Q: 12
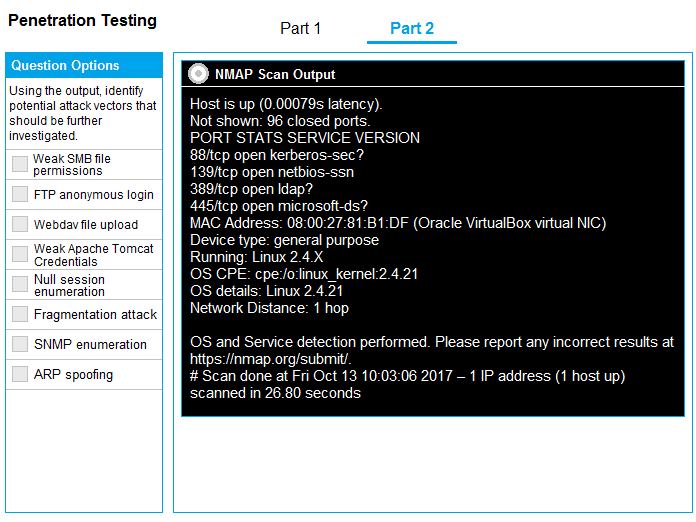
[Attacks and Exploits] You are a penetration tester running port scans on a server. INSTRUCTIONS Part 1: Given the output, construct the command that was used to generate this output from the available options. Part 2: Once the command is appropriately constructed, use the given output to identify the potential attack vectors that should be investigated further. If at any time you would like to bring back the initial state of the simulation, please click the Reset All button. 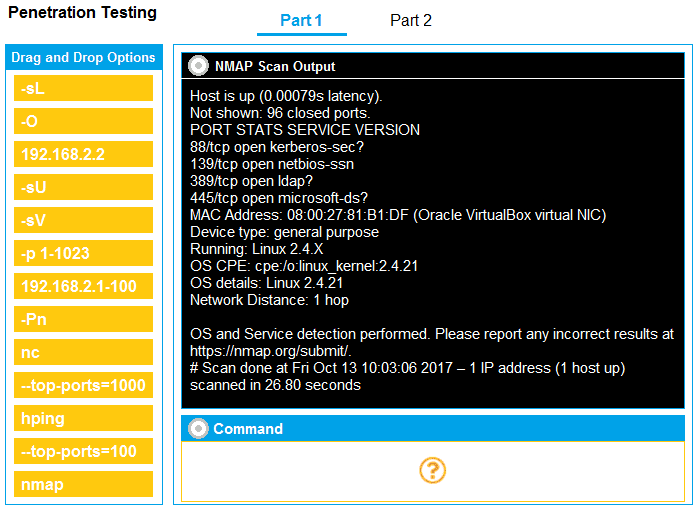
Your Answer
Discussion
Shouldn't the command have
-top-ports=100 instead of -top-ports=100? Also, with ports 139 and 445 open, I'd definitely look into SMB null sessions and weak file share permissions.Nah, pretty sure it should be NMAP -sV -O -top-ports=100 192.168.2.2 for part 1, not the double dash version.
NMAP -sV -O -top-ports=100 192.168.2.2
Pretty sure that's what you'd use, saw similar on practice tests. For the attack vectors part, I'd say anonymous SMB enumeration and maybe weak share permissions are the main things to check, but if you're unsure double-check the official CompTIA guide.
Pretty sure that's what you'd use, saw similar on practice tests. For the attack vectors part, I'd say anonymous SMB enumeration and maybe weak share permissions are the main things to check, but if you're unsure double-check the official CompTIA guide.
Be respectful. No spam.