Q: 13
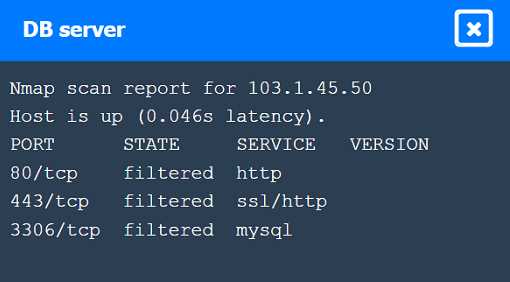
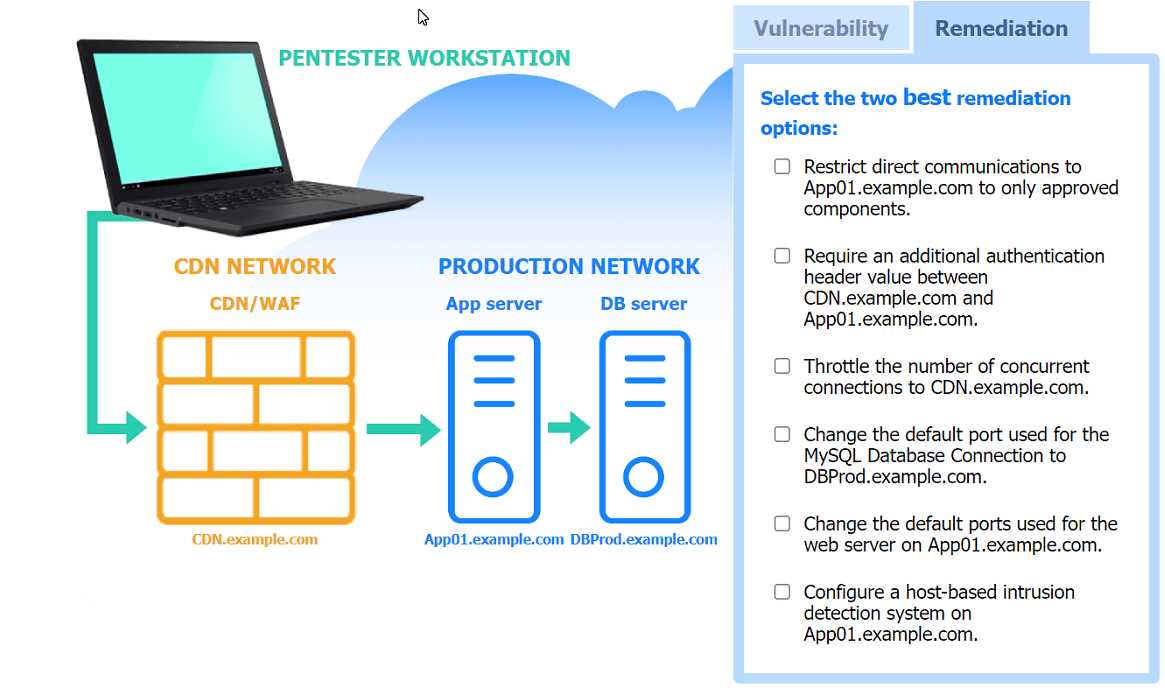
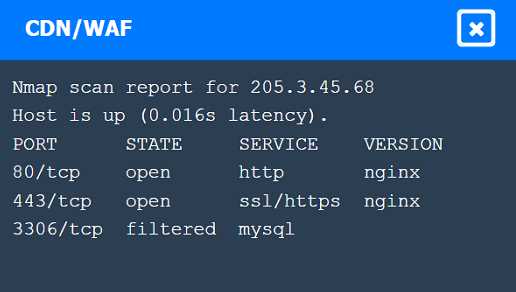
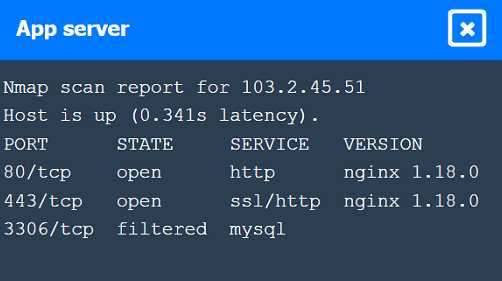
[Information Gathering and Vulnerability Scanning] A penetration tester performs several Nmap scans against the web application for a client. INSTRUCTIONS Click on the WAF and servers to review the results of the Nmap scans. Then click on each tab to select the appropriate vulnerability and remediation options. If at any time you would like to bring back the initial state of the simulation, please click the Reset All button. 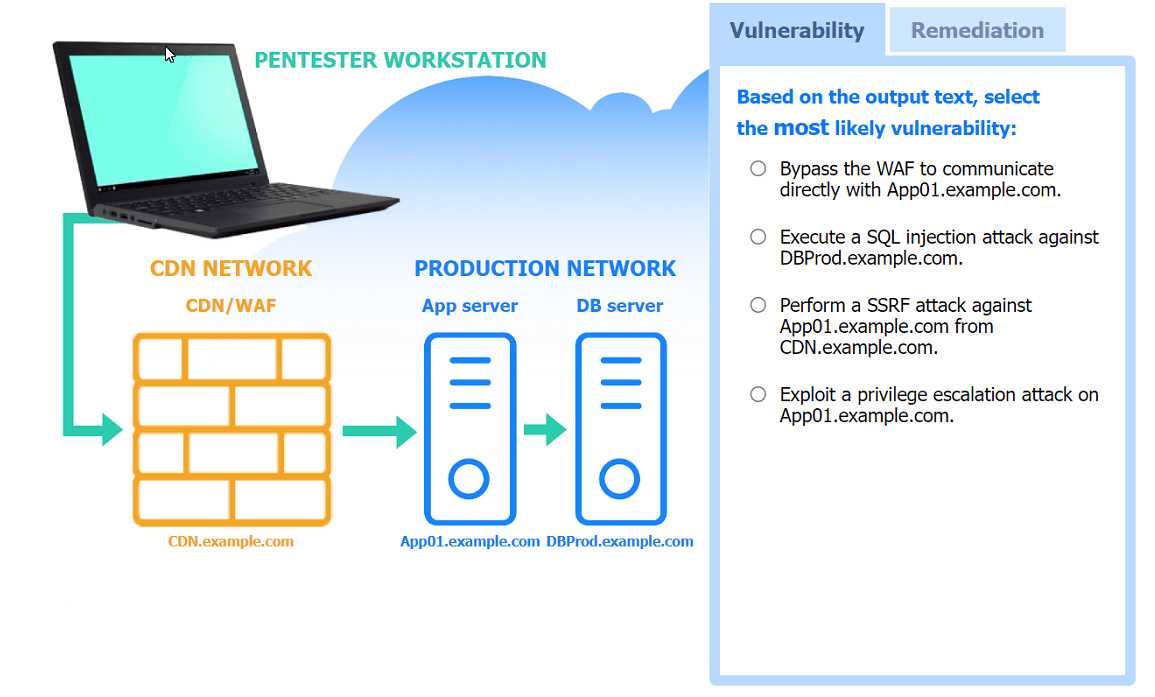
Your Answer
Discussion
Did you check the official CompTIA Pentest+ objectives and run through scenario-based labs for this type of WAF bypass question?
Bypass the WAF to communicate directly with app server, then restrict direct access and require custom authentication header.
Does the question specify if "best" remediation is required, or just any viable option? If they're asking for the most secure setup, I'd say only allowing the approved components plus that custom auth header is key. If it's just about any fix, network restriction alone could suffice.
Bypass the WAF to communicate directly with app server, then restrict direct communication but only using a firewall. Not totally sure if that's detailed enough for remediation but that's what I picked.
Be respectful. No spam.