Q: 4
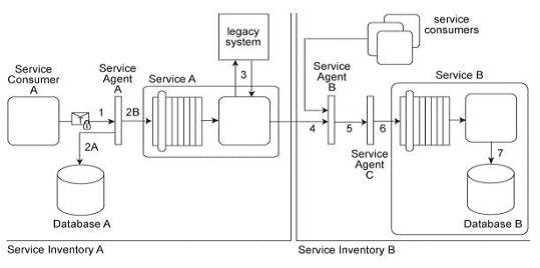
Service Consumer A sends a request message with an authentication token to Service A, but before
the message reaches Service A, it is intercepted by Service Agent A (1). Service Agent A validates the
security credentials and also validates whether the message is compliant with Security Policy A .If
either validation fails, Service Agent A rejects the request message and writes an error log to
Database A (2A). If both validations succeed, the request message is sent to Service A (2B). Service A
retrieves additional data from a legacy system (3) and then submits a request message to Service B
Before arriving at Service B, the request message is intercepted by Service Agent B (4) which
validates its compliance with Security Policy SIB then Service Agent C (5) which validates its
compliance with Security Policy B .If either of these validations fails, an error message is sent back to
Service A .that then forwards it to Service Agent A so that it the error can be logged in Database A
(2A). If both validations succeed, the request message is sent to Service B (6). Service B subsequently
stores the data from the message in Database B (7). Service A and Service Agent A reside in Service
Inventory A .Service B and Service Agents B and C reside in Service Inventory B .Security Policy SIB is
used by all services that reside in Service Inventory B .Service B can also be invoked by other service
consumers from Service Inventory B .Request messages sent by these service consumers must also
be compliant with Security Policies SIB and B .Access to the legacy system in Service Inventory A is
currently only possible via Service A, which means messages must be validated for compliance with
Security Policy A .A new requirement has emerged to allow services from Service Inventory B to
access the legacy system via a new perimeter service that will be dedicated to processing request
messages from services residing in Service Inventory B .Because the legacy system has no security
features, all security processing will need to be carried out by the perimeter service. However, there
are parts of Security Policy A that are specific to Service A and do not apply to the legacy system or
the perimeter service. Furthermore, response messages sent by the perimeter service to services
from Service Inventory B will still need to be validated for compliance to Security Policy B and
Security Policy SIB .How can the Policy Centralization pattern be correctly applied without
compromising the policy compliance requirements of services in both service inventories?

Options
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.

