Q: 7
Refer to Exhibit.
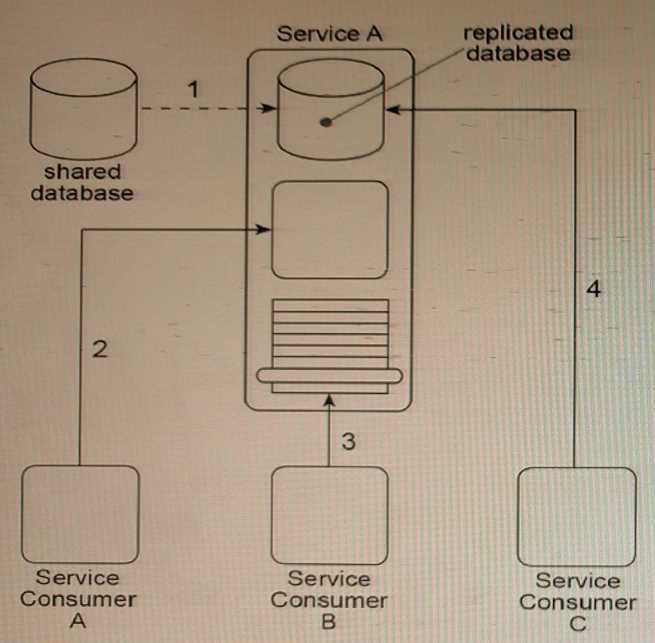
 Service A is a utility service that provides generic data access logic to a database containing data that
is periodically replicated from a shared database (1). Because the Standardized Service Contract
principle was applied to the design of Service A, its service contract has been fully standardized.
The service architecture of Service A Is being accessed by three service consumers. Service Consumer
A accesses a component that is part of the Service A Implementation by Invoking it directly (2).
Service Consumer B invokes Service A by accessing Its service contract (3). Service Consumer C
directly accesses the replicated database that Is part of the Service A Implementation (4).
You've been told that the reason Service Consumers A and C bypass the published Service A service
contract is because, for security reasons, they are not allowed to access a subset of the capabilities in
the API that comprises the Service A service contract. How can the Service A architecture be changed
to enforce these security restrictions while avoiding negative forms of coupling?
Service A is a utility service that provides generic data access logic to a database containing data that
is periodically replicated from a shared database (1). Because the Standardized Service Contract
principle was applied to the design of Service A, its service contract has been fully standardized.
The service architecture of Service A Is being accessed by three service consumers. Service Consumer
A accesses a component that is part of the Service A Implementation by Invoking it directly (2).
Service Consumer B invokes Service A by accessing Its service contract (3). Service Consumer C
directly accesses the replicated database that Is part of the Service A Implementation (4).
You've been told that the reason Service Consumers A and C bypass the published Service A service
contract is because, for security reasons, they are not allowed to access a subset of the capabilities in
the API that comprises the Service A service contract. How can the Service A architecture be changed
to enforce these security restrictions while avoiding negative forms of coupling?
 Service A is a utility service that provides generic data access logic to a database containing data that
is periodically replicated from a shared database (1). Because the Standardized Service Contract
principle was applied to the design of Service A, its service contract has been fully standardized.
The service architecture of Service A Is being accessed by three service consumers. Service Consumer
A accesses a component that is part of the Service A Implementation by Invoking it directly (2).
Service Consumer B invokes Service A by accessing Its service contract (3). Service Consumer C
directly accesses the replicated database that Is part of the Service A Implementation (4).
You've been told that the reason Service Consumers A and C bypass the published Service A service
contract is because, for security reasons, they are not allowed to access a subset of the capabilities in
the API that comprises the Service A service contract. How can the Service A architecture be changed
to enforce these security restrictions while avoiding negative forms of coupling?
Service A is a utility service that provides generic data access logic to a database containing data that
is periodically replicated from a shared database (1). Because the Standardized Service Contract
principle was applied to the design of Service A, its service contract has been fully standardized.
The service architecture of Service A Is being accessed by three service consumers. Service Consumer
A accesses a component that is part of the Service A Implementation by Invoking it directly (2).
Service Consumer B invokes Service A by accessing Its service contract (3). Service Consumer C
directly accesses the replicated database that Is part of the Service A Implementation (4).
You've been told that the reason Service Consumers A and C bypass the published Service A service
contract is because, for security reasons, they are not allowed to access a subset of the capabilities in
the API that comprises the Service A service contract. How can the Service A architecture be changed
to enforce these security restrictions while avoiding negative forms of coupling?Options
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.

