Q: 3
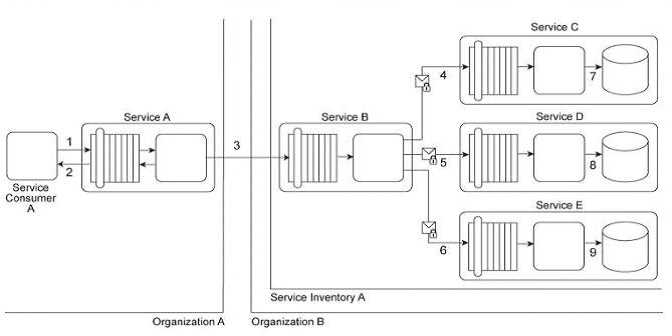
Service Consumer A sends a request to Service A (1). Service A replies with an acknowledgement
message (2) and then processes the request and sends a request message to Service B (3). This
message contains confidential financial data. Service B sends three different request messages
together with its security credentials to Services C, D, and E (4, 5, 6). Upon successful authentication,
Services C, D, and E store the data from the message in separate databases (7, 8, 9) Services B, C, D,
and E belong to Service Inventory A, which further belongs to Organization B .Service Consumer A
and Service A belong to Organization A .The service contracts of Services A and B both comply with
the same XML schema. However, each organization employs different security technologies for their
service architectures. To protect the confidential financial data sent by Service A to Service B, each
organization decides to independently apply the Data Confidentiality and the Data Origin
Authentication patterns to establish message-layer security for external message exchanges.
However, when an encrypted and digitally signed test message is sent by Service A to Service B,
Service B was unable to decrypt the message. Which of the following statements describes a solution
that solves this problem?

Options
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.

