Q: 11
Which feature enables an administrator to review the Security policy rule base for unused rules?
Options
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.
Q: 12
An administrator wants to create a No-NAT rule to exempt a flow from the default NAT rule. What is
the best way to do this?
Options
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.
Q: 13
What is the maximum volume of concurrent administrative account sessions?
Options
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.
Q: 14
What are the requirements for using Palo Alto Networks EDL Hosting Sen/ice?
Options
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.
Q: 15
An administrator is troubleshooting traffic that should match the interzone-default rule. However,
the administrator doesn't see this traffic in the traffic logs on the firewall. The interzone-default was
never changed from its default configuration.
Why doesn't the administrator see the traffic?
Options
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.
Q: 16
The PowerBall Lottery has reached a high payout amount and a company has decided to help
employee morale by allowing employees to check the number, but doesn’t want to unblock the
gambling URL category.
Which two methods will allow the employees to get to the PowerBall Lottery site without the
company unlocking the gambling URL category? (Choose two.)
Options
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.
Q: 17
For the firewall to use Active Directory to authenticate users, which Server Profile is required in the
Authentication Profile?
Options
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.
Q: 18
An administrator would like to apply a more restrictive Security profile to traffic for file sharing
applications. The administrator does not want to update the Security policy or object when new
applications are released.
Which object should the administrator use as a match condition in the Security policy?
Options
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.
Q: 19
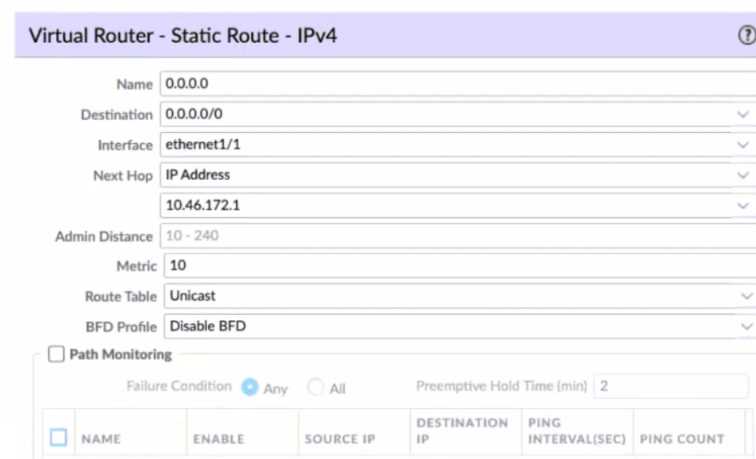
Given the screenshot what two types of route is the administrator configuring? (Choose two )

Options
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.
Q: 20
You receive notification about a new malware that infects hosts An infection results in the infected
host attempting to contact a command-and-control server Which Security Profile when applied to
outbound Security policy rules detects and prevents this threat from establishing a command-and-
control connection?
Options
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.
Question 11 of 20 · Page 2 / 2

