GIAC GCED
Q: 1
Which action would be the responsibility of the First Responder once arriving at the scene of a
suspected incident as part of a Computer Security Incident Response Plan (CSIRP)?
Options
Q: 2
An incident response team investigated a database breach, and determined it was likely the result of
an internal user who had a default password in place. The password was changed. A week later, they
discover another loss of database records. The database admin provides logs that indicate the attack
came from the front-end web interface. Where did the incident response team fail?
Options
Q: 3
Throughout the week following a new IPS deployment, nearly every user on the protected subnet
submits helpdesk tickets regarding network performance and not being able to access several critical
resources. What is the most likely reason for the performance issues?
Options
Q: 4
Which type of attack could be used to obtain IOS router configuration files without a valid user
password?
Options
Q: 5
You have been tasked with searching for Alternate Data Streams on the following collection of
Windows partitions; 2GB FAT16, 6GB FAT32, and 4GB NTFS. How many total Gigabytes and partitions
will you need to search?
Options
Q: 6
When running a Nmap UDP scan, what would the following output indicate?
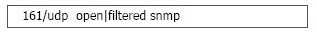
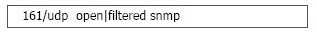
Options
Q: 7
What is the BEST sequence of steps to remove a bot from a system?
Options
Q: 8
A company classifies data using document footers, labeling each file with security labels “Public”,
“Pattern”, or “Company Proprietary”. A new policy forbids sending “Company Proprietary” files via
email. Which control could help security analysis identify breaches of this policy?
Options
Q: 9
The matrix in the screen shot below would be created during which process?
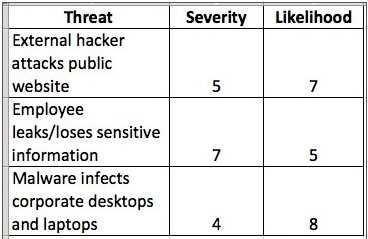

Options
Q: 10
A legacy server on the network was breached through an OS vulnerability with no patch available.
The server is used only rarely by employees across several business units. The theft of information
from the server goes unnoticed until the company is notified by a third party that sensitive
information has been posted on the Internet. Which control was the first to fail?
Options
Question 1 of 10

