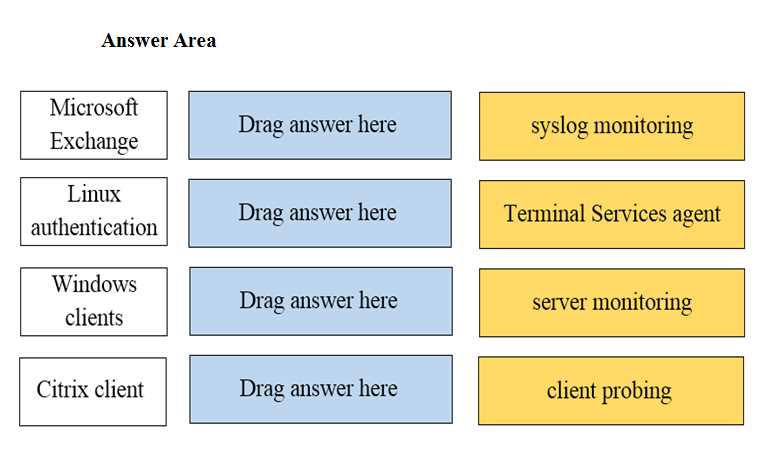
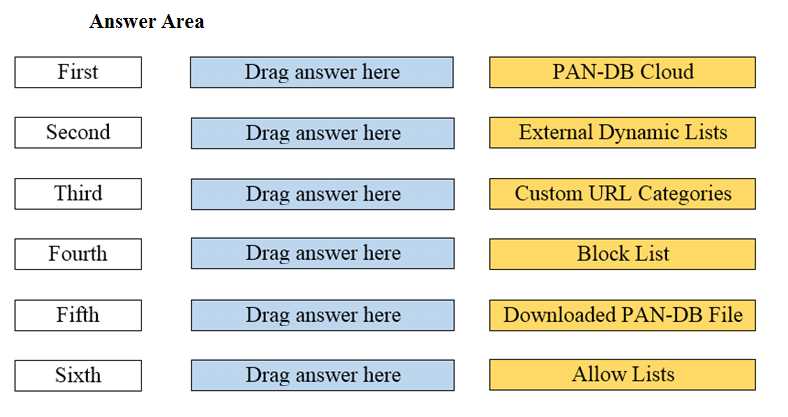
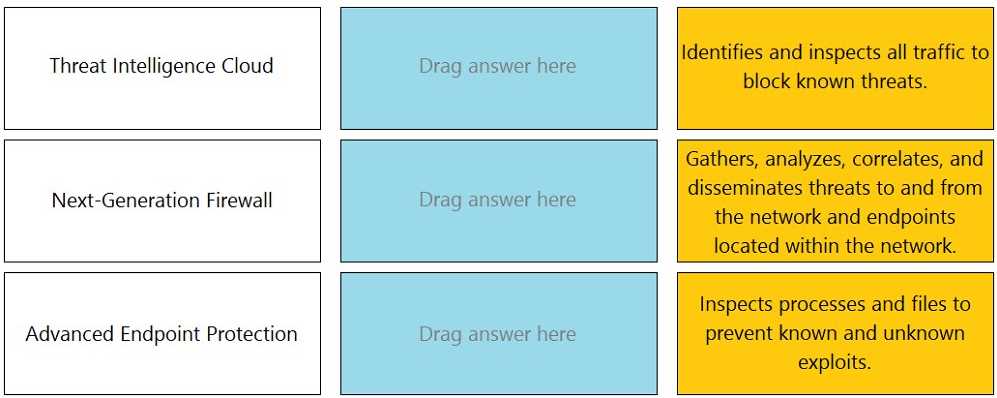
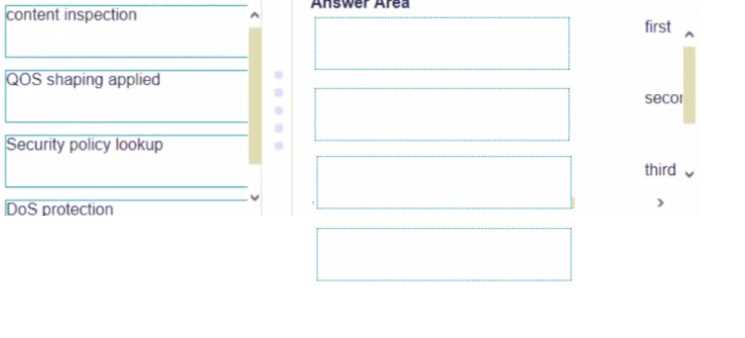
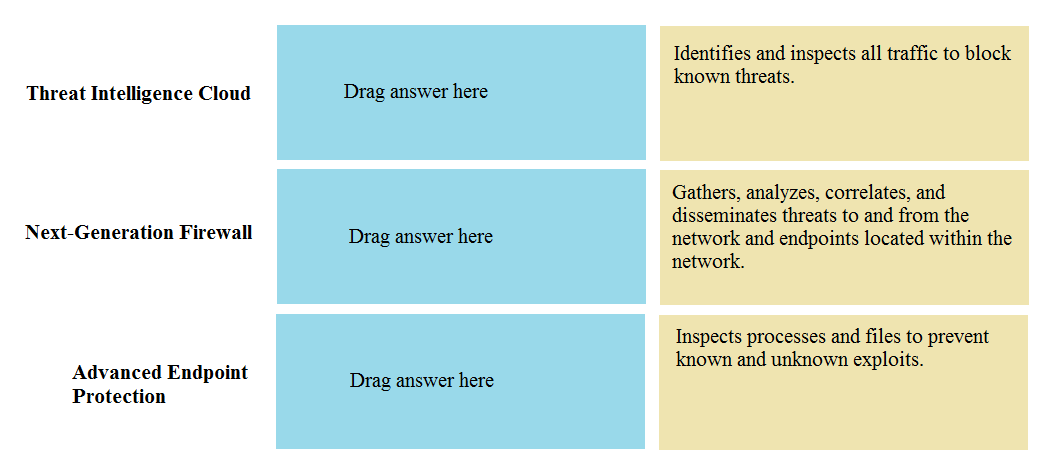
DRAG DROP Match the network device with the correct User-ID technology.
Q: 1
Drag & Drop
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.
Q: 2
DRAG DROP Arrange the correct order that the URL classifications are processed within the system.
Drag & Drop
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.
Q: 3
DRAG DROP Match each feature to the DoS Protection Policy or the DoS Protection Profile.
