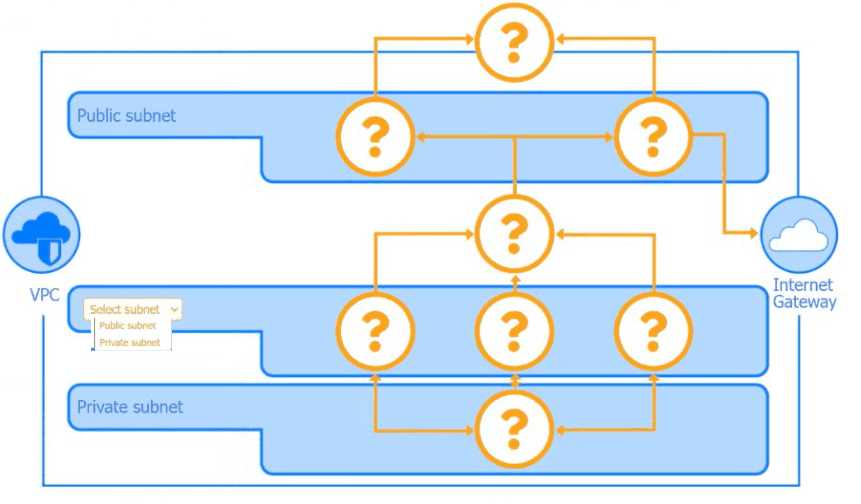
This looks like a spot where you'd use a reverse proxy. It can sit between the clients and the web servers to help manage traffic and provide some basic protection. Not sure if that's enough for layer-7 threats though. Anyone see issues with that approach?
Option D looked right to me since encryption can help protect data even on legacy systems. Had something like this in a mock, and they called out encryption as a control for old servers. But not totally sure if that's enough by itself.
If the requirement said "first step" instead of "most likely," would you still pick B or go for monitoring?
Option A seems right. Secure web gateway covers remote users by filtering their web traffic and applying company policies without needing a VPN, which the question specifically says not to use. Next-gen firewalls are more for network edges, and deep packet inspection isn't really tailored to remote scenarios in this way. Pretty sure SWG is what they're after here but happy to hear other takes if I'm off.



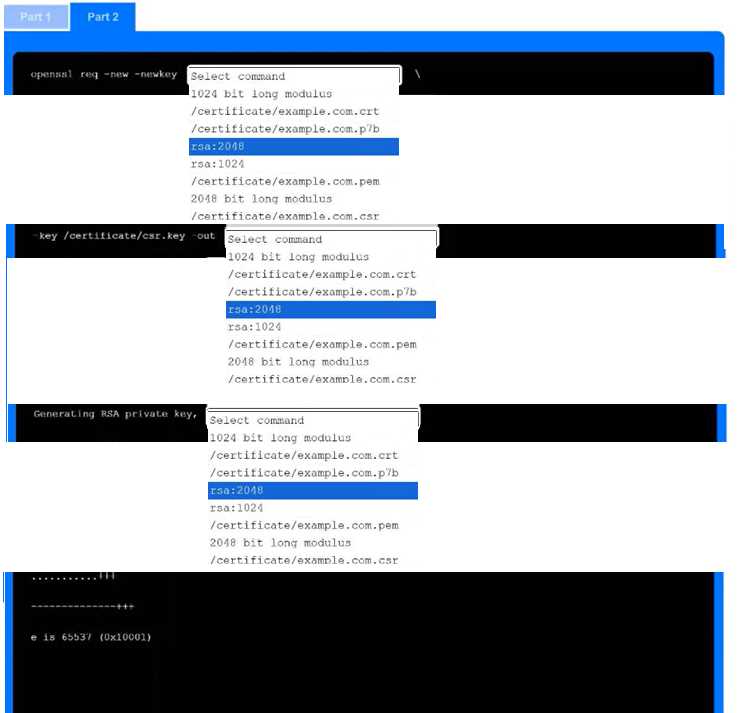
-keyout as one of the picks instead of just rsa:2048 every time. Not 100% sure though, maybe I'm mixing up with another format. Agree?I don't think it's D, since monitoring/review only happens after risks are identified and scoped. B fits because that's where you actually pin down what could go wrong and set those project boundaries. Sometimes the wording trips people up here.
I'm pretty sure it's B in this scenario. Risk identification is where you figure out what could go wrong and clarify which parts of the project you're actually assessing. D (monitoring and review) always comes after, so that's an easy one to rule out. If anyone disagrees, let me know!
Official study guides and practice tests cover scenarios like this a lot. They highlight user provisioning scripts (D) for automating account setup so permissions match policy every time. I think that's the main point here, but if anyone found something different in labs or the exam, let me know.
Anybody else think ticketing workflow (B) could also help here? I know D is more about automating the actual account setup and permissions, but sometimes workflows tie into approvals too. Is there a case where B would apply or is it always D for automation?

