Q: 1
Which characteristic of serverless computing enables developers to quickly deploy application code?
Options
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.
Q: 2
DRAG DROP
Match each description to a Security Operating Platform key capability.

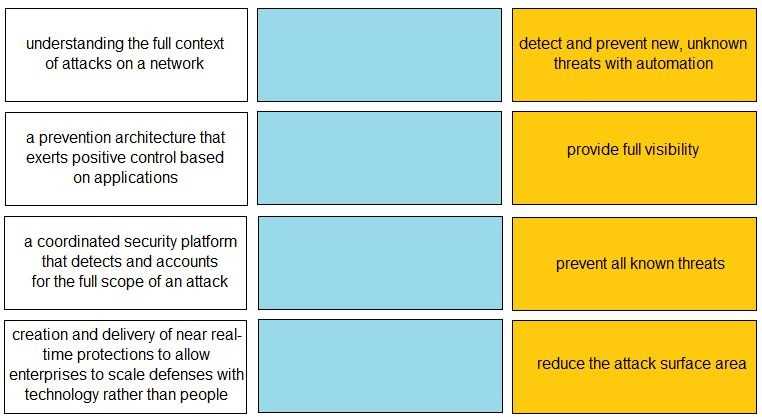
Your Answer
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.
Q: 3
Which core component is used to implement a Zero Trust architecture?
Options
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.
Q: 4
In the attached network diagram, which device is the switch?

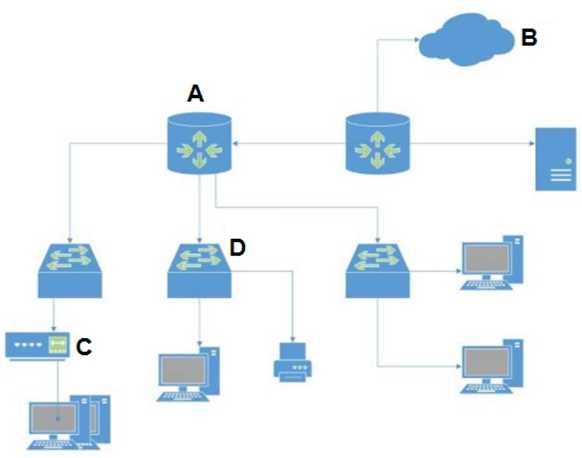
Options
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.
Q: 5
You received an email, allegedly from a bank, that asks you to click a malicious link to take action on
your account.
Which type of attack is this?
Options
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.
Q: 6
From which resource does Palo Alto Networks AutoFocus correlate and gain URL filtering
intelligence?
Options
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.
Q: 7
Which of the following is an AWS serverless service?
Options
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.
Q: 8
During the OSI layer 3 step of the encapsulation process, what is the Protocol Data Unit (PDU) called
when the IP stack adds source (sender) and destination (receiver) IP addresses?
Options
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.
Q: 9
Which tool supercharges security operations center (SOC) efficiency with the world’s most
comprehensive operating platform for enterprise security?
Options
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.
Question 1 of 20 · Page 1 / 2