Drag & Drop
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.
Q: 4
DRAG DROP Place the following steps in the packet processing order of operations from first to last.
Drag & Drop
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.
Q: 5
DRAG DROP Place the steps in the correct packet-processing order of operations.
Drag & Drop
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.
Q: 6
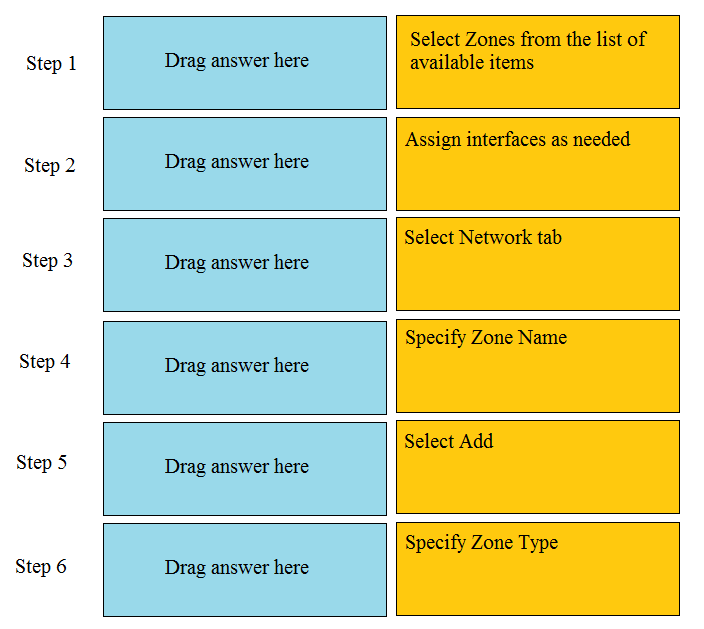
DRAG DROP Order the steps needed to create a new security zone with a Palo Alto Networks firewall.
