SNOWFLAKE ARA C01
Q: 1
Assuming all Snowflake accounts are using an Enterprise edition or higher, in which development
and testing scenarios would be copying of data be required, and zero-copy cloning not be suitable?
(Select TWO).
Options
Q: 2
Which of the following ingestion methods can be used to load near real-time data by using the
messaging services provided by a cloud provider?
Options
Q: 3
What built-in Snowflake features make use of the change tracking metadata for a table? (Choose
two.)
Options
Q: 4
A table contains five columns and it has millions of records. The cardinality distribution of the
columns is shown below:
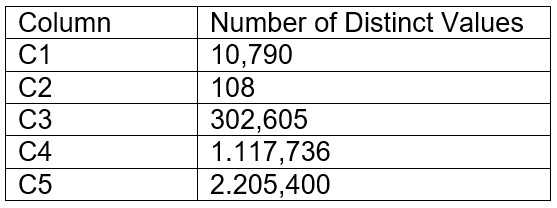 Column C4 and C5 are mostly used by SELECT queries in the GROUP BY and ORDER BY clauses.
Whereas columns C1, C2 and C3 are heavily used in filter and join conditions of SELECT queries.
The Architect must design a clustering key for this table to improve the query performance.
Based on Snowflake recommendations, how should the clustering key columns be ordered while
defining the multi-column clustering key?
Column C4 and C5 are mostly used by SELECT queries in the GROUP BY and ORDER BY clauses.
Whereas columns C1, C2 and C3 are heavily used in filter and join conditions of SELECT queries.
The Architect must design a clustering key for this table to improve the query performance.
Based on Snowflake recommendations, how should the clustering key columns be ordered while
defining the multi-column clustering key?
 Column C4 and C5 are mostly used by SELECT queries in the GROUP BY and ORDER BY clauses.
Whereas columns C1, C2 and C3 are heavily used in filter and join conditions of SELECT queries.
The Architect must design a clustering key for this table to improve the query performance.
Based on Snowflake recommendations, how should the clustering key columns be ordered while
defining the multi-column clustering key?
Column C4 and C5 are mostly used by SELECT queries in the GROUP BY and ORDER BY clauses.
Whereas columns C1, C2 and C3 are heavily used in filter and join conditions of SELECT queries.
The Architect must design a clustering key for this table to improve the query performance.
Based on Snowflake recommendations, how should the clustering key columns be ordered while
defining the multi-column clustering key?Options
Q: 5
How do Snowflake databases that are created from shares differ from standard databases that are
not created from shares? (Choose three.)
Options
Q: 6
How can an Architect enable optimal clustering to enhance performance for different access paths
on a given table?
Options
Q: 7
What is a valid object hierarchy when building a Snowflake environment?
Options
Q: 8
Which feature provides the capability to define an alternate cluster key for a table with an existing
cluster key?
Options
Q: 9
What considerations need to be taken when using database cloning as a tool for data lifecycle
management in a development environment? (Select TWO).
Options
Q: 10
An Architect has a VPN_ACCESS_LOGS table in the SECURITY_LOGS schema containing timestamps of
the connection and disconnection, username of the user, and summary statistics.
What should the Architect do to enable the Snowflake search optimization service on this table?
Options
Question 1 of 10

