Option A and E make sense here. You have to enable Defender plans for containers (E) so AKS is even monitored, and auto provisioning (A) ensures the agent gets installed on all clusters, which is needed for secure score. B/C/D don't actually trigger the right recommendations for secure score updates. Pretty confident but open to corrections.
I don't think it's C, I'd pick D here. NSG inbound rules (C) can't control access to Azure Storage coming from public internet IPs, that's a common trick option. Storage account firewall rules (D) are made for this, letting you set an allow list of only those app servers' IPs. Pretty sure that's what Microsoft wants here but open to other takes.
Yeah, D makes the most sense to me. Storage account firewall rules let you specify those 20 app server IPs so only they get access, blocking everything else by default. NSGs like C don't work for public internet traffic to storage accounts. Pretty sure D is what Microsoft has in mind, unless there's some networking detail we're missing.
This looks like the classic scenario for D. You'd use storage account firewall rules so only the public IPs of those 20 servers are allowed access, everything else blocked by default. Official study guide and lab practices both highlight this method. I think D is best here but open to other suggestions if anyone has seen it handled another way in real exam cases.
Yeah, looks like A and B fit best. Blob storage with customer-provided keys lets you keep insurance file encryption keys on-prem, which matches that requirement. For cardholder data, Managed HSM is still company-controlled in Azure so B works. Pretty sure about this combo but let me know if something's off?
You receive a security alert in Microsoft Defender for Cloud as shown in the exhibit. (Click the Exhibit tab.) 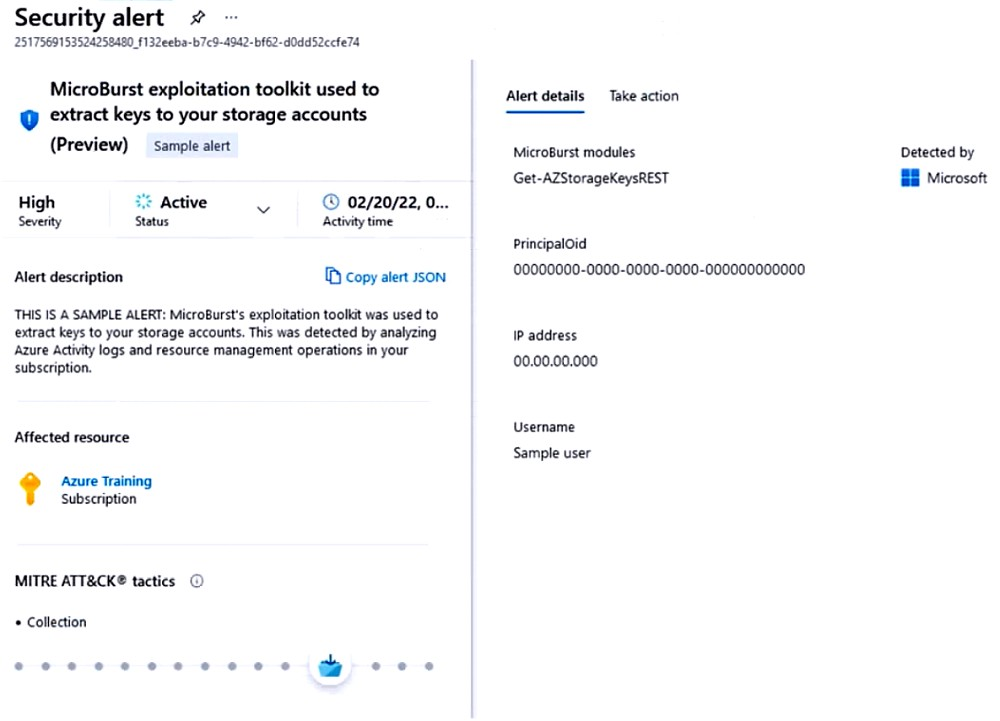
This one comes up in practice sets too. A lines up with "public access should be disallowed" which is exactly what the Defender alert called out. Official docs and practice exams both highlight this policy for public container issues. If anyone's got a different take let me know, but pretty sure it's A.
Don't think it's C here. The question is specifically about public access to storage accounts, not shared key usage. A covers that exact misconfig according to recent exam-style practice. People tend to mix up public and shared key exposures so that's the trap I see a lot.
Official guides and practice tests both mention SAST (B) for catching common flaws. It's good for code-level issues like injection. Not sure if it covers configs fully, but worth reviewing in the study materials. Agree?
D is the move here since Azure Policy actually enforces compliance with MCSB across deployed resources, not just in the pipeline. Branch policies (C) only cover code merge, not post-deploy resource config. Pretty sure this is what Microsoft expects for ongoing enforcement but open to other thoughts if I missed something.
Yeah, for stopping bots from scanning web apps, B fits best. Azure Application Gateway WAF has built-in bot protection rules and lets you create custom rules for geo restrictions too. That actually addresses both blocking bots and limiting access by region, so pretty sure B is the most complete answer here. Anyone disagree?
I kinda see why D could work since Traffic Manager can route based on geography and ASGs help segment, so maybe that’s seen as reducing surface area? Doesn’t really block bots specifically but fits if they just want geo-filtering. Not 100% though, someone correct me?
Pretty sure it's A for this one. Defender for Cloud integrates with AWS and GCP, does automatic compliance assessments, and gives you improvement actions with guidance. D (the connectors) just let you pull stuff in, they don't actually automate the monitoring part. If anyone thinks D works better here, let me know-but I think A fits all the requirements best.
Makes sense to pick A for this since Defender for Cloud actually does continuous posture assessment across those clouds and spits out remediation steps. D just connects data, not as automated. Pretty sure it's A but open to other arguments.

