Q: 7
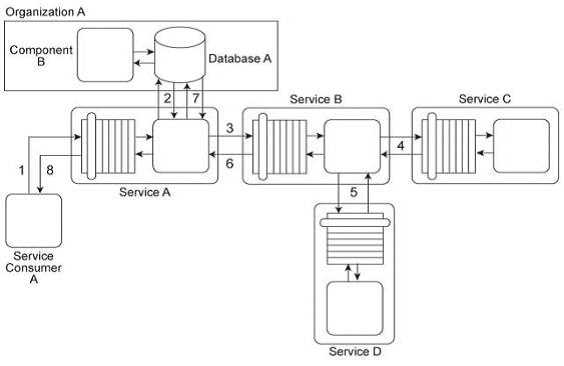
Service Consumer A sends a request message to Service A (1) after which Service A retrieves financial
data from Database A (2). Service A then sends a request message with the retrieved data to Service
B (3). Service B exchanges messages with Service C (4) and Service D (5), which perform a series of
calculations on the data and return the results to Service A .Service A uses these results to update
Database A (7) and finally sends a response message to Service Consumer A (8). Component B has
direct, independent access to Database A and is fully trusted by Database A .Both Component B and
Database A reside within Organization A .Service Consumer A and Services A, B, C, and D are external
to the organizational boundary of Organization A .Service A has recently experienced an increase in
the number of requests from Service Consumer A .However, the owner of Service Consumer A has
denied that Service Consumer A actually sent these requests. Upon further investigation it was
determined that several of these disclaimed requests resulted in a strange behavior in Database A,
including the retrieval of confidential data. The database product used for Database A has no feature
that enables authentication of consumers. Furthermore, the external service composition (Services
A, B, C, D) must continue to operate at a high level of runtime performance. How can this
architecture be improved to avoid unauthenticated access to Database A while minimizing the
performance impact on the external service composition?

Options
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.

