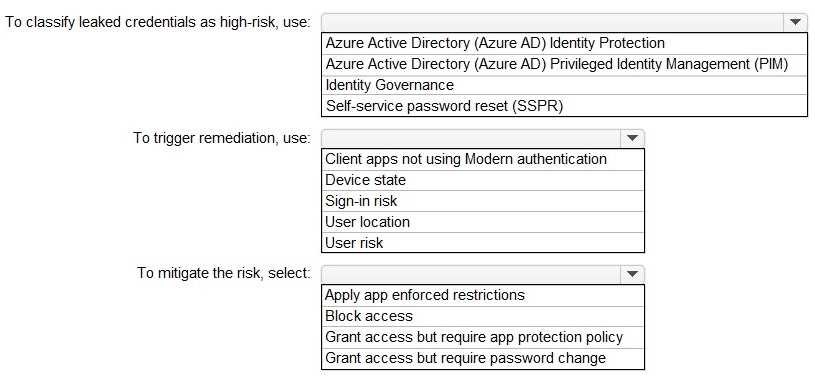
HOTSPOT You have a Microsoft 365 tenant. You need to identify users who have leaked credentials. The solution must meet the following requirements. • Identity sign-Ins by users who ate suspected of having leaked credentials. • Rag the sign-ins as a high risk event. • Immediately enforce a control to mitigate the risk, while still allowing the user to access applications. What should you use? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
Azure AD Identity Protection, User risk, Grant access but require password change.
Nah, "sign-in risk" is a common trap here-it's asking about leaked creds which means we care about overall user risk, not session-specific. So Azure AD Identity Protection, User risk policy, and require password change is the combo. I saw a similar question in practice and picked these. Correct me if I missed anything!