1. Microsoft Learn
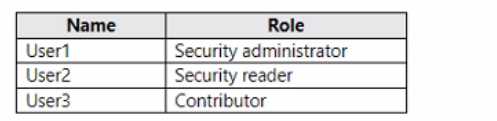
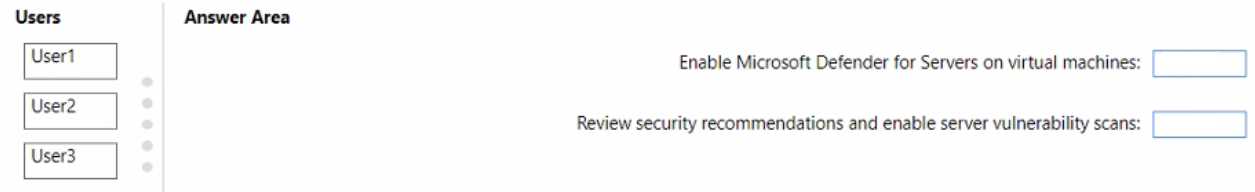
"Permissions in Microsoft Defender for Cloud": This document outlines the roles and permissions for managing Defender for Cloud.
Under the "Roles and allowed actions" table
it specifies that Security Admin can "Edit security policy
apply recommendations". This covers enabling vulnerability scans. It also states
"To enable Defender for Cloud plans on a subscription
you must be assigned the role of Subscription Owner
Subscription Contributor
or Security Admin." This confirms Security Admin is the least-privileged role for enabling Defender for Servers.
2. Microsoft Learn
"Azure built-in roles - Security Admin": This page details the specific permissions for the Security Admin role.
The role includes the Microsoft.Security/ permission
which grants full control over security configurations within the Microsoft.Security resource provider
including enabling plans and configuring vulnerability assessments
without granting excessive permissions to manage other Azure resources.
3. Microsoft Learn
"Azure built-in roles - Security Reader": This page details the permissions for the Security Reader role.
The permissions listed are all read-only (e.g.
Microsoft.Security/policies/read
Microsoft.Security/pricings/read)
confirming that this role can view settings but cannot enable any features.