350-201.pdf
Q: 1
A company’s web server availability was breached by a DDoS attack and was offline for 3 hours
because it was not deemed a critical asset in the incident response playbook. Leadership has
requested a risk assessment of the asset. An analyst conducted the risk assessment using the threat
sources, events, and vulnerabilities. Which additional element is needed to calculate the risk?
Options
Q: 2
What is needed to assess risk mitigation effectiveness in an organization?
Options
Q: 3
The physical security department received a report that an unauthorized person followed an
authorized individual to enter a secured premise. The incident was documented and given to a
security specialist to analyze. Which step should be taken at this stage?
Options
Q: 4
What is the purpose of hardening systems?
Options
Q: 5
Refer to the exhibit.
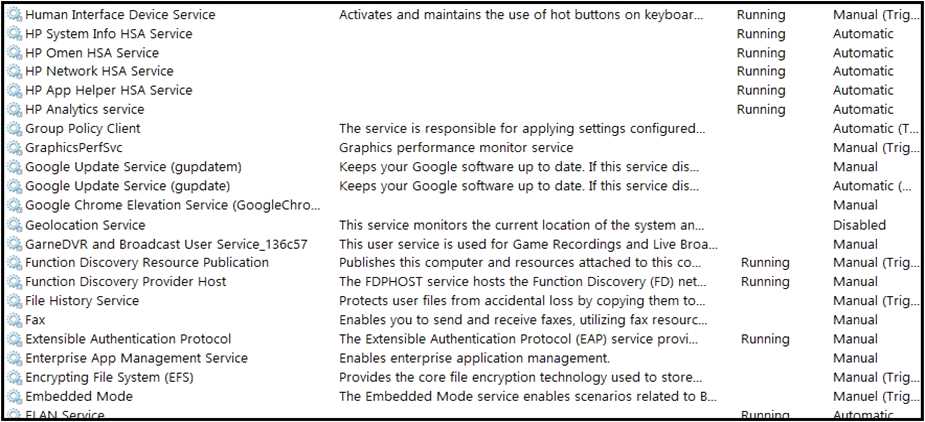 An engineer received multiple reports from employees unable to log into systems with the error: The
Group Policy Client service failed to logon – Access is denied. Through further analysis, the engineer
discovered several unexpected modifications to system settings. Which type of breach is occurring?
An engineer received multiple reports from employees unable to log into systems with the error: The
Group Policy Client service failed to logon – Access is denied. Through further analysis, the engineer
discovered several unexpected modifications to system settings. Which type of breach is occurring?
 An engineer received multiple reports from employees unable to log into systems with the error: The
Group Policy Client service failed to logon – Access is denied. Through further analysis, the engineer
discovered several unexpected modifications to system settings. Which type of breach is occurring?
An engineer received multiple reports from employees unable to log into systems with the error: The
Group Policy Client service failed to logon – Access is denied. Through further analysis, the engineer
discovered several unexpected modifications to system settings. Which type of breach is occurring?Options
Q: 6
An engineer is investigating several cases of increased incoming spam emails and suspicious emails
from the HR and service departments. While checking the event sources, the website monitoring
tool showed several web scraping alerts overnight. Which type of compromise is indicated?
Options
Q: 7
Refer to the exhibit.
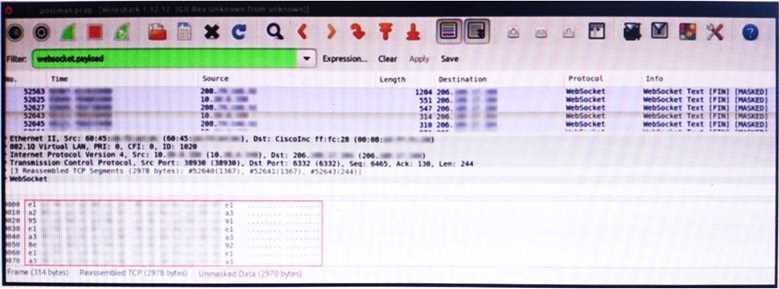 An engineer is analyzing this Vlan0386-int12-117.pcap file in Wireshark after detecting a suspicious
network activity. The origin header for the direct IP connections in the packets was initiated by a
google chrome extension on a WebSocket protocol. The engineer checked message payloads to
determine what information was being sent off-site but the payloads are obfuscated and unreadable.
What does this STIX indicate?
An engineer is analyzing this Vlan0386-int12-117.pcap file in Wireshark after detecting a suspicious
network activity. The origin header for the direct IP connections in the packets was initiated by a
google chrome extension on a WebSocket protocol. The engineer checked message payloads to
determine what information was being sent off-site but the payloads are obfuscated and unreadable.
What does this STIX indicate?
 An engineer is analyzing this Vlan0386-int12-117.pcap file in Wireshark after detecting a suspicious
network activity. The origin header for the direct IP connections in the packets was initiated by a
google chrome extension on a WebSocket protocol. The engineer checked message payloads to
determine what information was being sent off-site but the payloads are obfuscated and unreadable.
What does this STIX indicate?
An engineer is analyzing this Vlan0386-int12-117.pcap file in Wireshark after detecting a suspicious
network activity. The origin header for the direct IP connections in the packets was initiated by a
google chrome extension on a WebSocket protocol. The engineer checked message payloads to
determine what information was being sent off-site but the payloads are obfuscated and unreadable.
What does this STIX indicate?Options
Q: 8
What do 2xx HTTP response codes indicate for REST APIs?
Options
Q: 9
An engineer returned to work and realized that payments that were received over the weekend were
sent to the wrong recipient. The engineer discovered that the SaaS tool that processes these
payments was down over the weekend. Which step should the engineer take first?
Options
Q: 10
The SIEM tool informs a SOC team of a suspicious file. The team initializes the analysis with an
automated sandbox tool, sets up a controlled laboratory to examine the malware specimen, and
proceeds with behavioral analysis. What is the next step in the malware analysis process?
Options
Question 1 of 10

