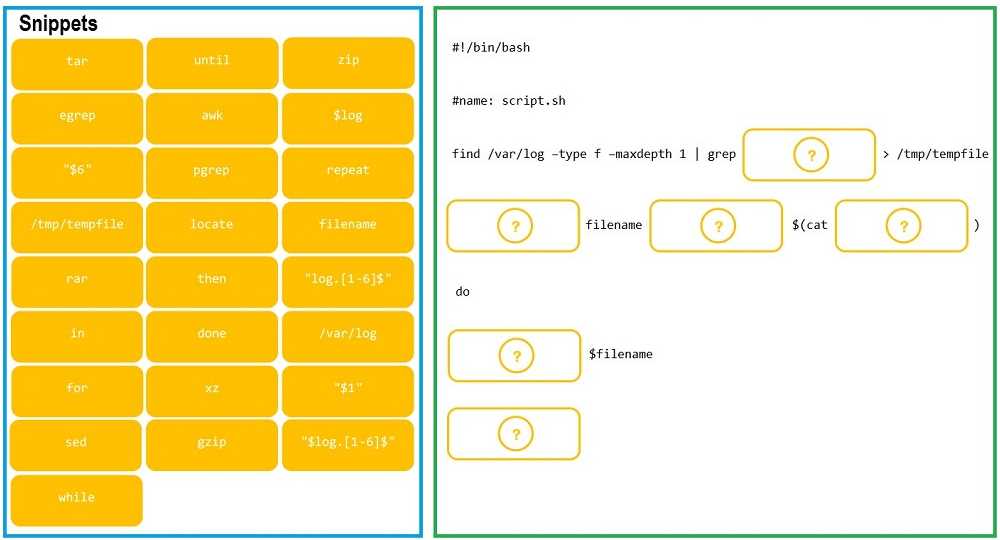
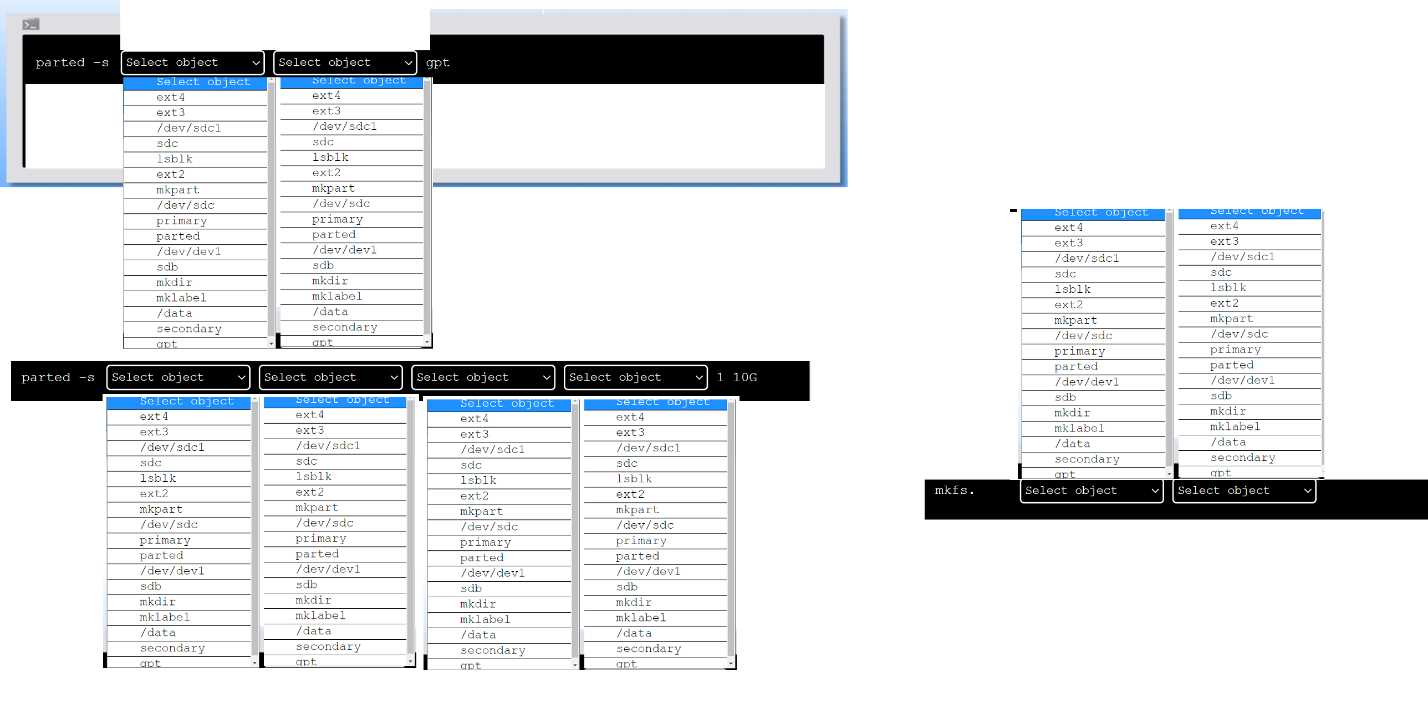
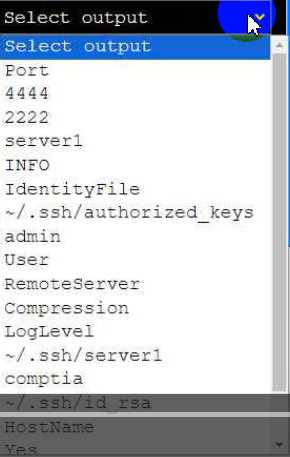
part for
detailed answer of
each part.
Explanation:
Part 1
Here is the step-by-step command construction process:
1. Move the private key (likely named server1 based on the provided details) to the .ssh directory:
mv ~/server1 ~/.ssh/id_rsa
This command moves the private key (assuming it's named server1) from the home directory (~) to
the .ssh directory and renames it to id_rsa (which is the default SSH private key file name).
2. Set the correct permissions for the private key file:
chmod 600 ~/.ssh/id_rsa
The private key file should be readable and writable only by the owner to maintain security.
3. Connect to the server using the private key and the correct port (2222):
ssh -i ~/.ssh/id_rsa -p 2222 admin@server1
This command tells ssh to use the specified private key (-i ~/.ssh/id_rsa), connect on port 2222 (-p
2222), and log in as the admin user on server1.
Part 2: Setting File Permissions
The correct command to set the file permissions based on the screenshots would likely involve using
chmod. Here is the command to set permissions correctly:
chmod 600 ~/.ssh/id_rsa
This restricts the private key's permissions so that only the user can read and write it.
Part 3: Setting Ownership
If ownership needs to be set, the command would look like this:
chown comptia:comptia ~/.ssh/id_rsa
This command ensures that the file is owned by the correct user (comptia) and the correct group
(comptia).
In part 4, it asks you to select the proper file for editing to enable remote server access. Based on
standard SSH configuration requirements, the proper file to edit for remote server access would be
~/.ssh/config.
Here’s why:
~/.ssh/config: This file allows you to set up configuration options for different hosts, including
specifying ports, user names, and the identity file (private key). You would add the necessary
configuration for server1 to this file for easier access.
Other options:
~/.ssh/authorized_keys: This file lists public keys that are authorized to log in to the local system. It's
not meant for configuring remote access to another server.
~/.ssh/known_hosts: This file stores the host keys of servers you’ve connected to. It doesn’t allow for
editing remote access settings.
~/.ssh/server1: This seems like a private key file or another custom file, but it’s not typically used to
configure SSH options.
For configuring access to server1 on port 2222, you would add a block like this to the ~/.ssh/config
file:
Host server1
HostName server1
Port 2222
User admin
IdentityFile ~/.ssh/id_rsa
 Which of the following commands should be used to resolve the issue?
Which of the following commands should be used to resolve the issue?
 Based on the output above, which of following is the MOST probable cause of the issue?
Based on the output above, which of following is the MOST probable cause of the issue?