Trend DEEP SECURITY PROFESSIONAL
Q: 1
Which of the following statements is true regarding the Intrusion Prevention Protection Module?
Options
Q: 2
A Recommendation Scan is run to determine which Intrusion Prevention rules are appropriate for a Server. The scan is configured to apply the suggested rules automatically and ongoing scans are enabled. Some time later, an operating system patch is applied. How can you de-termine which Intrusion Prevention rules are no longer needed on this Server?
Options
Q: 3
What is the purpose of the Deep Security Relay?
Options
Q: 4
Which of the following statements is true regarding Event Tagging?
Options
Q: 5
Which of the following correctly identifies the order of the steps used by the Web Reputation
Protection Module to determine if access to a web site should be allowed?
Options
Q: 6
Which of the following operations makes use of the Intrusion Prevention Protection Module?
Options
Q: 7
In the policy displayed in the exhibit, the state of the Web Reputation Protection Module is set to
"Inherited (On)", while the state for the other Protection Module is set to "On". Why is the Web
Reputation Protection Module displayed differently than the other Protection Modules.
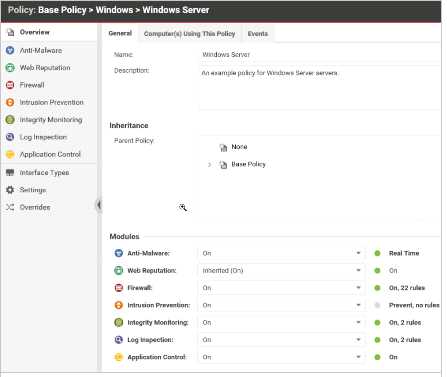

Options
Q: 8
The "Protection Source when in Combined Mode" settings are configured for a virtual machine as in
the exhibit. You would like to enable Application Control on this virtual machine, but there is no
corresponding setting displayed. Why?
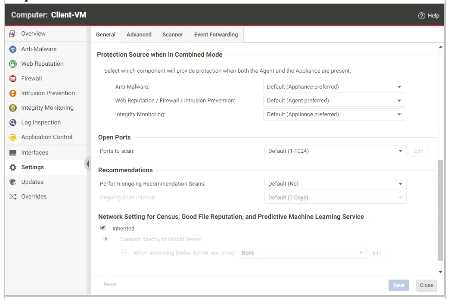

Options
Q: 9
The details for an event are displayed in the exhibit. Based on these details, which Protection Module
generated the event?
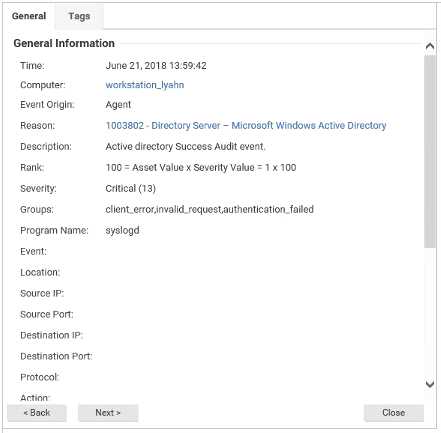

Options
Q: 10
Policies in Deep Security can include a Context value. Which of the following statements re-garding
Context is correct?
Options
Question 1 of 10