Drag & Drop
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.
Q: 7
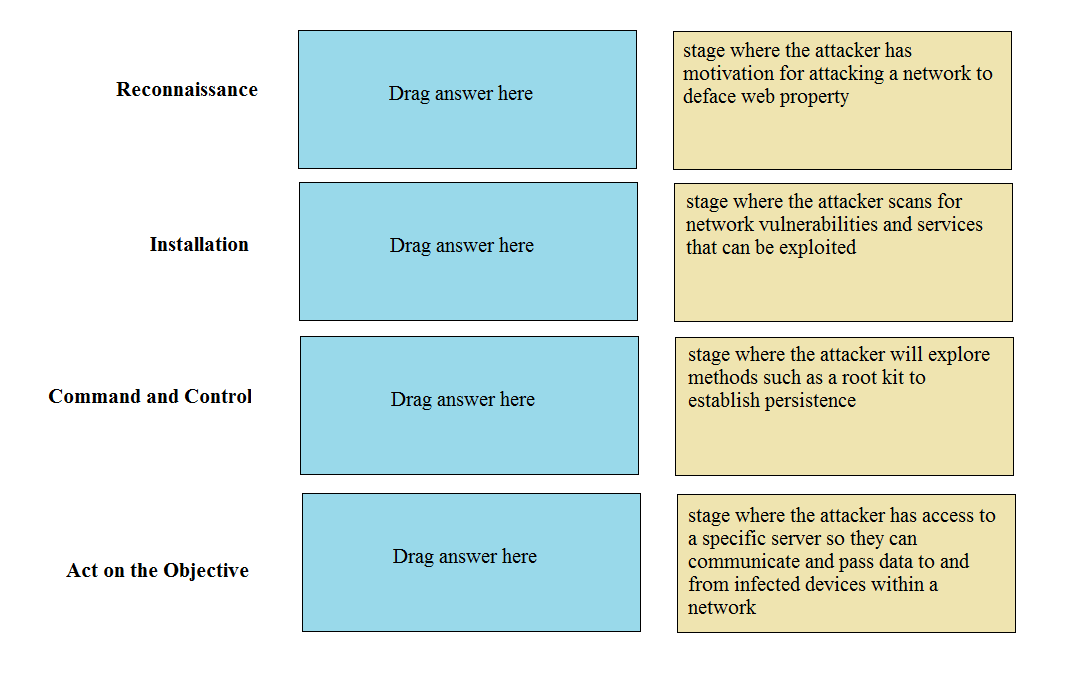
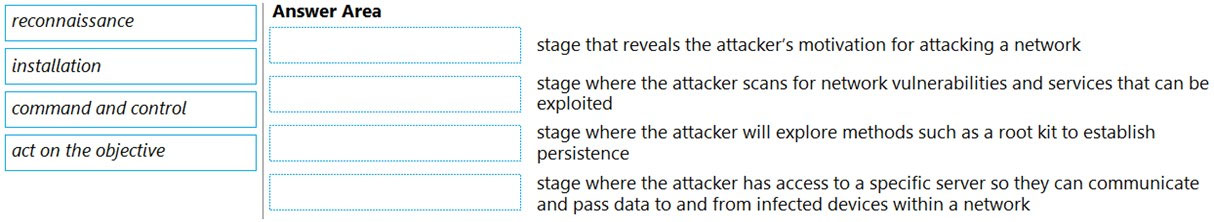
DRAG DROP Match the cyber-attack lifecycle stage to its correct description.
Drag & Drop
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.
Q: 8
DRAG DROP Match each rule type with its example
Drag & Drop
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.
Q: 9
DRAG DROP Match the Cyber-Attack Lifecycle stage to its correct description.
Drag & Drop
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.
Question 1 of 20 · Page 1 / 2