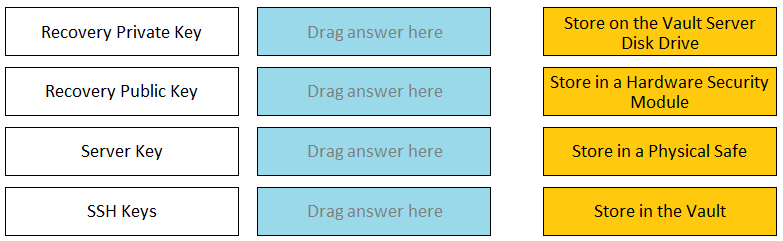
DRAG DROP Match each key to its recommended storage location.
Q: 11
Drag & Drop
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.
Q: 12
When the CPM connects to a database, which interface is most commonly used?
Options
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.
Q: 13
You want to give a newly-created group rights to review security events under the Security pane. You
also want to be able to update the status of these events.
Where must you update the group to allow this?
Options
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.
Q: 14
A Logon Account can be specified in the Master Policy.
Options
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.
Q: 15
Which onboarding method would you use to integrate CyberArk with your accounts provisioning
process?
Options
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.
Q: 16
Which parameter controls how often the CPM looks for Soon-to-be-expired Passwords that need to
be changed.
Options
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.
Q: 17
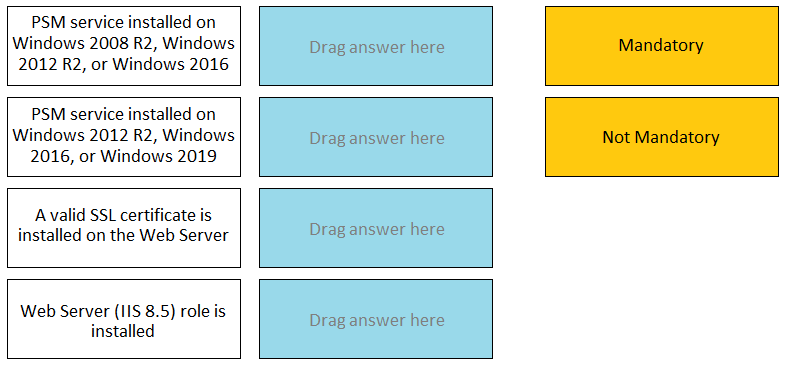
DRAG DROP For each listed prerequisite, identify if it is mandatory or not mandatory to run the PSM Health Check.
Drag & Drop
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.
Q: 18
By default, members of which built-in groups will be able to view and configure Automatic
Remediation and Session Analysis and Response in the PVWA?
Options
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.
Q: 19
When Dual Control is enabled a user must first submit a request in the Password Vault Web Access
(PVWA) and receive approval before being able to launch a secure connection via PSM for Windows
(previously known as RDP Proxy).
Options
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.
Question 11 of 20 · Page 2 / 2