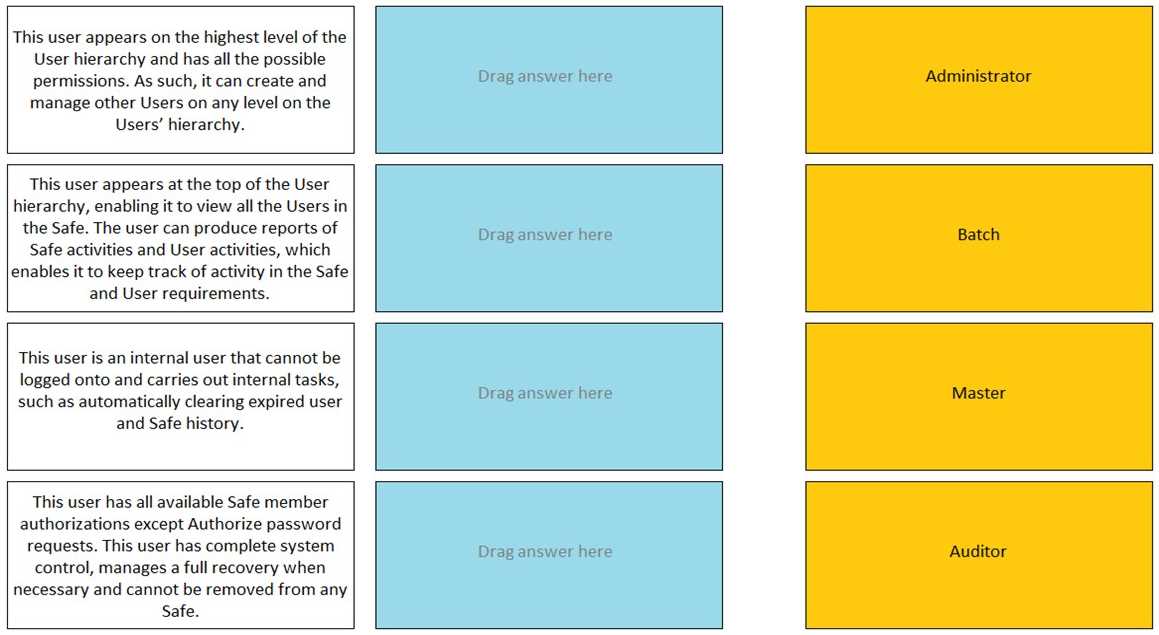
DRAG DROP Match the built-in Vault User with the correct definition.
Q: 1
Drag & Drop
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.
Q: 2
Via Password Vault Web Access (PVWA), a user initiates a PSM connection to the target Linux
machine using RemoteApp. When the client’s machine makes an RDP connection to the PSM server,
which user will be utilized?
Options
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.
Q: 3
As long as you are a member of the Vault Admins group you can grant any permission on any safe.
Options
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.
Q: 4
Which utilities could you use to change debugging levels on the vault without having to restart the
vault. Select all that apply.
Options
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.
Q: 5
Which change could CyberArk make to the REST API that could cause existing scripts to fail?
Options
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.
Q: 6
Can the 'Connect' button be used to initiate an SSH connection, as root, to a Unix system when SSH
access for root is denied?
Options
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.
Q: 7
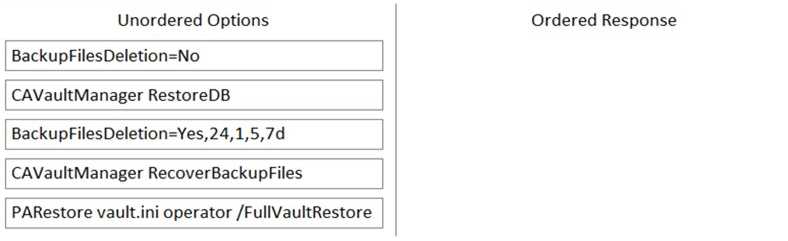
DRAG DROP Arrange the steps to restore a Vault using PARestore for a Backup in the correct sequence.
Drag & Drop
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.
Q: 8
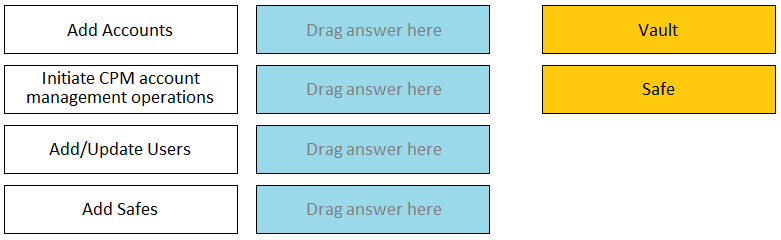
DRAG DROP Match each permission to where it can be found.
Drag & Drop
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.
Q: 9
It is possible to restrict the time of day, or day of week that a [b]reconcile[/b] process can occur
Options
Discussion
No comments yet. Be the first to comment.
Be respectful. No spam.
Question 1 of 20 · Page 1 / 2