Q: 5
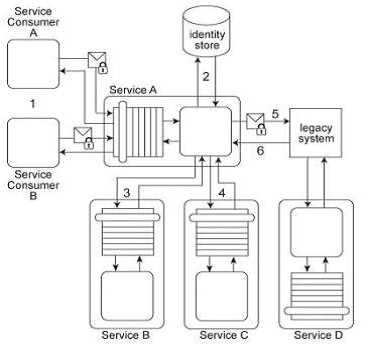
Service A has two specific service consumers, Service Consumer A and Service Consumer B (1). Both
service consumers are required to provide security credentials in order for Service A to perform
authentication using an identity store (2). If a service consumer's request message is successfully
authenticated, Service A processes the request by exchanging messages with Service B (3) and then
Service C (4). With each of these message exchanges, Service A collects data necessary to perform a
query against historical data stored in a proprietary legacy system. Service A's request to the legacy
system must be authenticated (5). The legacy system only provides access control using a single
account. If the request from Service A is permitted, it will be able to access all of the data stored in
the legacy system. If the request is not permitted, none of the data stored in the legacy system can
be accessed. Upon successfully retrieving the requested data (6), Service A generates a response
message that is sent back to either Service Consumer A or B .The legacy system is also used
independently by Service D without requiring any authentication. Furthermore, the legacy system
has no auditing feature and therefore cannot record when data access from Service A or Service D
occurs. If the legacy system encounters an error when processing a request, it generates descriptive
error codes. This service composition architecture needs to be upgraded in order to fulfill the
following new security requirements:
1. Service Consumers A and B have different permission levels, and therefore, response messages
sent to a service consumer must only contain data for which the service consumer is authorized.
2. All data access requests made to the legacy system must be logged.
3. Services B and C must be provided with the identity of Service A's service consumer in order to
provide Service A with the requested data.
4. Response messages generated by Service A cannot contain confidential error information about
the legacy system. Which of the following statements provides solutions that satisfy these
requirements?

Options
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.

