Q: 1
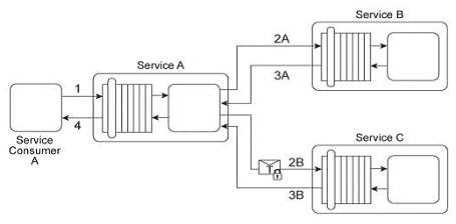
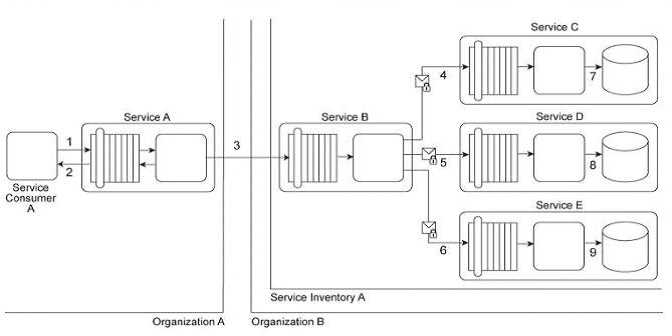
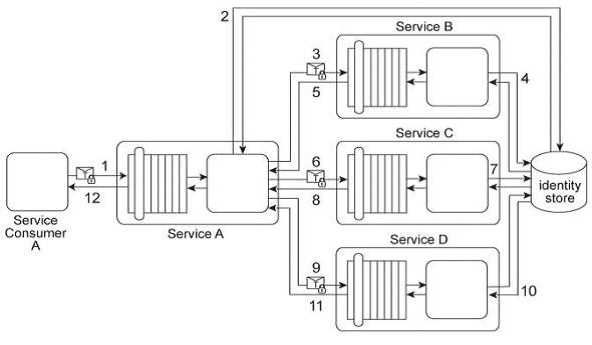
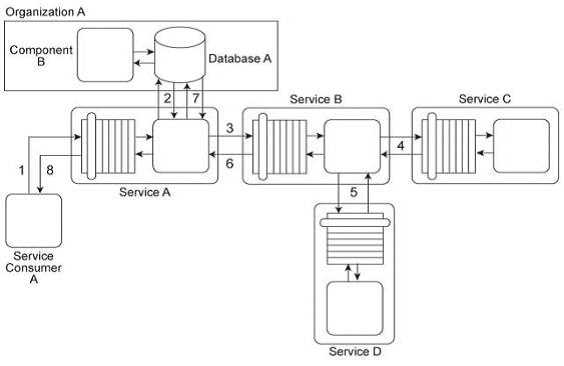
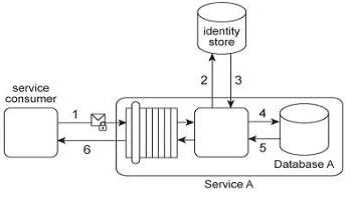
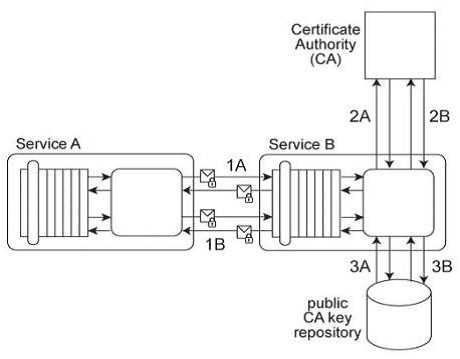
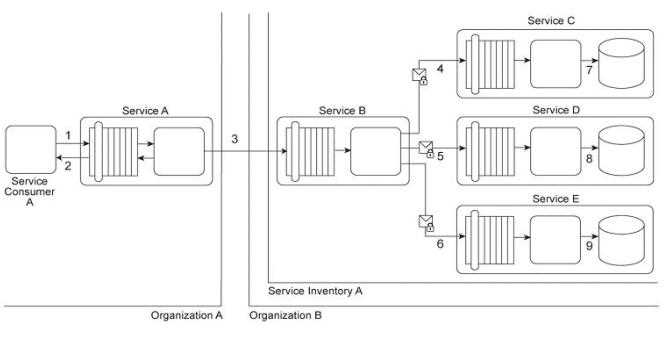
Service Consumer A sends a request to Service A (1). Service A replies with an acknowledgement
message (2) and then processes the request and sends a request message to Service B (3). This
message contains confidential financial data. Service B sends three different request messages
together with its security credentials to Services C .D .and E (4, 5, 6). Upon successful authentication,
Services C .D .and E store the data from the message in separate databases (7.8, 9). Services B .C .D,
and E belong to Service Inventory A, which further belongs to Organization B .Service Consumer A
and Service A belong to Organization A .Organization B decides to create a new service inventory
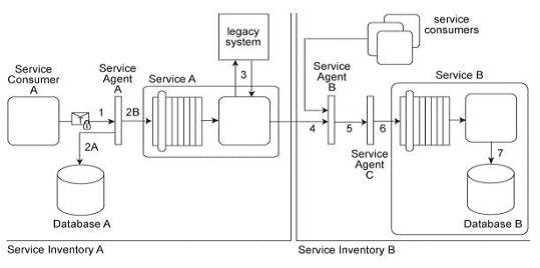
(Service Inventory B) for services that handle confidential data. Access to these services is restricted
by allocating Service Inventory B its own private network. Access to this private network is further
restricted by a dedicated firewall. Services C, D and E are moved into Service Inventory B, and as a
result. Service B can no longer directly access these services. How can this architecture be changed to
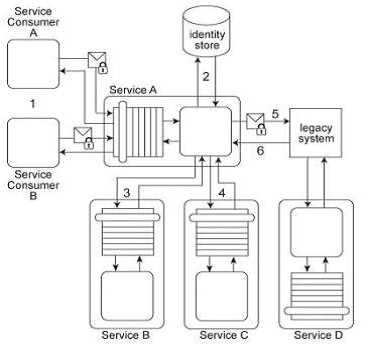
allow Service B to access Services C, D and E in a manner that does not jeopardize the security of
Service Inventory B while also having a minimal impact on the service composition's performance?

Options
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.