FCP_FCT_AD-7.2.pdf
Q: 1
ZTNA Network Topology
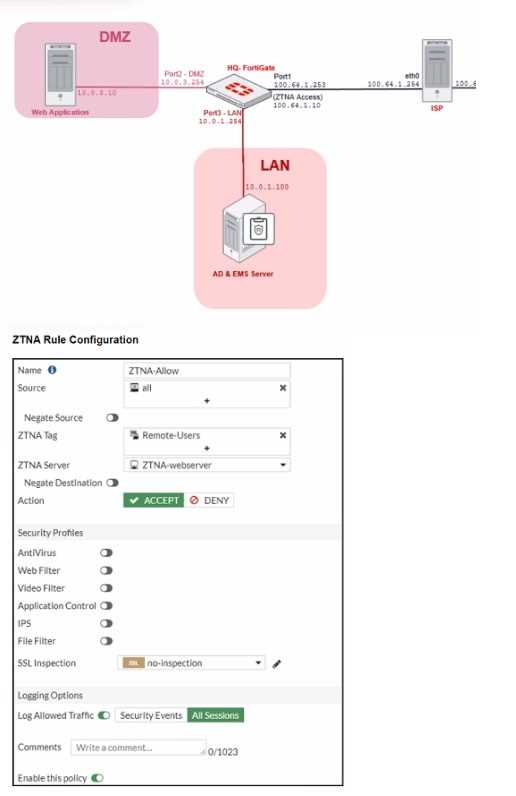 Refer to the exhibits, which show a network topology diagram of ZTNA proxy access and the ZTNA
rule configuration.
An administrator runs the diagnose endpoint record list CLI command on FortiGate to check Remote-
Client endpoint information, however Remote-Client is not showing up in the endpoint record list.
What is the cause of this issue?
Refer to the exhibits, which show a network topology diagram of ZTNA proxy access and the ZTNA
rule configuration.
An administrator runs the diagnose endpoint record list CLI command on FortiGate to check Remote-
Client endpoint information, however Remote-Client is not showing up in the endpoint record list.
What is the cause of this issue?
 Refer to the exhibits, which show a network topology diagram of ZTNA proxy access and the ZTNA
rule configuration.
An administrator runs the diagnose endpoint record list CLI command on FortiGate to check Remote-
Client endpoint information, however Remote-Client is not showing up in the endpoint record list.
What is the cause of this issue?
Refer to the exhibits, which show a network topology diagram of ZTNA proxy access and the ZTNA
rule configuration.
An administrator runs the diagnose endpoint record list CLI command on FortiGate to check Remote-
Client endpoint information, however Remote-Client is not showing up in the endpoint record list.
What is the cause of this issue?Options
Q: 2
Refer to the exhibit, which shows FortiClient EMS deployment, profiles.
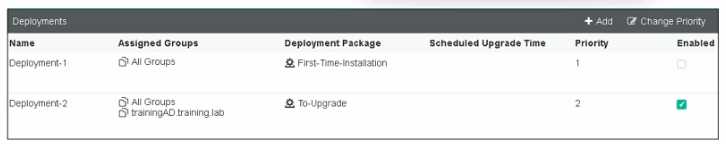 When an administrator creates a deployment profile on FortiClient EMS. which statement about the
deployment profile is true?
When an administrator creates a deployment profile on FortiClient EMS. which statement about the
deployment profile is true?
 When an administrator creates a deployment profile on FortiClient EMS. which statement about the
deployment profile is true?
When an administrator creates a deployment profile on FortiClient EMS. which statement about the
deployment profile is true?Options
Q: 3
Exhibit.
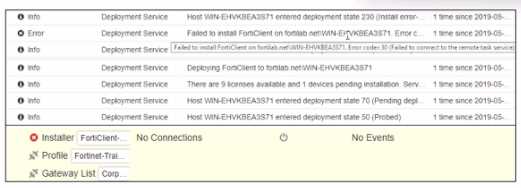 Based on the logs shown in the exhibit, why did FortiClient EMS tail to install FortiClient on the
endpoint?
Based on the logs shown in the exhibit, why did FortiClient EMS tail to install FortiClient on the
endpoint?
 Based on the logs shown in the exhibit, why did FortiClient EMS tail to install FortiClient on the
endpoint?
Based on the logs shown in the exhibit, why did FortiClient EMS tail to install FortiClient on the
endpoint?Options
Q: 4
FortiClient EMS endpoint policies
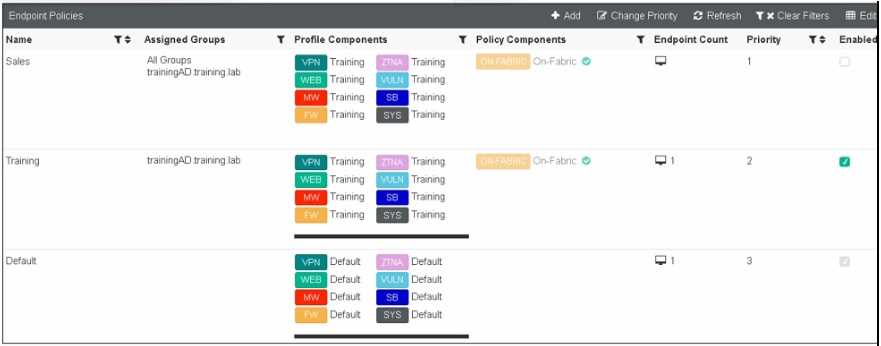 Refer to the exhibit, which shows multiple endpoint policies on FortiClient EMS. Which policy is
applied to the endpoint in the AD group trainingAD
Refer to the exhibit, which shows multiple endpoint policies on FortiClient EMS. Which policy is
applied to the endpoint in the AD group trainingAD
 Refer to the exhibit, which shows multiple endpoint policies on FortiClient EMS. Which policy is
applied to the endpoint in the AD group trainingAD
Refer to the exhibit, which shows multiple endpoint policies on FortiClient EMS. Which policy is
applied to the endpoint in the AD group trainingADOptions
Q: 5
What does FortiClient do as a fabric agent? (Choose two.)
Options
Q: 6
Which two statements are true about ZTNA? {Choose two.)
Options
Q: 7
Refer to the exhibit.
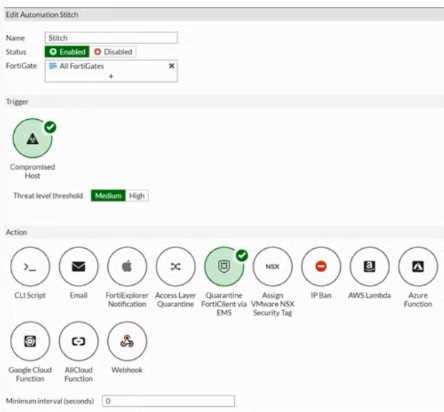 Based on the Security Fabric automation settings, what action will be taken on compromised
endpoints?
Based on the Security Fabric automation settings, what action will be taken on compromised
endpoints?
 Based on the Security Fabric automation settings, what action will be taken on compromised
endpoints?
Based on the Security Fabric automation settings, what action will be taken on compromised
endpoints?Options
Q: 8
In a ForliSandbox integration, what does the remediation option do?
Options
Q: 9
Which two VPN types can a FortiClient endpoint user inmate from the Windows command prompt?
(Choose two)
Options
Q: 10
An administrator is required to maintain a software vulnerability on the endpoints, without showing
the feature on the FortiClient. What must the administrator do to achieve this requirement?
Options
Question 1 of 10

