Q: 2
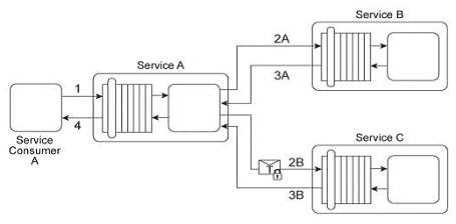
Service A is a publically accessible service that provides free multimedia retrieval capabilities to a
range of service consumers. To carry out this functionality, Service A is first invoked by Service
Consumer A (1). Based on the nature of the request message received from Service Consumer A,
Service A either invokes Service B or Service C .When Service B is invoked by Service A (2A) it
retrieves data from publicly available sources (not shown) and responds with the requested data
(3A). When Service C is invoked by Service A (2B) it retrieves data from proprietary sources within
the IT enterprise (not shown) and responds with the requested data (3B). After receiving a response
from Service B or Service C, Service A sends the retrieved data to Service Consumer A (4). Service B
does not require service consumers to be authenticated, but Service C does require authentication of
service consumers. The service contract for Service A therefore uses WS-Policy alternative policies in
order to express the two different authentication requirements to Service Consumer A .When Service
Consumer A sends a request message (1), Service A determines whether the request requires the
involvement of Service C and then checks to ensure that the necessary security credentials were
received as part of the message. If the credentials provided by Service Consumer A are verified.
Service A creates a signed SAML assertion and sends it with the request message to Service C (2B)
This authentication information is protected by public key encryption However, responses to Service
Consumer A's request message (3B, 4) are not encrypted for performance reasons. The owner of
Service C is planning two changes to the service architecture:
1. A fee will be charged to Service Consumer A (or any service consumer) using Service C .2. The
response messages issued by Service C need to be secured in order to prevent unauthorized access.
An analysis of Service C's usage statistics reveals that a group of service consumers specifically
request the retrieval of multimedia data on a frequent basis. To promote the usage of Service C to
these types of service consumers, the owner of Service C plans to offer a special discount by allowing
unlimited multimedia retrievals for a fixed monthly price. Service consumers that do not subscribe to
this promotion will need to pay for each request individually. It is anticipated that the new promotion
will significantly increase the usage of Service C .The owner of Service C therefore wants to ensure
that the security added to the response messages has a minimal impact on Service C's runtime
performance. What steps can be taken to fulfill these requirements?

Options
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.

