Microsoft. (2024). What is Microsoft 365 Defender?. Microsoft Learn. Retrieved from learn.microsoft.com/en-us/microsoft-365/security/defender/microsoft-365-defender.
Details: This document states, "Microsoft 365 Defender is a unified pre- and post-breach enterprise defense suite that natively coordinates detection, prevention, investigation, and response across endpoints, identities, email, and applications..." This confirms its role in protecting Windows devices.
Microsoft. (2024). What is Microsoft Defender for Cloud?. Microsoft Learn. Retrieved from learn.microsoft.com/en-us/azure/defender-for-cloud/defender-for-cloud-introduction.
Details: In the introductory section, it specifies that Defender for Cloud is a "Cloud Security Posture Management (CSPM) and Cloud Workload Protection (CWP) for all of your Azure, on-premises, and multicloud (Amazon AWS and Google GCP) resources." This establishes its role for Azure resources.
Microsoft. (2024). Overview of Microsoft Defender for Storage. Microsoft Learn. Retrieved from learn.microsoft.com/en-us/azure/defender-for-cloud/defender-for-storage-introduction.
Details: This page explicitly states, "Microsoft Defender for Storage is an Azure-native layer of security intelligence that detects unusual and potentially harmful attempts to access or exploit your storage accounts."
Microsoft. (2024). Overview of Microsoft Defender for Servers. Microsoft Learn. Retrieved from learn.microsoft.com/en-us/azure/defender-for-cloud/defender-for-servers-introduction.
Details: This document details how Defender for Cloud provides protection for virtual machines and servers, including "foundational cloud security posture management (CSPM)" and "vulnerability assessment solutions."



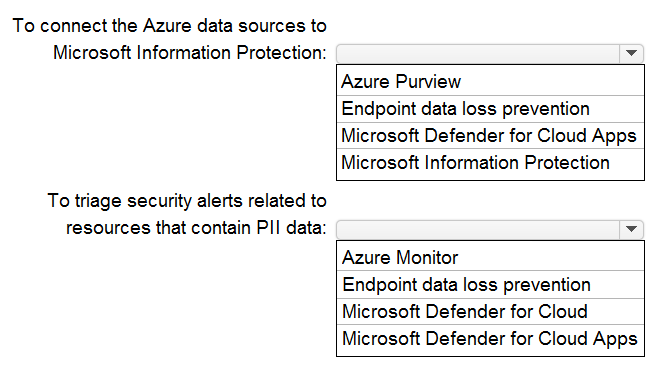
 What should you use to meet the requirement of each app? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
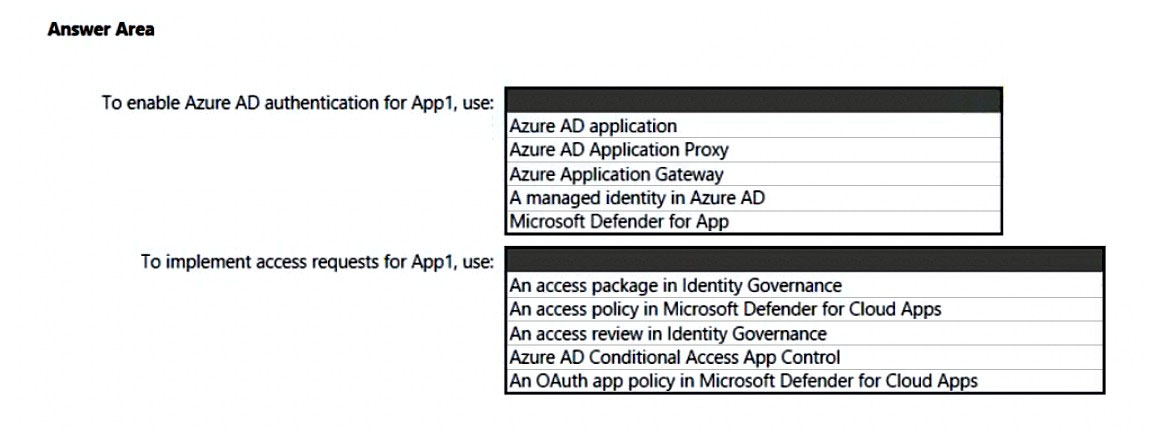
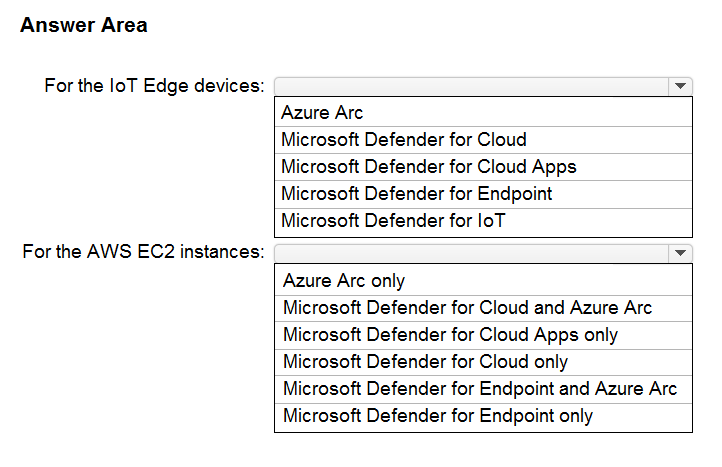
What should you use to meet the requirement of each app? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.