?
Options
Q: 10
ORDER LIST Mark works as a Network Administrator for Infonet Inc. The company has a Windows 2003 domain- based network. The network has three Windows 2003 member servers and 200 Windows XP Professional client computers. Mark configures a member server for dial-up access on the network. The company issues smart cards to all users who have dial-up access. Mark wants to enable the users to use the smart cards for remote access authentication. Choose the required steps to accomplish the task. 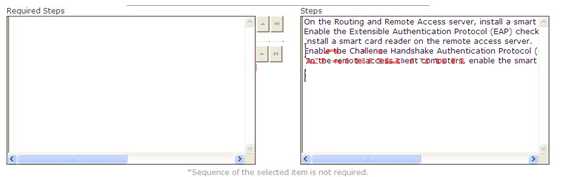
Your Answer
Question 1 of 10

