Cisco 350-701
Q: 1
[Security Concepts]
What are two DDoS attack categories? (Choose two)
Options
Q: 2
[Security Concepts]
Which Cisco DNA Center Intent API action is used to retrieve the number of devices known to a DNA
Center?
Options
Q: 3
[Security Concepts]
Which technology should be used to help prevent an attacker from stealing usernames and
passwords of users within an organization?
Options
Q: 4
[Security Concepts]
Based on the NIST 800-145 guide, which cloud architecture is provisioned for exclusive use by a
specific group of consumers from different organizations and may be owned, managed, and operated
by one or more of those organizations?
Options
Q: 5
[Security Concepts]
Which algorithm provides asymmetric encryption?
Options
Q: 6
[Security Concepts]
Which security product enables administrators to deploy Kubernetes clusters in air-gapped sites
without needing Internet access?
Options
Q: 7
DRAG DROP [Network Security] Drag and drop the VPN functions from the left onto the description on the right.

Drag & Drop
Q: 8
[Endpoint Protection and Detection]
An engineer needs a solution for TACACS+ authentication and authorization for device
administration.
The engineer also wants to enhance wired and wireless network security by requiring users and
endpoints to
use 802.1X, MAB, or WebAuth. Which product meets all of these requirements?
Options
Q: 9
DRAG DROP [Security Concepts] Drag and drop the features of Cisco ASA with Firepower from the left onto the benefits on the right. 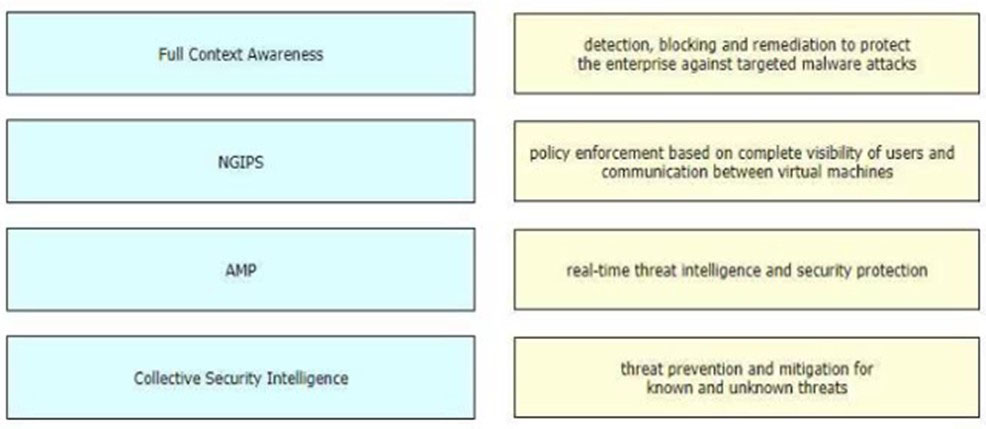
Drag & Drop
Q: 10
DRAG DROP [Security Concepts] Drag and drop the capabilities from the left onto the correct technologies on the right. 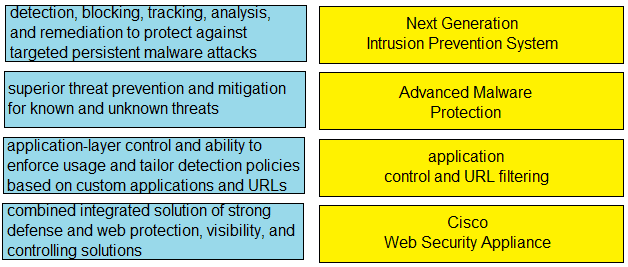
Drag & Drop
Question 1 of 10

